Learn how DevSecOps ensures quicker, safer releases by seamlessly integrating security into the software lifecycle, from development to deployment. Security is now an essential component of software development and cannot be ignored in the quickly changing field. Organizations are being forced to reconsider how they incorporate security into their operations due to the increase in cyberthreats, breaches, and sophisticated assaults. Let me introduce you to DevSecOps, an approach that integrates security throughout the entire development and operations lifecycle. DevSecOps makes sure security is an essential component of the entire process, as opposed to introducing it as a last-minute check before release.
Why DevSecOps?
It is simply insufficient to rely on traditional security measures given the increasing complexity and speed of software development. This is addressed by DevSecOps, which smoothly incorporates security into the DevOps workflow. What was the outcome? a system where security is the duty of all teams, including operations, testing, and development.
But why is this shift so important?
- Adapting to Modern Development: Traditional models often treat security as a separate step. DevSecOps embeds security practices early, aligning with today’s agile and rapid-release cycles.
- Speed and Security: DevOps is all about speed, but that speed shouldn’t come at the cost of security. By incorporating security checks throughout the process, teams can release software faster without compromising on protection.
- Early Detection of Vulnerabilities: The sooner you spot a security issue, the cheaper and easier it is to fix. DevSecOps reduces risks by identifying and addressing potential vulnerabilities during development rather than after deployment.
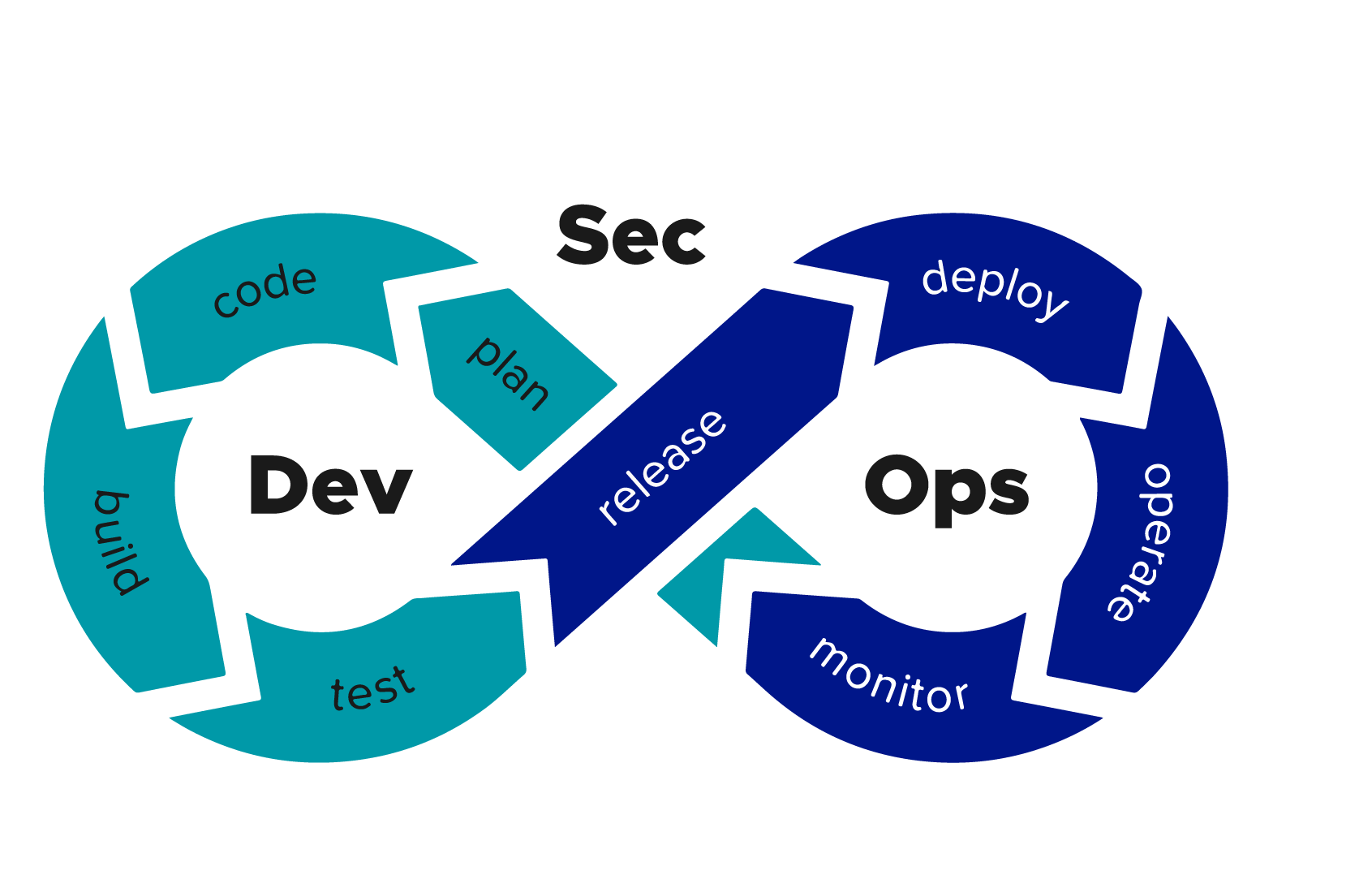
What Exactly is DevSecOps?
