Introduction
Malware analysis is playing a crucial role for safeguarding the digital landscape, guarding individuals, businesses, and governments alike. As ransomware locks down critical systems to spyware silently siphoning sensitive information, the impact of malware is both far-reaching and potentially devastating. This blog aims to demystify the concept of malware, delve into its evolution, and underscore the vital role of malware analysis in combating these threats. We will also explore how automation is revolutionizing the field, enabling faster and more accurate detection and analysis of malicious software.
What is Malware?
Malware, an acronym for “malicious software,” is any software that is intentionally created to harm a computer, server, client, or computer network. Equivalent to a chameleon that can change its shape to suit its surroundings and goals. Here is a closer examination of its different forms:
- Viruses: The traditional cause of problems. Viruses cling to authentic files and spread when those files are run, much like the contagious flu. They may cause data corruption, system slowdown, or even system failure.
- Worms: Think about worms tunneling across your virtual landscape. Worms are intelligent, self-replicating, networked organisms. They spread throughout systems by taking advantage of weaknesses, wreaking havoc all around.
- Trojans: Trojans, so named for the notorious wooden horse of Greek mythology, pose as innocuous software. Once inside, they unleash their payload, which may include initiating assaults, building backdoors, or stealing data.
- Ransomware: The thief of the digital highway. Your data are encrypted by ransomware, which then demands a large fee to unlock the keys. Repay or forfeit your priceless data permanently.
- Spyware: The sly neighbor of the digital world is spyware. Spyware quietly records everything you do, including your keystrokes and surfing patterns, and sends the data it collects back to its author.
Technology evolve new strains of malware continue to emerge, presenting significant challenges to cybersecurity efforts. For instance, the proliferation of IoT malware poses a threat to the expanding array of IoT devices, exploiting their often-limited security measures.
Furthermore, the emergence of fileless malware poses a distinct challenge to conventional detection and mitigation techniques because it functions solely in system memory and leaves no record on the disk. In addition, the incorporation of AI into malware adds another level of complexity, making attacks more effective and able to adapt dynamically. This highlights the necessity of improved cybersecurity solutions to counteract these more complex threats.
Hackers are always changing their strategies to increase the impact of their assaults. One such approach is RaaS, which makes destructive operations easier by giving less experienced users access to tools and services. AI-enhanced malware compounds this difficulty by eluding detection systems. Supply chain attacks and targeted phishing campaigns, on the other hand, take advantage of flaws in software supply chains and use individualized data to create enticing lures. All of these developments underscore the vital significance of strong cybersecurity defenses at all levels.
Impacts of Malware
Although a wide variety of targets are frequently the focus of malware, some popular targets are especially alluring because of their relative weakness, potential for significant damage, or rich data. The use of malware and phishing techniques can result in fraud, identity theft, and unauthorized access to private information. Businesses that hit by malware attacks face the risk of experiencing severe consequences, such as lower sales, disruptions in daily operations, and damage to their brand. Especially, ransomware can cause a system to crash, causing a great deal of downtime and possibly financial loss. Data breaches may result in the exposure of private client information, exposing businesses to fines and reputational damage.
Currently, hackers are becoming more frequent they target for critical infrastructure, including electricity grids, transportation networks, and healthcare systems. Threats to our national security and public safety they might arise from malware that interferes with vital services. Because infrastructure systems are frequently antiquated and lack strong cybersecurity safeguards, there is growing concern in 2024 about cyberattacks on these systems. Malware is currently being used for espionage and sabotage purposes. State-sponsored organizations utilize sophisticated malware to sabotage government operations, steal classified information, and affect political processes.
Importance of Malware Analysis
The practice of looking at harmful software to determine its intentions, behavior, and possible effects is known as malware analysis. It’s an essential part of cybersecurity that aids in defending people and businesses against online dangers.
