Introduction
Learn about insecure deserialization, a critical cybersecurity concern. In the digital age, data storage and transmission are fundamental aspects of software development. One key process that facilitates these tasks is Deserialization. While deserialization plays a crucial role in handling data, it also introduces significant security risks. This blog post delves into the concept of insecure deserialization, exploring why it is a critical concern in cybersecurity.
Understanding Serialization and Deserialization
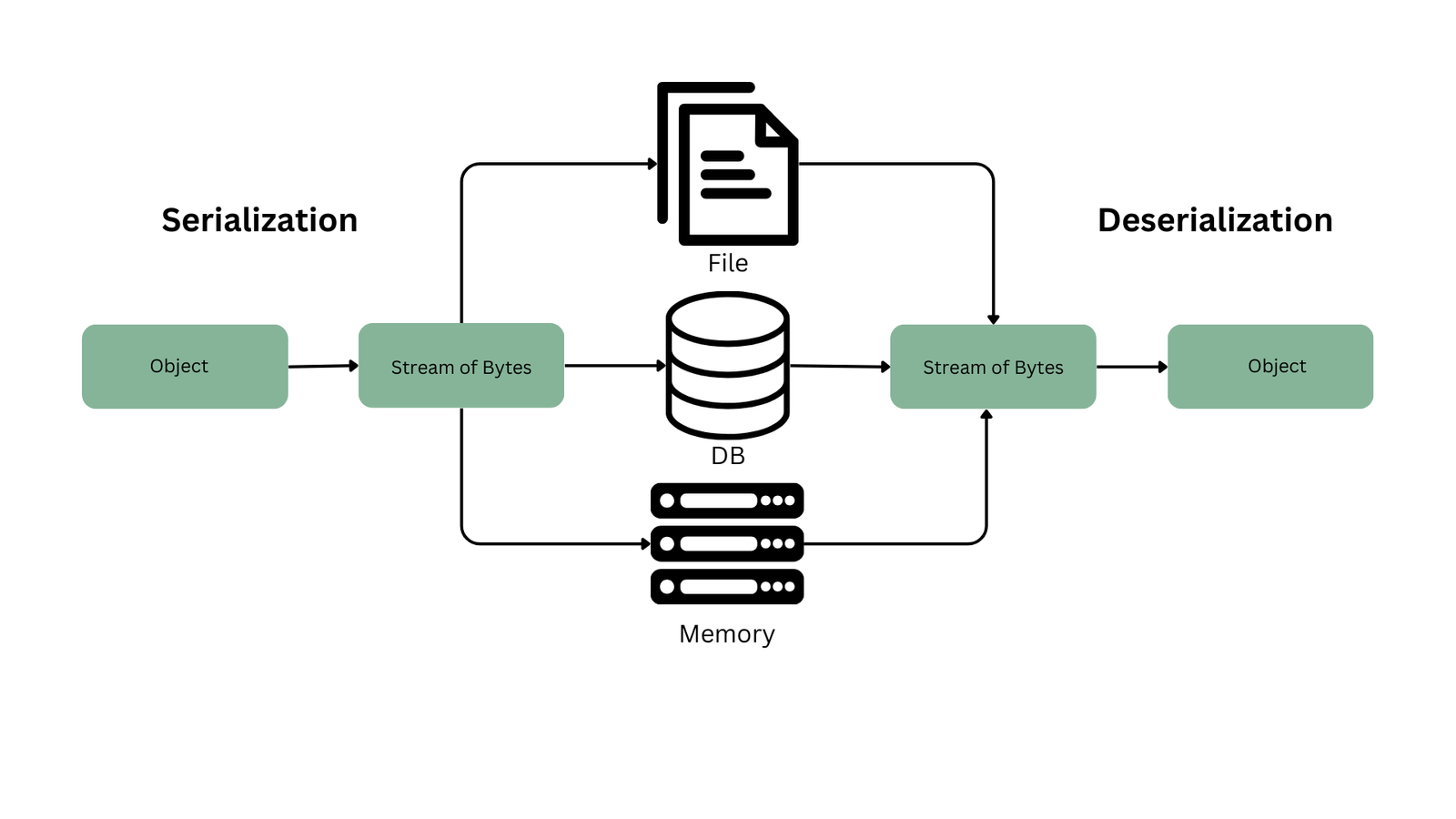
Serialization
The process of serializing an entity involves converting its state, or its data and structure, into a format that is easily shared, saved, and sent. The serialized data that is produced can be in binary, XML, or JSON forms. Serialization is useful in a number of situations:
- Data persistence: It is the process of storing an object’s state or information in a file or database so that it can be retrieved when needed and saved for later use. This frequently entails transforming the item into a format that is simple to store and then reconstruct, such serializing user profiles for database storage.
- Data transmission: It is the process of effectively sending and receiving information over networks so that it is reliably delivered from one location to another. In order to make it easier for data to be transferred across various systems and to be rebuilt at the receiving end, this is frequently utilized in APIs and web services.
- Microservices Communication: The method of allowing smooth data transfer in a microservices architecture between various services. It entails setting up systems for efficient communication amongst several microservices to facilitate them cooperation in carrying out designated functionalities. To guarantee dependable and effective data transmission between services, this involves utilizing techniques like message queues, REST APIs, or event-driven architectures.
Deserialization
Deserialization is the process of converting serialized data back into its original object form. It is the opposite of serialization. It’s important to note that deserialization typically works with the same formats used for serialization, such as JSON and XML. Rebuilding the object with its original attributes and configuration is necessary when you get serialized data, as from a file or a network request.API
- Security Concerns: To avoid security flaws, it’s crucial to handle external data carefully while interpreting it. Input from several sources, such as human input, APIs, or data from other systems, might be included in the category of external data. This external data can be abused to run malicious code or jeopardize the security of the program if it is not handled carefully. To https://shorturl.at/pDH5Areduce these security threats, sanitization, secure coding techniques, and appropriate input validation are crucial.