Consider DevSecOps to be a security-integrated version of DevOps. DevSecOps incorporates security procedures into the mix, whereas DevOps concentrates on fostering cooperation between development and operations for faster releases. By identifying and mitigating potential risks early on, this method lowers the chance that expensive breaches or vulnerabilities may go unnoticed.
The Importance of DevSecOps
- Establishing a Collaborative Culture: Development, Security, and Operations teams no longer operate in conventional silos thanks to DevSecOps. By encouraging teamwork, everyone is working toward the same objective—delivering dependable, secure software.
- Faster Response to Threats: Vulnerabilities are found and fixed instantly when security is integrated into the CI/CD workflow. Attackers have a smaller window of opportunity thanks to this prompt response.
- Continuous Security Testing: Automated security testing is continuously integrated to make sure that security is built into every build, to identify vulnerabilities early on and keep them from growing into more serious concerns down the road.
The DevSecOps Toolbox
DevSecOps strategies that are effective rely on a blend of methods, resources, and cultural shifts. Instead of going into detail on how to utilize these tools in this blog, we’ll walk you through the process of selecting the best ones for your DevSecOps project. Since each tool has a distinct set of capabilities that can be customized to meet the demands of your organization, choosing the appropriate one is essential. Let’s examine some essential elements and emphasize what makes some tools unique.
Shift-Left Security
The focus of shift-left security is on resolving security concerns as early in the development cycle as feasible. This proactive strategy guarantees your code is secure from the beginning and helps avoid expensive fixes later on.
Key Techniques and Tools:
- Static Application Security Testing (SAST): Source code is analyzed by SAST tools to find vulnerabilities before it is even run. These solutions give developers real-time feedback while they code by integrating directly into development environments (IDEs).
- Software Composition Analysis (SCA): SCA tools scan your open-source components and dependencies to identify known vulnerabilities in third-party libraries.
- Snyk excels in providing real-time alerts and actionable fixes directly within your development workflow, while WhiteSource offers in-depth risk analysis for open-source projects. Black Duck by Synopsys is widely recognized for its robust vulnerability database and comprehensive policy management.
- Integrated Development Environment (IDE) Plugins: IDE security plugins can provide developers with real-time feedback as they create code.In addition to evaluating the quality of the code, Codacy flags possible security flaws in your IDE. With GitHub’s CodeQL, which is made for exact code queries, developers can quickly find and fix particular problems in their codebase.
Automation and CI/CD Integration
Automation is the backbone of DevSecOps, ensuring security checks are consistent and scalable. The key is to integrate security seamlessly into your CI/CD pipelines without slowing down development.
Key Techniques and Tools:
- CI Tools with Built-In Security: Continuous Integration (CI) tools automate building, testing, and integrating code changes while performing security scans.
- Jenkins is popular for its extensive plugin ecosystem, which includes a variety of security testing tools. GitLab CI stands out for offering end-to-end DevSecOps capabilities, from version control to automated security testing in a single platform. CircleCI provides fast and efficient builds with easy integrations for security checks.