- Understanding Threats: Cybersecurity experts can determine a piece of malware’s capabilities, including what data it targets, how it spreads, and what harm it can inflict, by using malware analysis. Developing successful defenses and response plans requires this understanding. Malware is a digital predator, not merely a collection of code. What analysts find is as follows:
- Behavioral Patterns: Malware designed for industrial targets may exhibit behaviors aimed at disrupting critical infrastructure. This could include efforts to manipulate industrial control systems, steal sensitive intellectual property, or disrupt production processes. Analysts dissect the behavior of such malware to understand its specific motives and potential impact on industrial operations.
- Propagation Mechanisms: Malware targeting industrial systems may exploit vulnerabilities in industrial control software, machinery, or network protocols. It might also be designed to exploit weaknesses in specific industrial communication protocols, piggyback on seemingly innocuous files used in industrial processes, or use social engineering tactics to gain access to critical systems.
- Payloads and Triggers: The payloads carried by industrial-targeted malware may be tailored to cause significant harm to industrial processes, such as disrupting manufacturing lines, altering production parameters, or causing physical damage to equipment. Additionally, triggers for these payloads could be tied to specific industrial system events or production schedules, enabling the malware to cause maximum impact at strategic times.
- Prevention and Mitigations: Security professionals use specific methodologies to create defensive measures that are suited to the difficulties faced by industrial environments when it comes to protecting industrial systems against malware.
- Signatures: Based on the unique traits of threats that target operational technology and industrial control systems, security researchers develop signatures for malware. These could be particular lines of code, communication styles, or actions that point to nefarious conduct. These signatures are then included in intrusion detection systems and antivirus software to effectively identify and stop recognized industrial threats.
- Behavioral Indicators: Industrial-focused malware often exhibits suspicious behaviors within operational technology environments, much like an unwelcome presence in a secure facility. Analysts meticulously identify these patterns, such as anomalous network traffic, unauthorized alterations to control system configurations, or unexpected interactions with industrial equipment. These behavioral indicators serve as red flags, enabling security tools to uncover and neutralize malware threats in industrial settings.
- Heuristics and Machine Learning: Within industrial cybersecurity, heuristics and machine learning play a crucial role in identifying potential threats. These advanced capabilities enable security tools to continuously learn and adapt based on the behaviors and characteristics of malware encountered in industrial environments. By employing smart guessing and learning from past encounters, these tools can effectively raise alarms and mitigate never-before-seen threats, even when they exhibit unfamiliar patterns or behaviors.
- Incident Response: In the event of a cyber-attack, thorough malware analysis is essential for effective incident response. It plays a pivotal role in determining the scope of the breach, understanding the attack vector, and formulating a strategic plan to contain the threat and restore affected systems. A swift and accurate analysis can significantly mitigate the impact of an attack and facilitate a more efficient recovery process.
- Scope Assessment: Malware analysis begins with a comprehensive assessment to establish the extent of the infection and identify the systems that have been compromised. Security analysts meticulously map out the battlefield, determining the reach of the malware within the network, potential points of entry, and any lateral movement the malware may have executed. This assessment provides crucial insights into the scale of the incident and guides subsequent response efforts.
- Root Cause Analysis: Understanding how the malware infiltrated the network is a critical aspect of incident response. Analysts conduct a thorough root cause analysis to uncover the entry point of the malware—whether it was introduced through a phishing email, exploited a vulnerability in a plugin, or leveraged social engineering tactics to gain access. Identifying the initial intrusion vector is imperative for implementing targeted security measures and preventing similar breaches in the future.
- Containment and Eradication: Once the scope and root cause of the attack are understood, the focus shifts to containment and eradication. Analysts isolate the affected systems to prevent the further spread of the malware, remove the malicious code, and meticulously cleanse the impacted systems to eliminate any remnants of the malware. This process is akin to fumigating a haunted house, where every corner is thoroughly inspected and cleansed to ensure a full eradication of the threat.
- Legal and Regulatory Compliance: Particularly in sectors where strict data protection rules and regulations apply, malware analysis plays a critical role in guaranteeing adherence to legal and regulatory standards. Maintaining compliance, safeguarding data privacy, and averting legal ramifications all depend on having a solid understanding of how malware can compromise sensitive information.
