Incident Response (IR) is essential for managing security breaches and mitigating risks in today’s digital landscape. By quickly detecting and addressing threats, organizations can minimize damage and maintain business continuity. Aspia Infotech is here to help with the knowledge and resources necessary to protect your company from possible dangers, our cybersecurity experts will be at your disposal.
In this article, we’ll go over some fundamental issues with incident response, draw attention to some key data, and demonstrate how Aspia Infotech can support you.
What is Incident Response?
The comprehensive process that businesses use to identify, evaluate, and address cybersecurity incidents—such as malware infections, network intrusions, and data breaches—is known as incident response. There are several steps in this process: identifying possible threats, assessing their scope, and getting back to business as usual. Numerous companies have specialized incident response teams that are tasked with handling security occurrences and reducing dangers.
An effective incident response plan enables businesses to respond quickly and efficiently allowing them to contain threats before they escalate and reduce their overall impact on operations. Importantly, it doesn’t just focus on immediate action; it also includes a post-incident analysis phase. This stage is essential for gaining insightful knowledge that will help stop such occurrences in the future.
Importance of Effective Incident Management
Let’s take a moment to discuss why incident management is so vital for organizations today. World where cyberattacks are on the rise, the ability to manage and respond to incidents effectively can make a significant difference. Whenever a security incident occurs, their response speed and efficiency can help control and mitigate the impact, preventing further damage.
Every minute that an incident goes unmanaged can lead to increased downtime, greater financial loss, and a hit to customer trust. This is where an effective incident management process comes into play. It ensures that all actions are organized, coordinated, and timely, allowing organizations to minimize the damage and recover affected systems more rapidly.
Understanding The Growing Threat Landscape
Every day, Black hat attacker are finding new ways to exploit vulnerabilities, and their methods are becoming more and more sophisticated. Cyber dangers of all kinds, including ransomware, web compromise, email compromise, unauthorized access, and insider threats, are becoming more prevalent. Each of these poses unique challenges that businesses need to prepare for.
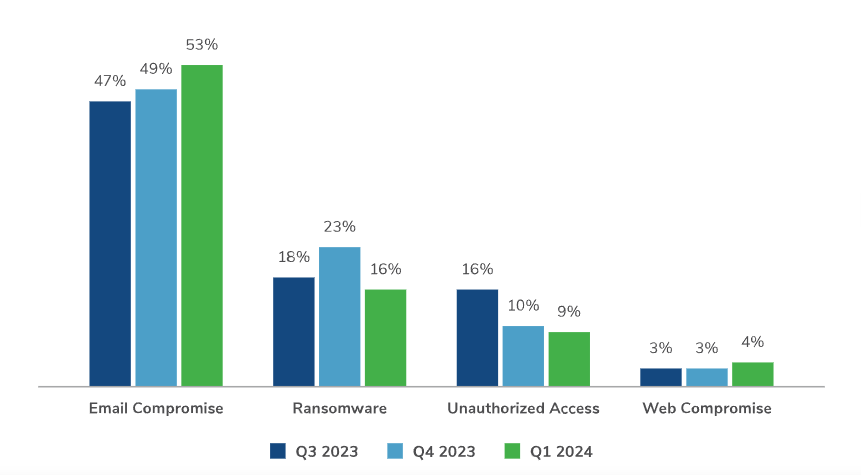
One of the key factors are complicating environment the increasing reliance on cloud services, Internet of Things (IoT) devices, and remote work setups. Despite all of the positive effects, these developments also give hackers new targets to go for. For instance, critical infrastructure, financial institutions, and healthcare organizations are particularly very vulnerable because of the sensitive and valuable data they handle.
The complexity and scale of modern attacks underscore a comprehensive incident response strategy. This strategy should not only react to incidents as they occur but also prepare the organization to prevent them from happening in the first place. By taking these steps, businesses can better safeguard themselves against the ever-present and evolving threat of cyberattacks.
Main Objectives of Incident Management
We’ll go into more detail about incident management’s primary goals now and why they’re so important to the operation of any business. To understand how this to achieved, we can break it down into several key areas as we will discuss further in detail:
- Early Detection
- Swift Containment
- Thorough Investigation
- Efficient Recovery
These basic objectives of incident management are to reduce risk, provide business continuity, and safeguard the assets and reputation of the company. Organizations may strengthen their defenses against potential threats and increase the effectiveness of incident response with a more efficient incident management procedure. By being proactive, they can safeguard not just their information but also their relationships with customers and stakeholders, establishing reliability and trust even in the face of adversity.
