Introduction
Application Programming Interfaces (APIs) are the unseen motors that drive our networked environment in the digital age, where technology controls the beat of contemporary life. The foundation of the digital experiences we frequently take for granted is the smooth data exchange and functionality between programs made possible by APIs. But as these unseen links sew our lives’ digital fabric together, they also open us up to fresh, constantly developing security risks. Enter the Top 10 API Security Risks from the Open Web Application Security Project (OWASP), a dynamic compilation that sheds light on the flaws endangering our digital ecosystems.
The Anatomy of APIs
APIs are fundamentally bridges that link various apps and allow them to coexist peacefully. Similar to how a waiter relays your order to the chef at a restaurant, APIs enable communication between different software components by relaying requests and providing results. This speeds up development and encourages creativity by enabling developers to take advantage of already-existing functions rather than having to create them from scratch.
Providing Powerful Digital Experiences
APIs have been crucial in establishing the digital experiences that are now considered standard. Here is how they affect different domains:
E-commerce: APIs coordinate communication between the front end of the website, the inventory database, and the payment gateway when you add an item to your online shopping basket. An easy purchasing experience is made possible by this seamless connection.
Social media: APIs are at work behind the scenes to enable every time you share a post, like a picture, or sign in with your social network credentials on another website.
Mobile Apps: Real-time data from servers, such as weather updates, news articles, or location-based data, is frequently fetched by mobile applications using APIs.
Cloud Services: APIs are largely responsible for the scalability and flexibility of cloud computing. Cloud service providers provide APIs that permit programmatic resource deployment and management by developers.
IoT (Internet of Things): In the realm of smart devices, APIs allow various gadgets and sensors to communicate with one another, forming a networked ecosystem that boosts productivity and ease.
The Engines of Innovation
How APIs democratize invention is among its most impressive features. Through the use of APIs, businesses can make specific functionality available to other developers so they can create complementing software or services. As a result, robust ecosystems have sprung up around platforms like Twitter, Google Maps, and Shopify, where third-party developers add a wide range of tools and features, greatly enhancing the platform’s functionality.
Understanding the Development of API Security Issues
Since their origin, APIs have evolved from straightforward tools for interconnection to the essential building blocks of contemporary software development. The hazards associated with APIs have changed along with them. Because of this shifting environment, the OWASP project frequently updates its list of the most serious risks to API security, giving organizations, security professionals, and developers the information they need to counter potential flaws.
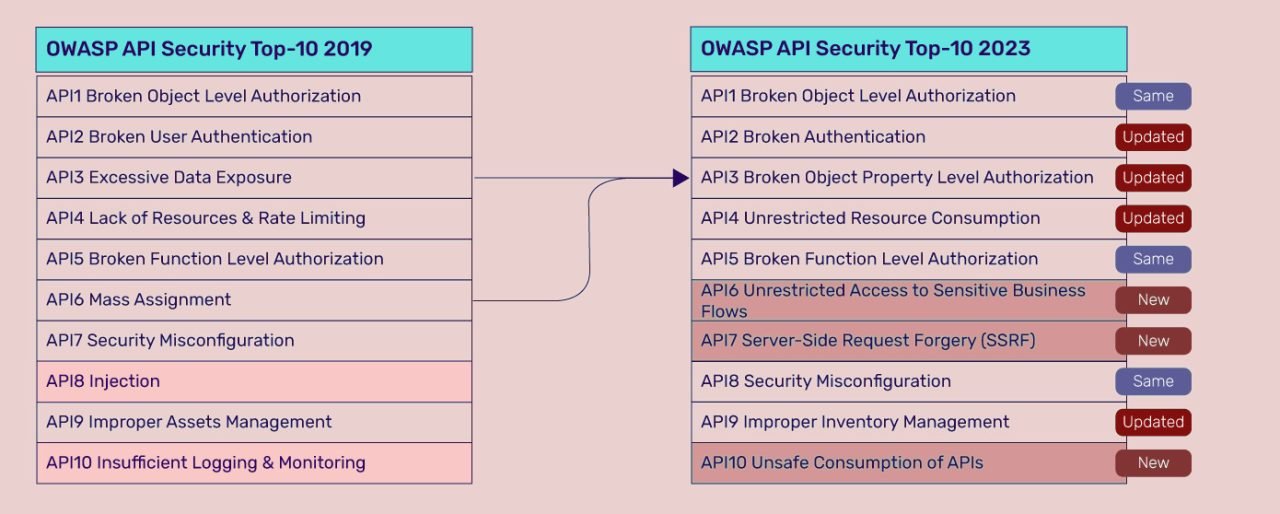
OWASP Top 10 API Security Risks
The most recent iteration of the OWASP Top 10 API Security Risks debuts as 2023 approaches, equipped with observations that reflect the shifting trends in the field of cybersecurity. In this episode, we look at the crucial concerns that have attracted attention:
1. Broken Object Level Authorization :
– Issue: APIs sometimes let attackers access data they shouldn’t.
– Solution: Always check if the user should access that data.
2. Broken Authentication :
– Issue: Sometimes, the way systems check who you are isn’t secure.
– Solution: Make sure only the right people get in.
3. Broken Object Property Level Authorization :
– Issue: Sometimes, parts of data are exposed when they shouldn’t be.
– Solution: Keep your data locked up properly.
4. Unrestricted Resource Consumption :
– Issue: Too many requests can break things or cost a lot of money.
– Solution: Be careful not to overload the system.
5. Broken Function Level Authorization :
– Issue: Sometimes, users can do things they’re not supposed to.
– Solution: Make sure people only do what they’re allowed to.
6. Unrestricted Access to Sensitive Business Flows :
– Issue: Some actions can hurt a business if done too much.
– Solution: Don’t let users do too much too quickly.
7. Server Side Request Forgery :
– Issue: Bad requests can make your system do things it shouldn’t.
– Solution: Check requests carefully.
8. Security Misconfiguration :
– Issue: Sometimes, settings aren’t secure.
– Solution: Keep your system settings safe.
9. Improper Inventory Management :
– Issue: It’s easy to lose track of what your API can do.
– Solution: Keep a good list of what your API can do.
10. Unsafe Consumption of APIs :
– Issue: Sometimes, people trust outside data too much.
– Solution: Be careful with data from other places.
A Forward And Backward Analytical Glance
The OWASP Top 10 API Security Risks – 2023 highlights an ongoing theme in API security concerns when compared to other editions. The principles of vulnerability categories still hold true, albeit they have been honed and modified to encompass modern attack vectors and strategies. This confirms OWASP’s commitment to matching its findings with the constantly changing environment of new threats.
Conclusion
In conclusion, APIs create the fabric of our digital existence while opening the door to numerous security risks. As a compass, The OWASP Top 10 API Security Risks – 2023 navigates the choppy waters of contemporary cybersecurity. Understanding and proactively reducing these risks allows us to build strong barriers against new dangers, promoting a safe and seamless existence for the digital world.