What is Multi-factor authentication (MFA)?
Multi-factor authentication is an identity and access management security method that requires two forms of identification to access resources and data. MFA gives businesses the ability to monitor and help safeguard their most vulnerable information and networks.
Importance of Multi-factor authentication
MFA stands for multi-factor authentication. It is used as an additional layer of security for user accounts. This simply means there will be two factors for you to authenticate into your account. One is simply your credentials, and if due to some case they are compromised the additional layer (second authentication) can protect your account from getting takeover.
Ways to implement Multi-factor authentication
There are many ways to implement MFA such as:
- Sending OTP to email or mobile number: In this method, One-Time Password (OTP) is sent to either the registered email or mobile number for authentication.
- Third-party app-generated codes: In this method, Users utilize authentication apps (e.g., Google Authenticator) to generate time-sensitive codes for login.
- Verification through QR codes: Users scan a QR code with their authentication app to set up a secure connection between the app and the service. For example, while logging in to WhatsApp or Telegram web, we are supposed to scan the QR code displayed on the screen to authenticate and log in.
- Biometric Authentication: In this method, Users authenticate using unique biological traits such as fingerprints, facial recognition, or iris scans. For example, devices like smartphones and laptops utilize face IDs and fingerprint scanners to authenticate the user and unlock the device.
- Push Notifications: In this method, Users receive a push notification on their mobile device, prompting them to approve or deny access. For example, when you log in to your Google account on a new device, a push notification is sent where you must tap a certain number to grant login access.
Bypassing Multi-factor Authentication: Risks and Techniques
Direct Request/Forceful Browsing
This issue happens when the application lacks authorization checks or doesn’t properly implement them. Suppose the application has the following workflow:
- The user navigates to target.com/login and enters the login credentials.
- The application redirects the user to the target.com/mfa page and asks to provide OTP.
- Now, when the user provides a valid OTP, the user is redirected to the target.com/my-account page and can access other parts of the application as well.
Now, if the application is having improper authorization checks, the attacker user would be able to perform the following:
- The user navigates to target.com/login and enters the login credentials.
- The application redirects the user to the target.com/mfa page and asks to provide OTP.
- Now, instead of providing the OTP, the user directly navigates to target.com/my-account and if the user can access the /my-account page, the MFA requirement is bypassed.
Flawed two-factor verification logic
Sometimes flawed logic in two-factor authentication means that after a user has completed the initial login step, the website doesn’t adequately verify that the same user is completing the second step.
For Example:
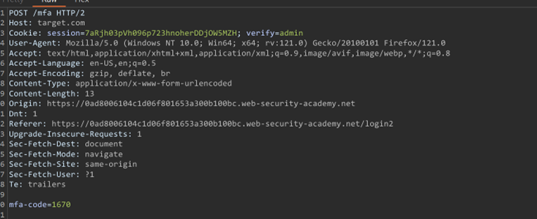
The user logs in simply using a username and password.
Now, when asked for OTP, you will notice a hidden parameter that contains the username. So, the attacker can change the username to admin and access the admin’s account.
Missing Brute-Force Protection on OTP Validation
Due to a lack of throttling and missing rate limiting/brute-force protection, it is possible to perform the following (not limited to these) attacks. Suppose there is a login page that asks for a mobile number and then uses OTP for logging in. In that case, we can:
- Enter the Victim’s mobile number and request OTP.
- Intercept the request while entering the wrong OTP and send the request to an intruder to brute force the right OTP.
In similar cases, we can get account takeovers.
OTP Code Reusability
When the application doesn’t invalidate a previously used OTP and the expiration timeframe is considerable say 1 day. It can be abused by an attacker to brute-force and can lead to account takeover.
HTTP Response Body Manipulation
Response manipulation is a technique where attackers make changes in the response before it reaches the browser. With the help of response manipulation, sometimes you can bypass 2FA or Authentication and many more things.
For example:
Suppose in Request and Response, there is only a single difference over there while comparing with right & wrong OTP responses.
if you enter the wrong OTP then in the response you will get
(“ success”: false, “message”: “otp-mismatch”)
and if you enter the right OTP then in the response you will get
(“ success”: true, ”paytmno”:”1234567890″)
In this case, what the attacker can do is, manipulate the response with the response he gets when entering the right OTP.
Missing Integrity Checks on OTP
In this case, what happens is that the application just checks for a valid OTP but doesn’t check valid for which user. This is a critical vulnerability and can be used for account takeover using the following steps:
- Attacker requests OTP for his own account A
- Now, he uses the OTP to log in to the victim’s account. Since the application isn’t verifying for which user the OTP is valid and just checks if the OTP is valid or not, this can lead to the attacker getting logged into the victim’s account.
What’s the Impact?
Bypassing Multi-factor authentication can lead to serious security issues for a company or an individual.
Using MFA bypass methods, one can gain unauthorized access to someone’s account which can eventually lead to data breaches and financial loss. Bypassing MFA increases the risk of identity theft. Attackers may impersonate users, create fraudulent accounts, or use compromised credentials for malicious activities. Organizations that experience MFA bypass incidents may suffer reputational damage. Users and clients may lose trust in the security measures implemented by the entity, affecting its credibility.
Best practices for MFA implementation
- Educate Users: Provide clear and concise information to users about the importance of MFA and how to use it securely. Offer training on recognizing and avoiding phishing attempts, as social engineering attacks are common methods to bypass Multi-factor authentication.
- Encourage Biometric Authentication: Where applicable, encourage the use of biometric factors (fingerprint, facial recognition) as they provide a convenient and secure method of authentication.
- Implement Time-Sensitive Codes: Ensure that one-time codes generated by MFA are time-sensitive and have a short validity period. This reduces the risk of attackers using intercepted codes and brute-forcing codes.
- Regularly Update Software and Firmware: Keep authentication devices, software, and firmware up to date to address vulnerabilities and enhance overall security.
- Regular Security Audits and Assessments: Conduct regular security audits and assessments to identify vulnerabilities and ensure that the Multi-factor authentication system remains resilient against emerging threats.
Conclusion
Multi-factor authentication cannot guarantee fullproof security or stop all cyberattacks. However, it can help protect high-value systems and accounts, secure email access, and limit the usefulness of stolen credentials. Most importantly, MFA adds additional layers of authentication to protect systems and combat many types of cyberattacks.