Minimizing the Effect of Security Incident
With the increase of cyberattacks, data breaches, and system failures, enterprises today have a fundamental responsibility to minimize the impact of security incidents. The objective is to swiftly and efficiently limit the harm that these accidents can do to safeguard the company’s operations, resources, and reputation. Let’s dissect this into a few essential parts.
- Prompt detection is the first step towards limiting impact. Systems that continuously monitor an organization’s networks and data must be in place. Intrusion detection systems (IDS), which are automated security solutions that may notify teams of anomalous activity in real-time, may be used in this situation. An organization’s ability to restrict the extent of an event depends on how quickly it can recognize that something is amiss and take appropriate action.
- Effective response plans are crucial as soon as an issue is identified businesses should have a plan in place for handling incidents, outlining what should be done in the event of a problem. A well-crafted strategy will delineate distinct roles and duties, establish communication procedures, and specify the precise containment and mitigation measures that must be implemented. The earlier a company can respond and minimize disruptions, the more prepared it is.
- Containment is a vital component of minimizing damage. Establishing containment procedures to separate impacted systems or networks should happen as soon as an issue is verified by organizations. One possible solution to stop a compromised server from infecting other systems is to disconnect it from the network. Likewise, entities may have to temporarily stop specific features or limit access to private data in the event of a data breach. The less harm that the incident can cause, the faster it is contained.
- Clear Communication In an emergency, communication is essential. Effective management of internal and external communications is essential for organizations. It’s critical to educate all parties involved internally, including management, staff, and IT departments. Everyone can more successfully coordinate efforts and know their roles when there is good communication.
- Pre pre-planned incident response plan is essential to any firm. This strategy should include frequent training and simulations for the incident response team in addition to a checklist of measures to perform during an occurrence. Employees who practice with simulations regularly get comfortable with their jobs and are better equipped to respond when an actual incident happens. Being ready is essential to minimize disruptions to operations and lower the organization’s total financial impact.
- Post-Incident Review the incident after Organizations must carry out a comprehensive post-event review as soon as the incident is resolved. This assessment aids in determining what worked, what didn’t, and how protocols may be strengthened in the event of similar occurrences. To further reduce the impact of future security incidents, this continuous improvement strategy makes sure that the lessons learned from each incident are incorporated into the organization’s overall security posture.
These not only protect their operations and data but also foster trust among stakeholders, ultimately contributing to their long-term success.
Ensuring Quick Containment and Remediation
-
The Importance of Quick Containment
Quick containment is essential because it limits the spread of a security incident. Once a threat is identified, the goal should be to prevent it from propagating through the network and affecting other systems. If containment is delayed, the threat could escalate, leading to more severe repercussions, such as data loss, operational disruption, or even reputational damage.
-
Containment Strategies
Organizations have several effective containment strategies they can use:
- Isolating Affected Systems: One of the first actions is often to isolate the affected systems. This may involve disconnecting compromised servers or workstations from the network to prevent unauthorized access or further exploitation. By doing this, the incident response team can focus on recovery efforts without worrying about the threat spreading.
- Disabling Affected User Accounts: If the incident involves compromised user accounts—such as credentials being stolen or misused—those accounts should be promptly disabled. This prevents attackers from continuing to use those accounts to access sensitive information or other systems.
- Applying Patches and Updates: In situations where vulnerabilities have been exploited, applying patches and updates is an essential containment strategy. By fixing these vulnerabilities, organizations can reduce their risk of similar incidents occurring in the future. For instance, if a particular software version has a known security flaw that was exploited, updating it can help mitigate that risk.
-
Transitioning to Remediation
Once containment measures are in place, the focus shifts to remediation. This stage involves addressing the root causes of the incident to ensure it doesn’t happen again.
- Removing Malware: If malware has been detected during the incident, it must be thoroughly removed from affected systems. This often involves using specialized security software to scan for and eliminate malicious code. It’s vital to ensure that the malware is completely eradicated, as remnants could lead to a resurgence of the incident.
- Fixing Vulnerabilities: Beyond just applying patches, organizations need to conduct a comprehensive assessment of their systems to identify any other vulnerabilities that could have contributed to the incident. This assessment may involve penetration testing or vulnerability scanning to uncover weak points.
- Implementing Security Updates: After addressing immediate threats, ensuring all systems are updated with the latest security measures is crucial. This may include updating antivirus programs, implementing new firewall rules, and ensuring that backup systems are functioning correctly.