- Data Integrity: Inconsistencies between the deserialized data and the original object might lead to application failures, which can be avoided by ensuring data integrity during deserialization. Validating and confirming the data’s integrity after deserialization is crucial to making sure that it wasn’t altered or corrupted during serialization. To do this, methods like digital signatures, checksums, or hash functions are used to confirm the integrity and validity of the deserialized data.
- Version Compatibility: Because there may be changes to the object structure, maintaining version compatibility can be difficult, especially when moving from an earlier version of an object to a newer version. Changes to the object’s attributes or structure can cause compatibility problems during deserialization, therefore this is especially important when working with serialized data. In order to properly address these issues and guarantee a seamless transition between various versions of the object, strategies like versioning, backward compatibility, and data migration approaches are needed.
Insecure deserialization occurs when untrusted data is used to abuse the logic of an application, leading to unexpected behaviour or security breaches. This vulnerability can arise in various scenarios, such as when handling user input or inter-service communication. Deserialization can be exploited when an attacker crafts malicious input to manipulate the deserialization process.
Common Vulnerabilities and Mitigations
Various vulnerabilities in software systems can result from unsecured deserialization and serialization. The following are some major vulnerabilities that can occur from insecure deserialization and serialization.
Vulnerabilities:
- Remote Code execution (RCE): When an attacker manipulates serialized data to allow them to run arbitrary code on the server, this is known as remote code execution.
- Authentication Bypass : To get around authentication systems, attackers can alter serialized objects. For example, if a user’s session is serialized and saved in cookies, an attacker can alter the session object to alter the user’s rights.
- Privilege Escalation: By altering serialized data, attackers might increase their level of privilege within an application and obtain access to features that are blocked.
# Python example with pickle
user = User(‘attacker’, ‘user’) serialized_user = pickle.dumps(user) modified_user = serialized_user.replace(b’user’, b’admin’)
- Data Tempering: Data that has been serialized can be changed, which could lead to illegal changes or corrupted data in an application. For example, tampering with serialized data in transit could allow an attacker to modify important information.
// JSON example with tampered data
{ “username”: “attacker”, “balance”: 1000000 }
- Denial of Service (DOS): Intentionally manipulating serialized data can drain system resources and cause a denial of service, where the application crashes or becomes unresponsive. An attacker could, for example, send through an unnecessarily huge and complexly constructed object, which uses a lot of server resources when it comes to deserialization and eventually affects the availability and performance of the application.
String serializedTransaction = “rO0ABXNyAC5jb20uZXhhbXBsZS5UcmFuc2FjdGlvbgAAAAAAAAAAAQIAAHhyAA1qYXZhLmxhbmcuT2JqZWN0AAAAAAAAAAAAAAECAAB4cA==”;
- Injection Attacks: Malicious code can be injected by serialized data manipulation, including through exploitations like SQL, LDAP, or other similar injection techniques. An attacker might alter a serialized object, for example, with the goal of carrying out a SQL injection attack.
// PHP example with SQL injection
$serializedData = ‘O:8:”stdClass”:2:{s:4:”name”;s:5:”admin”;s:7:”isAdmin”;s:16:”1’ OR ‘1’=’1″;}’; $object = unserialize($serializedData);
- Cross-Site Scripting (XSS): XSS (Cross-Site Scripting) attacks are made possible when serialized data is shown on webpages without first completing sufficient sanitization procedures.
- Cross-Site Request Forgery(CSRF): Unauthorized operations can be carried out on behalf of authenticated users without their agreement by using serialized data to create fake requests. To change a user’s password, for example, an attacker could submit a serialized request object.
<!– XML example with CSRF –>
<request>
<action>changePassword</action>
<newPassword>attacker123</newPassword>
</request>
- Information Disclosure: Improper handling of serialized data can pose a significant risk, potentially resulting in the inadvertent exposure of sensitive information, including credentials, configuration details, or other critical data. In a scenario where an attacker successfully deserializes an object containing sensitive configuration details, the repercussions can be severe. This could lead to the unauthorized access and extraction of critical information.
Mitigations:
- Least Privilege Principle: Limit the permissions of deserialized objects to minimize impact.
- Use Secure Libraries and Frameworks: Prefer libraries and frameworks that are designed to handle serialization and deserialization securely.
- Validate and Sanitize Input: Always validate and sanitize serialized data before deserializing it.
- Implement Whitelisting: Use whitelisting to allow only specific classes to be deserialized.
- Use Non-Executable Formats: Prefer using non-executable data formats such as JSON or XML instead of binary formats that can execute code.
- Cryptographic Integrity Checks: Implement cryptographic integrity checks (e.g., digital signatures) to ensure data has not been tampered with.
- Limit Exposure: Minimize the exposure of deserialization endpoints to untrusted sources.
- Regular Security Audits: Perform regular security audits and code reviews to identify and fix potential vulnerabilities.
Conclusion
Insecure deserialization is a critical cybersecurity issue that both developers and security specialists need to be aware of. In contemporary software development, serialization and deserialization are fundamental processes that enable data storage, transport, and inter-service communication. Nevertheless, programs may become subject to dangerous problems like privilege escalation, remote code execution, and authentication bypass if deserialization is not done securely.
It is essential to follow best practices and have strong security measures in place to reduce these dangers. Using secure libraries and frameworks, input validation and sanitization, whitelisting, the least privilege principle, and favoring non-executable data types are a few examples of this.
Developers can safeguard their applications from the risks associated with unsafe deserialization by implementing these precautions.