- Dynamic Application Security Testing (DAST): DAST tools test running applications by simulating attacks, identifying vulnerabilities that can be exploited in production.
- OWASP ZAP is a go-to for open-source enthusiasts, offering comprehensive scanning capabilities with active community support. BurpSuite is preferred by many professionals for its advanced manual testing features, while Acunetix is lauded for its automated, high-accuracy scanning those scales easily.
- Infrastructure as Code (IaC) Scanning: As infrastructure is increasingly defined through code, IaC scanning tools help ensure secure configurations before deployment.
- Checkov is an open-source tool that integrates smoothly into CI pipelines and supports a wide array of IaC frameworks. Terraform Sentinel is ideal if you’re already using Terraform, offering policy-as-code to enforce compliance. Bridgecrew offers full cloud-native security, combining IaC scanning with runtime monitoring and remediation.
Continuous Monitoring and Incident Response
Even with strong preventive measures, real-time monitoring and quick response capabilities are vital to managing potential security incidents effectively.
Key Techniques and Tools:
- Security Information and Event Management (SIEM): SIEM tools gather and analyse logs from your environment to detect threats and trigger alerts.
- Splunk is known for its powerful search and analytics capabilities, making it suitable for large-scale operations. The ELK Stack (Elasticsearch, Logstash, Kibana) is popular for those preferring open-source solutions, offering customizable log management and visualization. IBM QRadar stands out for advanced threat intelligence integration, providing deeper insights into potential incidents.
- Intrusion Detection and Prevention Systems (IDPS): These tools monitor network traffic and system activities, flagging suspicious behaviour that could indicate an attack.
- Snort is a leading open-source tool with a huge community, making it accessible and customizable. Suricata offers advanced multi-threading, making it faster in high-traffic environments, while OSSEC is praised for its host-based intrusion detection capabilities, making it versatile across different environments.
- Compliance Monitoring: Continuous checks ensure that your systems meet regulatory standards, reducing the risk of compliance breaches.
- AWS Config is a natural choice for those in the AWS ecosystem, continuously auditing your configurations for policy violations. Azure Policy does the same within the Microsoft Azure environment, offering a broad range of built-in policies. Chef InSpec is an open-source framework that offers flexible, code-driven compliance checks across multi-cloud environments.
Culture and Training
Tools and automation are essential, but the success of DevSecOps also hinges on fostering a culture of shared responsibility and continuous learning.
Strategies to Implement:
- Security Awareness Training: Regular training keeps everyone informed about the latest threats and best practices.
- Secure Code Warrior provides gamified training that’s engaging and tailored to different skill levels. HackEDU focuses on hands-on labs, allowing developers to practice real-world scenarios. KnowBe4 is renowned for its phishing simulations and compliance-focused training modules.
- Gamified Learning and Capture the Flag (CTF) Exercises: Simulated attack scenarios encourage hands-on learning and foster collaboration.
- CTFd offers customizable CTF platforms for companies and teams, while PicoCTF focuses on educational challenges suitable for all levels, from beginners to professionals.
- Security Champions: Appointing security advocates within teams helps ensure that security best practices are embedded into everyday workflows.
Conclusion
The journey to integrating DevSecOps isn’t just about adopting new tools—it’s a fundamental shift in mindset and culture. In today’s fast-paced world of software development, where speed often takes precedence, security must be an integral part of every stage, not an afterthought. By embedding security into every step of your development lifecycle, from code creation to production deployment, you create a proactive defence against potential threats.
DevSecOps empowers organizations to build security into their development processes, fostering a culture of shared responsibility and continuous improvement. Whether you’re at the beginning of your DevSecOps journey or looking to optimize your existing practices, the key is to choose tools that align with your needs while also driving collaboration and automation.
Remember, there’s no one-size-fits-all solution. By focusing on the right combination of strategies, tools, and cultural shifts, you can build a robust, secure development process that keeps pace with innovation—without compromising on protection. Security doesn’t have to slow you down; with DevSecOps, it becomes an accelerator, allowing you to deliver software that’s both fast and secure.