-
The Critical Role of Speed
Speed is of the essence during both the containment and remediation phases. The quicker the response, the less damage the organization typically incurs. Delays can lead to increased downtime, higher recovery costs, and more significant consequences. A speedy response helps organizations maintain operational integrity while identifying and remedying security gaps.
-
The Role of a Well-Rehearsed Incident Response Plan
One vital factor in ensuring quick containment and remediation is having a well-rehearsed incident response plan. This planning should be comprehensive and have clearly defined roles and responsibilities for their team members. Regular drills and simulations help prepare staff to react quickly and effectively when an incident occurs. These rehearsals train team members how to collaborate efficiently, communicate effectively, and execute containment and remediation strategies without hesitancy.
Organizations can reduce the impact of security incidents and improve their overall security posture by focusing on thorough remediation and using effective containment strategies.
Preserving Data Integrity and Business Continuity
-
Understanding Data Integrity
Data integrity refers to the accuracy, consistency, and reliability of data throughout its lifecycle. When a cyber incident occurs—such as a data breach, ransomware attack, or system failure—the integrity of critical data is often at risk. This could include sensitive information like customer details, financial records, and intellectual property.
Key Measures to Preserve Data Integrity:
- Data Backup: Regularly backing up data is fundamental. This often involves creating copies of data in various secure locations to ensure that, in the event of corruption or loss, the organization can restore information to its original state.
- Access Controls: Implementing stringent access controls ensures that only authorized personnel can access, modify, or delete critical data. This minimizes the risk of unauthorized access during an incident and helps maintain data integrity.
- Data Validation: Employing data validation techniques helps ensure that only accurate and uncorrupted data is stored or processed. This might involve checksums, hashing, and validation rules.
- Monitoring and Auditing: Continuous monitoring and regular audits of data access and integrity can help detect anomalies early, allowing teams to respond before more severe issues arise.
-
Ensuring Business Continuity
Business continuity refers to an organization’s ability to maintain essential functions and operations during and after a disruptive incident. Organizations must minimize downtime and swiftly restore operations to reduce potential losses in revenue and customer trust.
Strategies for Ensuring Business Continuity:
- Business Continuity Plans (BCP): A comprehensive BCP outlines the steps that should be taken before, during, and after a disruption. This includes identifying critical functions, resources and processes vital for business operations.
- Backup Systems: Implementing effective backup systems ensures that data can be restored with minimal disruption. Organizations may use cloud-based backups or off-site storage solutions, ensuring data accessibility even during a security incident.
- Failover Procedures: These procedures involve automatically switching to standby systems or processes in case the primary ones fail. For instance, if a server goes down, traffic may automatically reroute to a backup server to maintain service availability.
- Communication Protocols: Clear communication protocols are essential during an incident. This includes informing stakeholders—such as employees, customers, and partners—about the situation and what steps are being taken to address it. Effective communication helps manage expectations and builds trust.
-
Minimizing Downtime
The speed at which an organization can respond to an incident will significantly impact its downtime. Incident response teams should be trained to execute the established business continuity plans swiftly. This involves not just technical recovery efforts but also managing logistics and communication during incidents.
-
The Interlinked Nature of Data Integrity and Business Continuity
Preserving data integrity and ensuring business continuity are interrelated. A loss of data integrity can lead to significant operational disruptions, which in turn affects business continuity. For example, if customer transaction data becomes corrupted after a cyber incident, it could hinder the organization’s ability to process orders or maintain accurate financial reporting.
Conversely, an effective business continuity strategy can help protect data integrity by ensuring that data systems remain operational and secure throughout a disruption. By addressing both aspects simultaneously, organizations can create a robust response framework.
By implementing strategies focused on data backup, access control, failover procedures, and effective communication, organizations can respond proactively to incidents, minimize damage, and maintain operations amidst challenges. This integrated approach ensures that when crises emerge, organizations are prepared to navigate through them and emerge resilient.
Reducing Financial and Reputational Loss
-
Financial Losses from Cyber Incidents
When a cyber incident occurs, there are many ways an organization can experience financial losses:
- System Downtime: Imagine your favorite online store suddenly going offline because of a cyberattack. No one can make purchases, and the business is losing money. The longer the store is down, the more revenue is lost. This is what we mean by downtime triggering financial losses.
- Legal Liabilities: If customer data is compromised, the organization may face lawsuits or regulatory fines. For example, organizations governed by data protection laws like the GDPR can incur heavy fines for not protecting personal data. This can create a significant financial burden.
- Loss of Business: Customers may decide to take their business elsewhere if they feel their data isn’t safe. If a company is in the news for a breach, potential customers might choose a competitor they believe has better security, leading to lost sales and long-term impacts on revenue.