- Data Protection Laws: Regulations such as the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA), and the Health Insurance Portability and Accountability Act (HIPAA) impose strict requirements for safeguarding sensitive information. Malware poses a significant threat to data privacy and security. Compliance with these laws necessitates a deep understanding of the regulations, along with robust cybersecurity measures to secure sensitive data from malicious attacks, including malware incursions.
- Incident Reporting: Certain regulations mandate organizations to promptly report data breaches to relevant authorities and affected individuals. Malware analysis plays a pivotal role in incident response by providing crucial insights into the nature of the breach, the impact on data privacy, and the actions taken to mitigate the incident. Detailed malware analysis helps organizations create an evidence trail that can be used for compliance reporting and incident documentation as required by regulatory frameworks.
- Forensics for Courtrooms: In the unfortunate event of legal disputes or regulatory investigations stemming from a data breach or cybersecurity incident, malware analysis assumes the role of digital forensics. Just like a cyber edition of CSI (Crime Scene Investigation), malware analysis helps uncover the origin of the attack, the tactics employed by threat actors, and the extent of the damage caused. This forensic analysis of malware-related incidents provides essential evidence that can be presented in legal proceedings, regulatory inquiries, or compliance audits.
Cybersecurity experts can look at the actions, and the possible effects of malicious software to create focused defense, strengthen systems against new threats, and react quickly to intrusions. By developing special preventive measures putting into practice an efficient incident response plan, and keeping a close eye on potential threats, organizations may reduce the risks associated with malware and protect their critical information and confidential data. Beyond its technical uses, malware analysis has legal and regulatory compliance applications as well. It does this by making sure that strict data protection regulations are followed, expediting the incident reporting procedure, and offering vital proof for legal or regulatory actions.
Methods of Malware Analysis
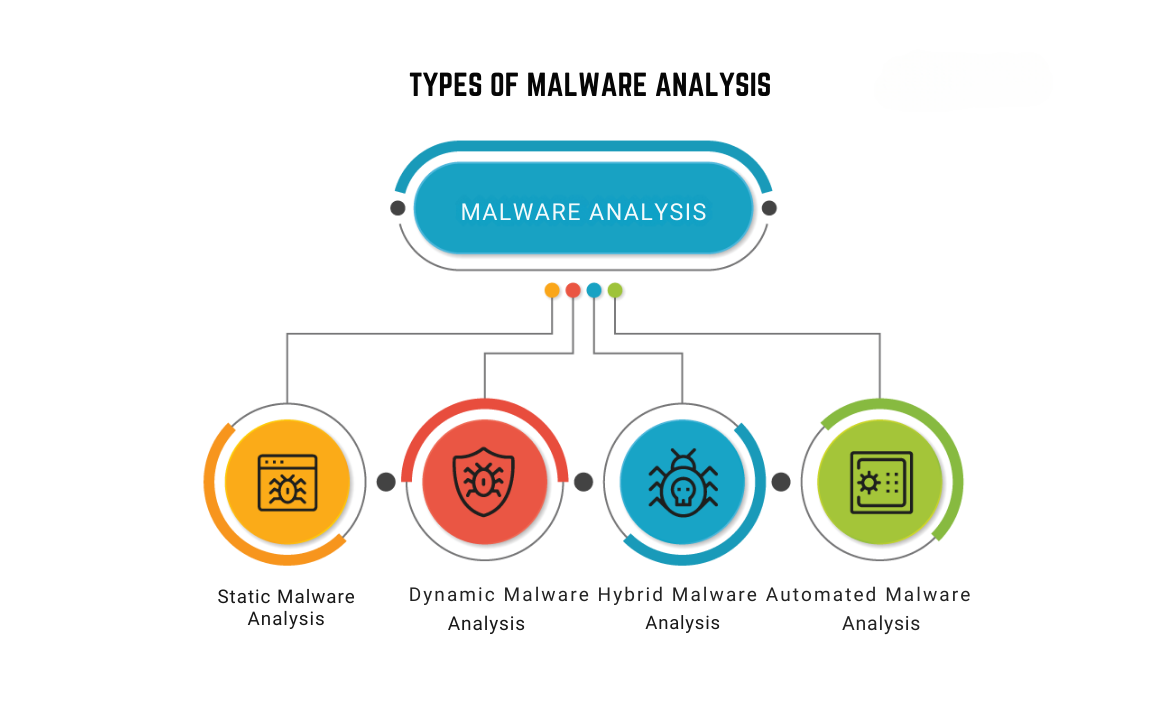
Malware analysis is crucial in cybersecurity, allowing professionals to understand the motivations, behaviors, and potential ramifications of malicious software. This understanding is pivotal for crafting effective defenses and developing responsive strategies.
