What is it?
Business logic vulnerabilities are flaws in the design and implementation of an application that allow an attacker to elicit unintended behavior. This potentially enables attackers to manipulate legitimate functionality to achieve a malicious goal. These flaws are generally the result of failing to anticipate unusual application states that may occur and, consequently, failing to handle them safely.
How do these vulnerabilities arise?
Business logic vulnerabilities typically emerge when the underlying assumptions made by design and development teams about user interactions with the application don’t align with reality. These incorrect assumptions often lead to a failure in properly validating user inputs. For instance, developers might presuppose that users will only interact with the application through a web browser. Based on this assumption, they might overly rely on client-side controls for input validation. However, these controls are not robust and can be easily circumvented by attackers using tools like intercepting proxies.
The root cause of the problem is that these assumptions about user behavior lead to a security oversight. The application is not equipped to recognize or mitigate actions that fall outside of the expected use cases.
Attack Surface
Since these Business Logic Vulnerabilities rely on breaking the logic of web application, there is no specific way to approach every application. But, what we can do is, we can try looking at functionalities that are common in applications which might have possibilities of common attacks.
Scenario 1) Discount
While making a purchase on an E-Commerce website, you may encounter a business logic vulnerability. Suppose, the website offers a 20% discount for purchases totaling $400 or more, subject to terms and conditions. After adding products to my cart to meet the $400 threshold, the 20% discount coupon was applied automatically. However, during the checkout process, you can try removing certain items from my cart, reducing the total value less than $400. Despite the cart value falling below the $400 requirement, if the discount coupon remains valid, you will be offered the 20% discount at checkout.
This scenario has been seen in many shopping websites and poses a threat to the finances of the company.
Scenario 2) Price Tampering
Price tampering refers to the unauthorized alteration or manipulation of prices for goods or services within a business’s system or platform. This can involve changing the listed prices in a way that deviates from the intended pricing structure, whether by increasing, decreasing, or otherwise modifying the prices without proper authorization. Price tampering can occur in various industries, including retail, e-commerce, hospitality, and finance, and can be exploited through several means.
The most common way of exploiting it is via capturing the checkout request in burpsuite and modifying the value of the final price.
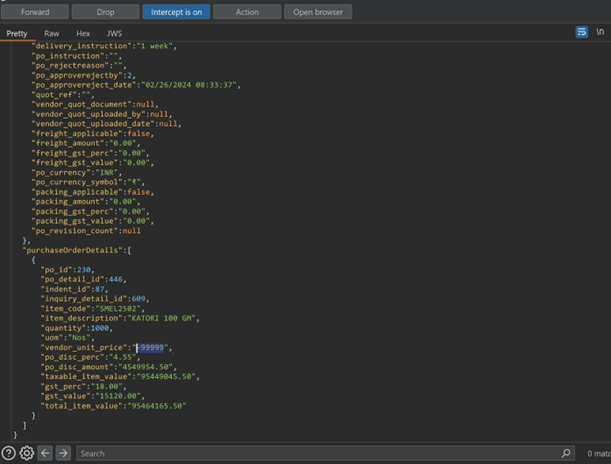
Scenario 3) Adding Negative Items in cart
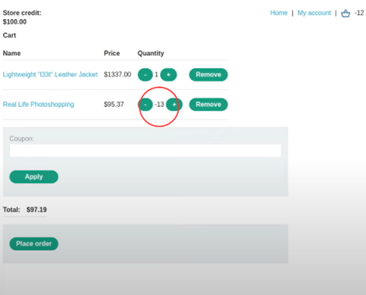
Imagine you’re shopping online and you want to buy something.
But sometimes, if the developers don’t write those rules carefully, weird things can happen. For instance, the system might accept negative numbers (like -1, -2, etc.) when it shouldn’t. Negative numbers don’t make sense when you’re talking about ordering items, right? It’s like saying you want to buy negative five apples – it doesn’t really work.
Now, imagine an attacker figures out that the system doesn’t check for negative numbers properly. They might try to exploit this by typing in a negative number when they buy something. If the system doesn’t catch it, they could trick the system into taking money from someone else’s account and putting it into their own! So, if they type in “-$1000” to buy something, the system might think they’re adding money to their account instead of taking it away.
So, developers need to be careful when they write these rules, or else someone might find a way to take advantage of the system.
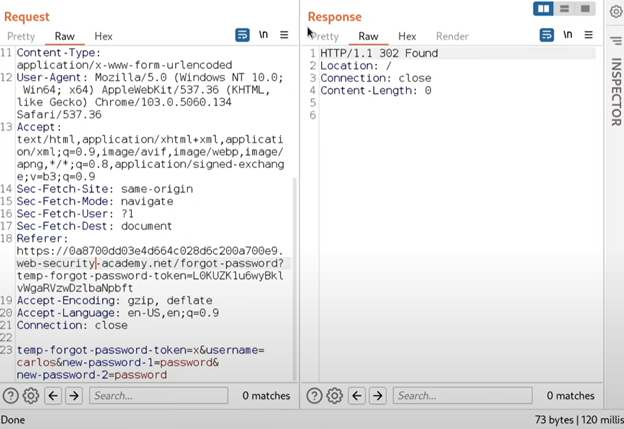
Scenario 4) Password reset broken logic
There are scenarios where password reset process isn’t implemented correctly. For example, In this case while resetting the password if we intercept the request in burpsuite, we will see a hidden parameter named username. Now, what we can do is, we can change the username to victim’s name and reset their password instead.