-
Reputational Damage
Reputational damage can be just as, if not more, harmful compared to financial losses, and it’s often harder to measure:
- Loss of Customer Trust: Trust is foundational for all business relationships. If a company suffers a data breach, customers may no longer trust that their information is secure. This loss of trust can lead to reduced customer loyalty and significant drops in revenue.
- Negative Publicity: Cyber incidents tend to attract media attention. A negative story can reach a wide audience quickly, affecting how the public perceives the business. This kind of coverage can linger in the news cycle, making recovery more complex.
- Impact on Market Position: If a company loses customer trust and suffers from bad publicity, its standing in the market can be affected. Competitors might take this opportunity to promote their security measures, further complicating the recovery for the impacted organization.
-
Effective Incident Management
To mitigate both financial and reputational losses, organizations need to have effective incident management practices in place:
- Rapid Response: Speed is essential! The quicker you detect and respond to a cyber threat, the less damage it can cause. Think of it like catching a fire before it spreads—early intervention saves resources and minimizes losses.
- Threat Containment: Once a threat is identified, containing it should be a top priority. This could involve isolating affected systems or disabling compromised accounts. By controlling the situation early, you can prevent further damage and loss.
- Transparent Communication: Honest communication with stakeholders—like customers, employees, and partners—is crucial. If an incident occurs, informing those affected about what happened and how it’s being addressed can build trust and reduce anxiety.
-
The Importance of Communication Strategy
A clear communication strategy is especially critical following a cyber event:
- Crisis Communication Plans: Having a plan in place ensures everyone knows how to respond during a crisis. This includes who speaks to the media, what messages are shared, and how to keep stakeholders updated.
- Engagement with Stakeholders: Quick and transparent engagement lets customers know you’re taking the situation seriously. Providing information about the incident and outlining steps to resolve it can help rebuild trust.
- Prepared Spokespeople: Training individuals to communicate with the media and the public ensures that messages are consistent and accurate. Good communication can alleviate some of the fears customers may have and help manage the organization’s reputation.
-
Monitoring and Continuous Improvement
After an incident has been managed, it’s vital to reflect on what happened to improve future responses. This means analyzing the incident to identify what worked, what didn’t, and how to strengthen protections moving forward. Constantly improving your approach not only reduces the chance of future incidents but can also help diminish the impact of any that do occur.
By responding quickly, containing threats, and maintaining open and honest communication with stakeholders, businesses can navigate these challenging situations more successfully.
Incident Management Lifecycle
The incident management lifecycle is a systematic approach that organizations use to respond to security incidents. Understanding each stage in this lifecycle is crucial for effectively mitigating threats and improving overall security posture. It’s a vast topic but will try to mention important things, let’s dive into each stage with some details.
-
Identification
The first step in the incident management lifecycle is Identification. This is where the organization detects a potential security threat.
- Detection Methods: Various monitoring systems and tools, such as intrusion detection systems (IDS), firewalls, antivirus software, and security information and event management (SIEM) systems, play a critical role here. They provide alerts based on unusual activities or known signatures of malicious behavior.
- Importance of Early Detection: Timely identification of threats is crucial. The sooner a threat is detected, the less damage it can cause. For instance, if malware is spreading through a network, early detection allows IT teams to take quick action to contain it before it can encrypt files or exfiltrate data.
-
Containment
Once a threat has been identified, the next phase is Containment. This stage focuses on isolating the incident to prevent it from spreading further.
- Immediate Actions: Containment strategies might include disconnecting affected systems from the network, disabling compromised user accounts, or blocking suspicious traffic. The objective is to limit the threat’s impact and prevent additional damage.
- Strategies: There are two types of containment: short-term and long-term. Short-term containment involves quick fixes to minimize damage, such as shutting down affected systems. Long-term containment might include applying patches or reconfiguring systems to prevent the threat from occurring again.
-
Eradication
Once the incident is contained, the next step is Eradication. This involves removing the root cause of the incident.
- Removing Threats: Actions during this phase can include deleting malware, closing vulnerabilities, and performing thorough scans to ensure that no remnants of the attack remain. If an attacker exploits a specific vulnerability, it should be addressed by applying necessary patches or updates.
- Verifying Security: After initial eradication efforts, it’s essential to verify that the threat has been completely removed. This may involve further investigation and monitoring to ensure systems are secure before moving on to recovery.
-
Recovery
Following eradication, the lifecycle moves to the Recovery phase. Here, the organization focuses on restoring systems to their normal operational state.