- Static Analysis: Static analysis involves examining the malware without executing it. This method is useful for understanding the structure and components of the malware. Static analysis can reveal details such as file type, embedded resources, and potential entry points. However, it has limitations, particularly when dealing with obfuscated or encrypted malware.
- Dynamic Analysis: Dynamic analysis involves executing the malware in a controlled environment, such as a sandbox, to observe its behavior. Dynamic analysis provides insights into the malware’s runtime behavior, such as which files it modifies, what registry keys it accesses, and whether it communicates with external servers. This method is particularly useful for detecting actions that are not evident in static analysis.
- Hybrid Analysis: Hybrid analysis combines static and dynamic techniques to provide a comprehensive understanding of malware. By leveraging both approaches, analysts can overcome the limitations of each and gain a more complete picture of the malware’s capabilities and intentions.
- Automated Analysis: Automation can handle repetitive tasks, such as extracting and analyzing strings, calculating hash values, and generating reports, freeing up human analysts for more complex tasks.
Popular Tools and Techniques
A wide range of tools and techniques are employed in malware analysis. Some of the most popular ones include:
- Disassemblers and Decompilers: Tools like IDA Pro, Ghidra, and Radare2 help analysts examine the binary code of malware, translating it into a more human-readable format.
- Debuggers: Debuggers such as OllyDbg, x64dbg, and WinDbg are crucial for dynamic analysis.
- Sandboxes: Popular sandboxing tools include Cuckoo Sandbox, Joe Sandbox, and FireEye’s FLARE VM.
- Network Analysis Tools: Wireshark and tcpdump are popular tools for capturing and analyzing malware-generated network traffic
- Behavioral Analysis Tools: Tools like Sysinternals Suite and Process Monitor can track and log changes made by the malware to system files, registry entries, and processes, providing valuable insights into the malware’s behavior.
- Antivirus and Threat Intelligence Platforms: Solutions like VirusTotal and Malwarebytes can help identify known malware samples and provide context to an analyst’s investigation, including information about the malware’s capabilities, distribution methods, and threat actors involved.
Conclusion
Malware is a growing concern in 2024, affecting not just individuals but also businesses, key infrastructure, and even national security, as we traverse the complex digital terrain. Robust malware analysis is crucial because of the rising complexity and diversity of malware as well as our growing reliance on digital systems. The way we identify, comprehend, and counteract these dangers has changed dramatically as a result of the combination of automation and artificial intelligence with static and dynamic analysis techniques.
But the battle against cyber threats is never-ending; it calls for continual awareness, flexibility, and ingenuity. Cybersecurity enthusiasts and professionals alike must keep up with the most recent advancements in malware strategies and analysis methods. It is now imperative to invest in cybersecurity protection for everything from personal devices to organizational infrastructure. Continuing education is essential for keeping a strong defense against changing threats. This can be achieved through workshops, certifications, and remaining current with industry trends.
We all have a role to play in securing our digital future. Whether you’re a seasoned professional or a tech enthusiast, your efforts in enhancing cybersecurity awareness and practices can make a significant difference. Together, we can build a safer digital world, resilient against the ever-evolving threats posed by malicious software. In the face of these obstacles, let’s pledge to keep learning, growing, and innovating. Cybersecurity’s future rests on our combined watchfulness and preventative actions. Continue to learn about cybersecurity, keep safe, and stay informed.
Our LinkedIn: https://www.linkedin.com/company/aspiainfotech/mycompany/