Scenario 5) 2fa bypass
In 2fa, you are supposed to enter the OTP or any code sent to you via mail or to your mobile in order to get logged in successfully. But, when this functionality is not implemented properly, what we can do is, we can simply do a force browsing i.e. manipulate the url to direct us to the dashboard hence, bypassing the 2fa mechanism.
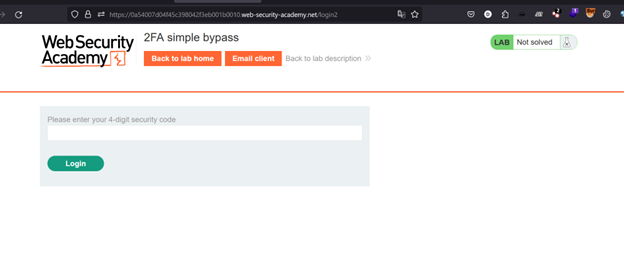
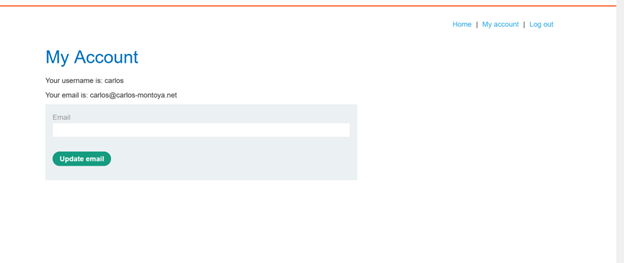
Here, we manipulated the url to /my-account and got logged in.
Impact
- Authentication Bypass: Authentication systems are the first line of defense for any web application. An Authentication Bypass vulnerability allows an attacker to gain unauthorized access to restricted areas of an application without valid credentials. This can occur due to flaws in the login process or session management.
- Inadequate Authorization Checks: Even if a user is successfully authenticated, it doesn’t mean they should have access to all parts of the application. Inadequate Authorization Checks occur when an application fails to verify whether a user has the necessary permissions to perform a particular action, potentially granting unwarranted privileges.
- Price Manipulation: E-commerce applications are susceptible to Price Manipulation vulnerabilities. Attackers can manipulate the price of products or services by tampering with client-side data, potentially causing financial losses for both businesses and customers.
- Account Enumeration: Account Enumeration vulnerabilities allow attackers to identify valid user accounts by exploiting differences in error messages or response times. This information can be leveraged for further attacks, such as brute force or phishing campaigns.
- Business Workflow Manipulation: Here, attackers exploit vulnerabilities in an application’s workflow, often involving multi-step processes. By manipulating the flow of operations, they can disrupt business operations, cause financial losses, or compromise sensitive data.
Preventing Business Logic Vulnerabilities
Preventing business logic vulnerabilities requires a comprehensive approach that involves understanding the domain, avoiding assumptions, maintaining clear documentation, writing clear code, and analyzing past mistakes. Here’s a more detailed breakdown of steps to prevent such vulnerabilities:
- Understand the Domain: Ensure that developers and testers have a deep understanding of the business domain that the application serves. This understanding will help them make informed decisions and anticipate potential pitfalls.
- Avoid Implicit Assumptions: Explicitly define assumptions about user behavior and application behavior. Avoid relying on implicit assumptions, as they can lead to overlooked vulnerabilities.
- Verify Assumptions: Implement logic to verify that assumptions are met. This involves validating input values and ensuring that the server-side state aligns with expected conditions before proceeding with any critical operations.
- Clear Design Documents and Data Flows: Maintain clear documentation that outlines the design of the application, including data flows, transaction processes, and any assumptions made at each stage. This documentation serves as a reference point for developers and testers to understand expected behavior.
By following these steps and continuously improving development practices, teams can significantly reduce the risk of business logic vulnerabilities in their applications.
Conclusion
In conclusion, mitigating business logic vulnerabilities demands a holistic approach that encompasses a thorough understanding of the application domain, meticulous validation of assumptions, and diligent adherence to best practices in development and testing. These vulnerabilities often stem from implicit assumptions, underscoring the importance of clear documentation, transparent communication among team members, and rigorous analysis of past mistakes. By fostering a culture of vigilance and continuous improvement, organizations can fortify their applications against the multifaceted threats posed by business logic vulnerabilities, safeguarding both their assets and their reputation in an ever-evolving digital landscape.