- Restoration of Services: This may involve restoring data from secure backups, reinstalling software, and ensuring all systems are functioning correctly. Testing is important during this phase to confirm that systems are operating as expected.
- Monitoring: Once recovery actions are taken, there must be ongoing monitoring to detect any signs of residual threats or issues. This helps ensure that the system remains secure post-recovery and verifies that no further exploitation is occurring.
-
Lessons Learned
The final stage of the incident management lifecycle is the Lessons Learned phase. This is an essential step for improving future incident responses.
- Analysis of the Incident: In this phase, the organization analyses the entire incident—from detection through recovery—to identify what went well, what didn’t, and how the response can be improved. This might involve reviewing logs, discussing with team members, and documenting the findings.
- Documentation and Reporting: All findings should be documented thoroughly, including timelines, actions taken, and the overall effectiveness of the incident response. This documentation serves as a valuable resource for training and refining incident management protocols.
- Continuous Improvement: The insights gained from this review feed directly into the organization’s incident response strategy, leading to updated policies, improved detection and response tools, and better staff training. This cyclical learning process is crucial for creating a resilient security posture, ultimately reducing the risk of future incidents.
The incident management lifecycle is a strategic framework that guides organizations through the process of responding to security incidents. By moving through the stages of identification, containment, eradication, recovery, and lessons learned, organizations can better manage threats, minimize damage, and continuously improve their security practices. Each stage is interconnected, and a robust incident response allows organizations to not only recover from incidents but also to cultivate a culture of security awareness and proactive protection.
Key Roles and Responsibilities in Incident Management
Let’s look into the critical area of incident management, focusing on the key roles and responsibilities within an organization’s incident response framework. This subject is pivotal for understanding how teams can effectively respond to security incidents, minimize damage, and maintain operational continuity.
Incident Response Team Structure
To commence, let us outline the Incident Response Team (IRT). This team is fundamental in managing security incidents and is composed of various specialists, each tasked with specific responsibilities. Typically, the IRT consists of:
- Incident Manager
- Security Analysts
- Communication Teams
- Executives and Stakeholders
In this multi-disciplinary structure, each individual’s expertise complements the others, facilitating a comprehensive approach to incident management.
Role of the Incident Manager
Firstly, we must examine the role of the Incident Manager, who serves as the central figure in the incident response process.
- Leadership and Coordination: The Incident Manager orchestrates the efforts of the IRT, ensuring a coordinated response. This individual must maintain clear communication among team members, delineating responsibilities and tasks.
- Strategic Decision-Making: In the face of an incident, timely and informed decision-making is crucial. The Incident Manager evaluates the severity of the incident and determines the most appropriate response strategy.
- Resource Management: Effective incident management requires the proper allocation of resources. The Incident Manager is responsible for ensuring that the team has access to the necessary personnel, tools, and financial resources to respond effectively.
- Reporting and Documentation: After the resolution of an incident, the Incident Manager must document what transpired, including actions taken and outcomes achieved. This reporting is essential for compliance, future training, and process improvement.
- Training and Preparedness: The Incident Manager is also responsible for ongoing training and simulation exercises to prepare the team for potential incidents. This preparedness is vital for ensuring that the team is competent and confident in their response capabilities.
Responsibilities of Security Analysts
Next, we turn our attention to Security Analysts, whose expertise is indispensable in identifying and responding to threats.
- Threat Detection: Security Analysts continuously monitor the organization’s systems using advanced tools and methodologies to identify potential threats before they escalate.
- Incident Analysis: Upon detecting an anomaly, they conduct thorough investigations to uncover the nature of the threat, employing forensic techniques to understand its impact.
- Incident Response Execution: Following an analysis, Security Analysts enact containment strategies to mitigate the effects of the threat, ensuring that affected systems are isolated and secured.
- Post-Incident Review: After an incident has been resolved, Analysts participate in reviews to assess the effectiveness of the response efforts. This evaluation is critical for identifying areas for improvement.
- Continuous Improvement: Staying informed about evolving threats and vulnerabilities, Security Analysts recommend enhancements to the organization’s security policies and protocols.
Role of Communication Teams in Incident Response
A key component of effective incident management is the involvement of Communication Teams. Their role is critical in managing both internal and external communications during a crisis.
- Internal Communication: Communication Teams ensure that all internal stakeholders receive timely updates regarding the status of incidents and necessary actions to be taken.
- External Communication: Should an incident have ramifications for customers or partners, these teams are responsible for formulating communication strategies to maintain transparency and trust.
- Crisis Management: They manage the dissemination of information during an incident, working to counter misinformation and guide public perceptions.
