Introduction:
Infrastructure as Code (IaC) has transformed how organizations manage and provision their infrastructure. By treating infrastructure as code, teams can automate deployments, achieve consistent environments, and scale rapidly. However, this shift introduces new security challenges. Misconfigurations in IaC scripts can expose environments to significant vulnerabilities. Understanding the role of IaC in DevSecOps highlights the importance of integrating security from the beginning, ensuring that the infrastructure is as secure as the application it supports.
Key Security Risks in IaC
Infrastructure as Code (IaC) streamlines infrastructure management through automation, reproducibility, and scalability. Addressing risks is paramount, as failure to do so can result in severe data breaches, downtime, compliance issues, and reputational harm. Proactive risk management fortifies infrastructure, aligns with best practices, and meets regulatory requirements. However, security risks that should be carefully managed:
-
Insecure Defaults:
Risk: Many pre-configured settings prioritize functionality over security, like default credentials or permissive network configurations that can easily be exploited.
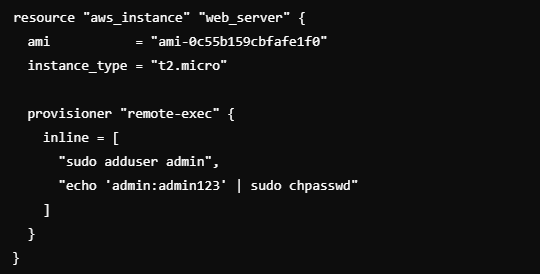
Leaving default admin usernames and passwords unchanged in IaC scripts could allow attackers to gain unauthorized access.
-
Configuration Drift:
Risk: Configuration drift occurs when the actual state of your infrastructure diverges from what is defined in your IaC scripts due to manual changes, updates, or overlooked errors.
An untracked change to security group rules that opens sensitive ports could go unnoticed, exposing your environment to attacks.
-
Hardcoded Secrets:
Risk: Embedding sensitive data like API keys, passwords, or tokens within IaC scripts makes them vulnerable if those scripts are shared or exposed.
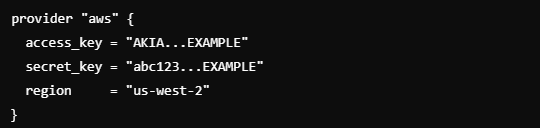
Storing access keys in a public repository could lead to unauthorized access to critical resources.
-
Overly Permissive IAM Policies:
Risk: Inappropriate access controls in IaC configurations can lead to users or services having more permissions than necessary, increasing an attack’s blast radius.
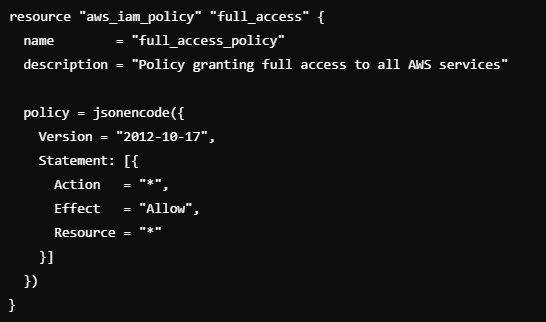
We are allowing full administrative privileges in IAM roles instead of following the principle of least privilege.
-
Lack of Version Control:
Risk: Failing to version-control IaC configurations can make it difficult to track changes, potentially leading to the deployment of insecure configurations. For e.g. Rolling back to an earlier state with known vulnerabilities because the changes were not properly tracked, As Without using Git or another VCS, changes aren’t tracked, increasing the risk of reintroducing vulnerabilities.
-
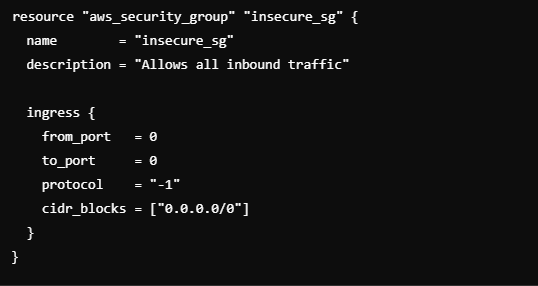
Insecure Network Configurations:
Risk: Incorrectly configuring network settings, such as overly broad CIDR blocks or open security group rules, can expose critical infrastructure.
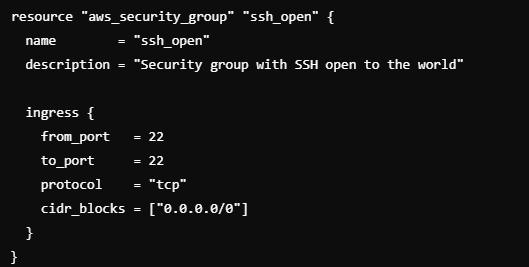
We are allowing inbound traffic from any IP address to sensitive ports like SSH or RDP.
