What is it?
SQL injection is a type of security exploit where an attacker injects malicious SQL code into a vulnerable application’s database query, in order to gain unauthorized access to sensitive information or perform malicious actions.
In simpler terms, it’s a technique that hackers use to manipulate a database by inserting malicious SQL statements into an entry field, such as a search bar or login form, with the aim of tricking the database into executing unintended commands.
Types of SQL Injection
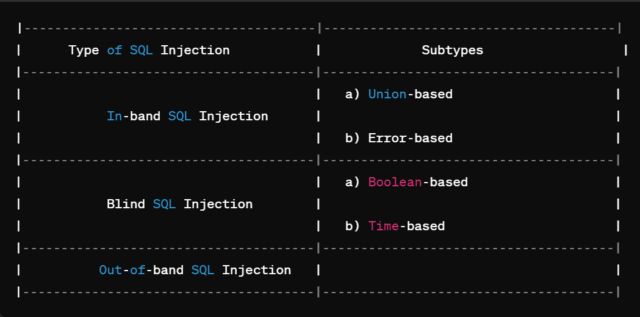
In-band SQL Injection:
In-band SQL Injection occurs when an attacker is able to use the same communication channel to both launch the attack and gather results. Here, communication channel means the mechanism used by the attacker to interact with the web application. Typically, this interaction happens over HTTP and HTTPS i.e. direct interaction with the web application.
In-band SQL Injection is of two types:
Union Based SQLi:
In union-based SQL injection, attackers use the UNION SQL operator to combine the results of two or more SELECT queries and retrieve data from other database tables. For example:
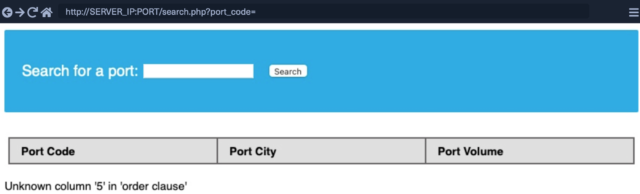
Now, to determine the number of columns of the second table, we use two methods:
- One method involves injecting a series of ORDER BY clauses and incrementing the specified column index until an error occurs.
‘ ORDER BY 1–
‘ ORDER BY 2–
‘ ORDER BY 3–
Now, Suppose, we get an error on using the payload ‘ORDER BY 5—
This means that the second table has 4 columns.
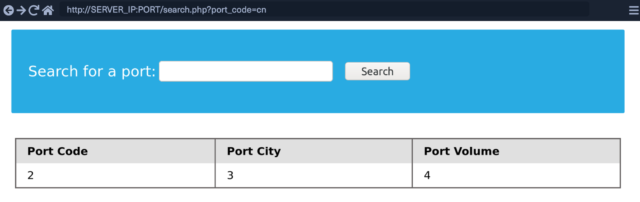
- The second method is using Union. In this method, we get an error every time until we enter the right amount of columns. For example,
Suppose, on using the payload
cn’ UNION select 1,2,3– –
we are getting an error, we will then use the payload
cn’ UNION select 1,2,3,4– –
Now, as we can see that we get the right results, which means the second table has four columns.
Union-based SQLi Payloads:
https://github.com/payloadbox/sql-injection-payload-list#:~:text=Generic%20Union%20Select%20Payloads
Error Based SQLi:
Error-based SQL injection is an In-band injection technique that enables threat actors to exploit error output from the database to manipulate its data. It manipulates the database into generating an error that informs the actor of the database’s structure. For example:
https://target.com/Books.aspx?class=Class%201&subject=
If this application is vulnerable to SQLi, it would throw an error if I use some payloads at any parameter. Now, let’s try putting ’ in the subject parameter.

As you can see, it threw an error so, using this, we can exploit it further.
Blind SQL Injection:
Blind SQL injection occurs when the attacker is unable to directly see the result of a query, but can infer the success or failure of the injection by observing differences in application behavior.
Basic payloads for error based SQLi:
https://github.com/payloadbox/sql-injection-payload-list#:~:text=Generic%20Error%20Based%20Payloads
Boolean based SQLi:
Boolean-based blind SQL injection is a subtype of blind SQL injection where the attacker observes the behavior of the database server and the application after combining legitimate queries with malicious data using boolean operators. For example:
Suppose there’s a query that is being executed. The query is as follows:
SELECT * FROM products WHERE id = product_id
Now, we will try injecting our payloads along with the right patameter.
SELECT * FROM products WHERE id = 42 and 1=1
SELECT * FROM products WHERE id = 42 and 1=0
If the application behaves differently in each case, it is susceptible to boolean-based blind SQL injections.
Time-Based SQli:
Time-based SQL injection is a type of blind SQL injection attack, where an attacker sends specific SQL queries that force the database to ‘sleep’ or pause for a specified period, thus confirming the vulnerability. This technique is used when the application is configured to suppress error messages but hasn’t sufficiently mitigated the underlying SQL injection vulnerability.
For example, in the following case, the response from the server will be delayed according to the payload we use.
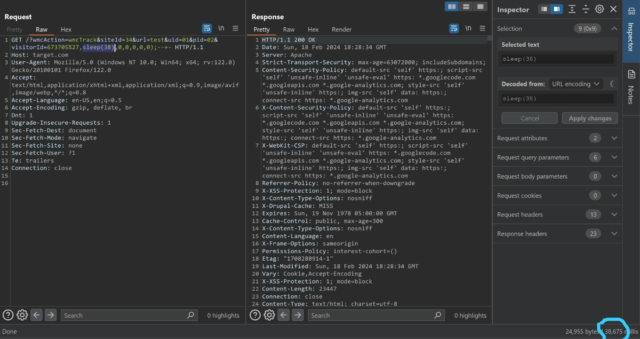
Payloads for Time based SQLi:
Out-of-band SQL Injection
Out-of-band SQL injection (OOB SQLi) is a type of SQL injection where the attacker does not receive a response from the attacked application on the same communication channel but instead is able to cause the application to send data to a remote endpoint that they control.
The easiest and most reliable tool for using out-of-band techniques is Burp Collaborator. This is a server that provides custom implementations of various network services, including DNS. It allows you to detect when network interactions occur as a result of sending individual payloads to a vulnerable application.
Impact of SQL Injection:
- Unauthorized Data Access: SQL injection can allow attackers to access, modify, or delete sensitive data stored in the database. This includes personal information, financial records, and authentication credentials.
- Data Manipulation: Attackers can manipulate the database to perform actions such as bypassing authentication, adding unauthorized users, or altering existing data, leading to integrity breaches.
- Denial of Service: In some cases, attackers can exploit SQL injection vulnerabilities to perform denial-of-service attacks by executing resource-intensive queries that overwhelm the database server.
- Authentication Bypass: SQL injection can bypass authentication mechanisms, allowing attackers to gain unauthorized access to restricted areas of the application or administrative functionalities.
What’s the Remediation:
- Secure Coding Practices: Train developers on secure coding practices to prevent SQL injection vulnerabilities, such as using parameterized queries and input validation.
- Regular Security Audits: Conduct regular security audits and vulnerability assessments to identify and remediate SQL injection vulnerabilities in web applications.
- WAFs and Database Firewalls: Deploy web application firewalls (WAFs) and database firewalls to monitor and block malicious SQL injection attempts in real-time.
- Patch Management: Keep web application frameworks, libraries, and database management systems up to date with the latest security patches to mitigate known vulnerabilities.