- Post-Incident Communication: After resolving an incident, Communication Teams craft messages summarizing the event, the response taken, and measures implemented to prevent future occurrences.
- Media Relations: They serve as the primary contact for media inquiries, ensuring that all communications uphold the organization’s integrity and values.
Executive and Stakeholder Involvement
Lastly, the role of Executives and Stakeholders in incident management cannot be understated. Their involvement is essential for strategic alignment and resource support.
- Strategic Oversight: Executives play a pivotal role in shaping the organization’s incident management policies, ensuring they align with overall business objectives and risk tolerance levels.
- Resource Allocation: They are responsible for approving budgets and resources necessary for effective incident response, enabling the IRT to operate efficiently.
- Risk Assessment: Executives contribute to evaluating potential risks associated with incidents, helping to prioritize actions based on their impact on business operations.
- Policy Development: In collaboration with the IRT, executives help design and refine policies that govern incident response, ensuring compliance with applicable regulations.
- Review and Feedback: After an incident, executives participate in feedback sessions, offering insights that inform improvements in policies and response strategies.
How ASPIA Enhances Incident Response
ASPIA Infotech offers advanced solutions to help organizations detect, manage, and remediate security incidents efficiently. In an era of increasingly sophisticated cyberattacks, ASPIA enhances every aspect of the incident response process, ensuring teams can act quickly and effectively. Here’s how ASPIA significantly boosts incident response:
- Automation in Incident Detection and ResponseASPIA automates much of the detection and response process using machine learning and workflows to catch incidents faster. This automation reduces the Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) by handling repetitive tasks, allowing teams to focus on critical threats.
- Centralized Management of Security AlertsASPIA consolidates all security alerts into a centralized platform, pulling data from various sources to streamline alert management. This reduces false positives, prioritizes real threats, and makes it easier for teams to monitor and respond across the organization.
- Real-Time Threat Intelligence IntegrationASPIA integrates real-time global threat intelligence, providing up-to-date insights on emerging threats. This allows teams to proactively predict and prevent attacks, helping them stay ahead of attackers and respond more effectively.
- Streamlining Incident RemediationASPIA simplifies the remediation process with predefined workflows that guide teams in neutralizing threats. Automated steps, like isolating systems or applying patches, reduce the risk of incidents escalating. ASPIA also generates detailed reports to improve future responses.
- Customizable Incident Response PlaybooksASPIA’s playbooks ensure a structured approach to handling incidents, from phishing to malware. These customizable guides improve response times and align with the organization’s unique risk profile.
Relying on outdated or manual incident response processes puts your business at unnecessary risk. With ASPIA Infotech, you get advanced automation, real-time threat intelligence, and streamlined remediation, all designed to help your security team respond faster and more effectively. By centralizing your security alerts and guiding your team with customizable playbooks, ASPIA ensures that every incident is managed with precision and speed.
KPIs for Effective Incident Management
Key Performance Indicators (KPIs) that organizations utilize to measure the effectiveness of their incident response programs. Understanding these KPIs is essential for assessing how well an organization can identify, respond to, and recover from security incidents. The KPIs we will cover include:
- Mean Time to Detect (MTTD)
- Mean Time to Respond (MTTR)
- Number of Incidents by Severity Level
- Time to Full System Recovery
- Cost Per Incident Response
Let us examine each of these in detail.
Mean Time to Detect (MTTD)
Mean Time to Detect, or MTTD, is a pivotal metric that signifies the average duration it takes for an organization to identify a security threat from the moment it occurs. A low MTTD is essential for minimizing the potential damage that an incident may cause.
To achieve a reduced MTTD, organizations invest in several proactive strategies, including continuous monitoring of their systems, employing automated threat detection technologies, and engaging in active threat hunting. The quicker a threat is detected, the more time incident response teams have to contain and mitigate its effects.
Mean Time to Respond (MTTR)
Next, we examine Mean Time to Respond (MTTR), another critical metric that reflects the average time taken for an organization to contain and remediate a security incident after it has been identified. A low MTTR signifies robust incident response capabilities, as a prompt neutralization of threats reduces potential damage.
Effective incident response protocols, integrated automated tools, and well-defined response playbooks significantly contribute to minimizing MTTR. This metric also highlights the collaborative efficiency across different departments during the response phase, indicating how rapidly the team can execute containment, eradication, and recovery actions.
By consistently tracking and striving to lower MTTR, organizations can significantly mitigate the impacts of security incidents, ultimately preserving business operations and safeguarding sensitive information.