By addressing these vulnerabilities proactively, you can significantly reduce the attack surface and maintain a secure and compliant infrastructure.
Secure IaC Practices
In Infrastructure as Code (IaC), ensuring security is pivotal for maintaining a robust and reliable IT environment. By employing best practices such as validated modules, code linting, and integrating security into CI/CD pipelines, organizations can fortify their infrastructure against vulnerabilities and compliance risks. These are a few key strategies for supporting IaC security.
3.1 Secure Coding and Templates
- Using Validated Modules and Templates: Reusing tested and validated templates reduces the risk of introducing insecure configurations. Many platforms provide secure, community-validated modules that follow best practices. In Terraform, using official or community-reviewed modules like vpc ensures that configurations on the modules follow best practices for security.
- Implementing Code Linting and Validation: Automated code linting and validation help catch potential misconfigurations early in the development cycle. Tools like Checkov, TFLint, and KICS can be integrated into your CI/CD pipelines to ensure code quality and compliance before deployment. As TFLint can automatically enforce policies like ensuring encryption is enabled enabling AWS-specific linting rules, ensuring resources comply with security best practices by default for all resources, preventing misconfigurations from reaching production.
3.2 Integrating IaC Security into CI/CD Pipelines
Securing IaC doesn’t end with coding—it must be woven into the CI/CD workflow. By integrating security checks directly into the pipeline, you can ensure that every code change is validated against security and compliance policies before it reaches production.
- Security as an Integrated Step in the Pipeline: Security checks must be introduced early, ideally as soon as the code is committed. Integrating tools like SAST, linting, and policy validation into the CI/CD pipeline allows security assessments to occur alongside regular code testing. Developer runs the Checkov scan which is triggered whenever a pull request is created. If any violations like overly permissive IAM roles or unencrypted data stores are detected, the pipeline can automatically fail, preventing insecure code from advancing.
- Automated Testing and Continuous Compliance: Tools like Terraform Sentinel and Open Policy Agent (OPA) enable continuous compliance by validating every code change against predefined policies. OPA policy denies any deployment where a security group allows inbound traffic from 0.0.0.0/0 ensuring that only secure configurations reach production.
Integrating these security practices reduces the risk of deploying vulnerable infrastructure by catching issues early. Real-time feedback encourages best practices, while automated checks ensure consistent compliance with security policies. This streamlined approach strengthens your overall security posture and minimizes risks before they reach production.
Embedding security into IaC workflows ensures safer, more reliable infrastructure while addressing compliance requirements efficiently.
Tools for IaC Security
These tools offer a comprehensive range of functionalities for securing IaC environments, from early-stage misconfiguration detection to continuous compliance monitoring. By integrating these solutions into your CI/CD pipelines and workflows, you can enhance the security of your infrastructure and prevent common vulnerabilities from impacting your deployment.
- Checkov: An open-source tool that scans Terraform, CloudFormation, Kubernetes, and ARM templates for misconfigurations.
- Terraform Sentinel: A policy-as-code framework used for enforcing policies in Terraform configurations.
- TFLint: A Terraform linter focused on identifying best practices, errors, and security concerns.
- KICS (Keeping Infrastructure as Code Secure): An open-source static analysis tool that scans various IaC formats for security vulnerabilities.
- Open Policy Agent (OPA): A general-purpose policy engine for enforcing policies in IaC, Kubernetes, and more.
- Cloud Custodian: An open-source tool for managing cloud governance and compliance policies.
- Conftest: A tool for validating configuration files using custom policies written in Rego.
- Snyk IaC: A developer-friendly tool for identifying and prioritizing security risks in IaC.
- Bridgecrew: A platform offering end-to-end IaC security with automated policy enforcement and remediation.
- Prowler: A security tool primarily for AWS, useful for auditing configurations and enforcing compliance standards.
- Aqua Security (tfsec): A static analysis tool for Terraform that identifies potential security risks.
- Gauntlt: A security testing framework designed for continuous security by running attack simulations against IaC deployments.
Conclusion
Infrastructure as Code (IaC) enhances automation and scalability, but it introduces security challenges that must be managed. Addressing risks such as insecure defaults, configuration drift, and hardcoded secrets is vital for maintaining a secure environment. Implementing secure coding practices, utilizing validated modules, and integrating security checks into CI/CD pipelines are essential for identifying and addressing vulnerabilities early. Tools like Checkov, Terraform Sentinel, and TFLint play a key role in this process. By adopting these practices and tools, you can strengthen your infrastructure’s security and reduce the risk of vulnerabilities impacting your production environment. Embracing these measures ensures a more resilient and secure infrastructure as you scale.