Number of Incidents by Severity Level
The metric known as the Number of Incidents by Severity Level provides organizations with insights into the frequency and scale of security threats they encounter. Incidents can be categorized into different severity levels—typically low, medium, high, and critical—each reflecting the potential damage posed to business operations, data integrity, or regulatory compliance.
By systematically monitoring the frequency and severity of incidents, organizations are better positioned to allocate resources judiciously and adjust their security measures appropriately. This KPI is invaluable for identifying trends over time, which can inform decision-making and highlight areas that may require enhanced security protocols.
A comprehensive understanding of incident severity helps organizations prioritize which threats necessitate immediate attention and which can be managed through automated processes or routine monitoring.
Time to Full System Recovery
The Time to Full System Recovery encompasses the duration required to restore all systems and services to their pre-incident condition following a security breach or disruption. This metric is critical for evaluating an organization’s resilience in the face of security incidents.
It is important to note that recovery involves not only the technical restoration of systems but also the resumption of normal business operations. Organizations must prioritize the swift restoration of critical services to minimize downtime, which can adversely affect productivity and customer satisfaction.
To optimize recovery times, organizations implement robust disaster recovery and business continuity plans. Regular testing and refinement of these plans are vital for ensuring that recovery procedures are both effective and efficient in the event of an incident.
Cost Per Incident Response
Finally, we have the Cost Per Incident Response metric, which quantifies the financial implications of responding to a security incident. This includes direct costs, such as labor, technology, and any external services utilized during the response. Additionally, it encompasses indirect costs like business downtime, damage to reputation, and potential regulatory penalties.
A high cost per incident can be indicative of inefficiencies within the incident response process. Such inefficiencies may stem from delayed detection, slow containment efforts, or deficits in remediation practices. By analyzing this metric, organizations can identify opportunities for optimization within the incident response framework.
Organizations should aim to reduce costs associated with incident response without compromising the integrity of their security measures. In doing so, they can enhance overall efficiency and strengthen their defenses against future incidents.
ASPIA’s Incident Response Features
ASPIA Infotech empowers organizations to efficiently manage and respond to security incidents with advanced, streamlined tools. Let’s explore the core features that make ASPIA a crucial asset for any security team:
- Automated Workflow and Task AssignmentsASPIA automates task assignments, ensuring quick responses by assigning roles such as containment to security analysts or patching to system administrators. Tracking progress in real-time minimizes delays and reduces the Mean Time to Respond (MTTR), ensuring incidents are managed efficiently.
- Real-Time Dashboards for Incident MonitoringASPIA’s real-time dashboards give a comprehensive view of ongoing incidents and key performance metrics like Mean Time to Detect (MTTD) and MTTR. This enables teams to monitor threats and make quick decisions, fostering better collaboration and faster resolution.
- Integration with 3rd-Party ToolsASPIA integrates seamlessly with existing security platforms like SIEM and vulnerability scanners, ensuring compatibility with your current infrastructure. This enhances threat analysis and centralizes security operations without disrupting workflows.
- Comprehensive Reporting and Audit LogsASPIA delivers detailed reports and audit logs for every incident, providing complete transparency and ensuring compliance. These logs help organizations improve their response by learning from past events and conducting thorough post-incident reviews.
ASPIA Infotech offers the essential tools to help organizations detect, respond, and resolve incidents quickly. With automation, real-time monitoring, and comprehensive reporting, ASPIA ensures your team can respond smarter and faster to today’s sophisticated cyber threats.
Best Practices for Implementing Incident Response
An effective incident response strategy is vital for organizations to safeguard their assets, maintain operational continuity, and protect their reputation in the face of cyber threats. Adhering to best practices ensures that organizations are well-prepared for any potential security incidents.
-
Regular Incident Drills and Simulations
Importance and Implementation
Regular incident drills and simulations are essential to ensure that your incident response team is well-prepared for real-world scenarios. These exercises have multiple critical functions:
- Testing the Response Plan: By simulating various types of incidents—such as ransomware attacks, data breaches, or insider threats—organizations can evaluate the effectiveness of their incident response plan under pressure.
- Identifying Weaknesses: Drills reveal potential gaps in the response process, allowing teams to pinpoint deficiencies that can be addressed before a real incident occurs.
- Familiarization with Roles: During simulations, team members practice their specific responsibilities in a controlled environment. This helps ensure that during an actual incident, everyone knows what their roles entail, contributing to a coordinated and efficient response.
- Building Confidence: These exercises instill confidence among staff by allowing them to practice their skills, enabling them to respond more effectively when faced with real threats.
Types of Simulations
- Tabletop Exercises (TTXs): These are discussion-based sessions where team members talk through their roles during a simulated incident scenario. They help familiarize staff with policies and procedures but do not involve hands-on execution.
- Live Drills: These involve the actual execution of the response plan, either in full or in part, enabling hands-on practice.
By conducting these drills regularly, organizations can not only refine their incident response processes but also improve coordination across teams, thereby ultimately reducing response times when incidents occur.
-
Creating an Incident Response Policy
Purpose and Components
An Incident Response Policy is a formal document that sets forth the guidelines for handling security incidents. Here’s why it’s important and what it should contain:
- Consistency and Efficiency: A clear policy ensures that incidents are handled consistently, allowing the team to pivot quickly and effectively during crises.
- Definitions of Security Incidents: The policy should provide clear definitions of what constitutes a security incident, helping the team identify and classify incidents appropriately.
- Roles and Responsibilities: This section outlines who is responsible for what actions during an incident. Clearly defined roles (such as Incident Manager, Security Analysts, etc.) ensure accountability and efficient response.
- Response Lifecycle Steps: The policy should delineate steps for each phase of the incident response lifecycle, including preparation, identification, containment, eradication, recovery, and lessons learned.
- Communication Protocols: Establishing protocols for internal and external communications—such as how to escalate issues and notify stakeholders—is crucial for maintaining transparency and managing reputational risk.
- Regular Reviews and Updates: Given the continuously evolving threat landscape and organizational changes, the Incident Response Policy should be reviewed and updated regularly to remain relevant. This includes incorporating lessons learned from past incidents.
In summary, a well-designed Incident Response Policy acts as a strategic blueprint for your response efforts, allowing for well-coordinated action when it’s needed most.
-
Continuous Monitoring and Threat Analysis
Significance and Strategies
Continuous monitoring and threat analysis form the backbone of an effective incident response strategy, allowing organizations to respond to threats in real time and pre-emptively.
- Real-Time Monitoring: Tools like Security Information and Event Management (SIEM) systems are used to collect and analyze security events from various sources. Continuous monitoring means that anomalies can be identified as they arise, which is crucial for early detection.
- Threat Intelligence Integration: Leveraging threat intelligence sources helps organizations stay informed about new vulnerabilities and trends in the threat landscape. This context assists in prioritizing and tailoring defensive measures.
- Proactive Threat Hunting: Organizations can take a step further by proactively searching for signs of vulnerabilities or attacks that may not yet have triggered alarms. This can involve simulating potential attack scenarios to uncover weaknesses.
Benefits of Continuous Monitoring
By employing continuous monitoring, organizations can detect incidents early in the attack chain, which significantly diminishes the potential damage of a security breach. This proactive posture is essential in today’s fast-paced cyber environment, where threats are constantly evolving.
-
Post-Incident Review and Knowledge Sharing
Critical Analysis After an Incident
A post-incident review is a fundamental part of the incident management process. Once an incident has been resolved, organizations need to analyze both their successes and shortcomings.
- Analyzing Responses: Teams need to evaluate not just what happened but also how effectively they responded. This requires input from all relevant stakeholders, including technical staff, incident managers, and business leaders.
- Understanding Root Causes: The primary purpose of the review is to identify the root cause of the incident. What vulnerabilities were exploited? What factors contributed to its occurrence?
- Learning and Improving: By understanding the incident’s dynamics, organizations can fine-tune their incident response strategies for better future outcomes. This may involve revising response plans, enhancing security protocols, or providing targeted training.
Knowledge Sharing
- Internal Communication: Post-incident reviews should not happen in isolation. The lessons learned should be shared broadly across the organization. This can include formal presentations, written reports, or informal discussions.
- Culture of Continuous Improvement: Fostering a culture where knowledge sharing is encouraged can significantly enhance an organization’s incident response capability. When staff members are aware of past incidents and the lessons learned from them, they are better equipped to handle future crises.
Conclusion
Incident response is a critical component of any organization’s cybersecurity strategy, ensuring that threats are swiftly identified, contained, and resolved. In a constantly evolving threat landscape, tools like ASPIA Infotech play a pivotal role by automating detection, streamlining response workflows, and integrating real-time threat intelligence. With features like centralized alert management, automated task assignments, and comprehensive reporting, ASPIA equips security teams to handle incidents more effectively and reduce downtime. By implementing a structured incident response plan and leveraging advanced platforms like ASPIA, organizations can minimize the impact of security incidents, safeguard their data, and maintain business continuity in the face of evolving cyber threats.




