Active Directory
A directory is a hierarchical structure that stores information about objects on the network. A directory service, such as Active Directory Domain Services (AD DS), provides the methods for storing directory data and making this data available to network users and administrators. For example, AD DS stores information about user accounts, such as names, passwords, phone numbers, and so on, and enables other authorized users on the same network to access this information.
Active Directory stores information about objects on the network and makes this information easy for administrators and users to find and use. Active Directory uses a structured data store as the basis for a logical, hierarchical organization of directory information.
Suppose you are administering a small business network with only five computers and five employees. In such a tiny network, you will probably be able to configure each computer separately without a problem. You will manually log into each computer, create users for whoever will use them, and make specific configurations for each employee’s accounts. If a user’s computer stops working, you will probably go to their place and fix the computer on-site.
Now, this is possible for small startups and companies but, if we talk about companies like Microsoft, Sony, Google with thousands of employees worldwide, will it be possible to manually configure each device? The answer is most likely no.
To overcome these limitations, we can use a Windows domain. Simply put, a Windows domain is a group of users and computers under the administration of a given business. The main idea behind a domain is to centralize the administration of common components of a Windows computer network in a single repository called Active Directory (AD). The server that runs the Active Directory services is known as a Domain Controller (DC).
Why is Active Directory Important?
Microsoft Active Directory commands approximately 43% of the enterprise market share for Identity and Access Management solutions. This significant market presence is expected to continue, especially as Microsoft integrates and improves AD with Azure AD. Notably, in the past two years, Microsoft has reported over 2,000 vulnerabilities associated with CVEs. AD’s comprehensive services and primary function of simplifying access to information can make it challenging to manage and secure properly. This complexity often leads to misconfigurations of services and permissions, which can leave enterprises vulnerable to exploitation. Combined with common user and OS vulnerabilities, these issues create a prime opportunity for attackers.
A real world usage of Active Directory in day to day life is, In school or university networks, students and staff are typically given a username and password that can be used on any computer within the campus. These credentials are valid across all machines because when you log in, the authentication request is sent to the Active Directory, which verifies your credentials.
This means your login information does not need to be stored on each individual computer but is accessible network-wide through Active Directory. Active Directory also enables the institution to enforce restrictions, such as preventing access to the control panel on campus computers. Network-wide policies are implemented to ensure that users do not have administrative privileges on these machines.
Now, to access the AD features search for Active Directory Domains and Services, type Active Directory Users and Computers in the search bar.
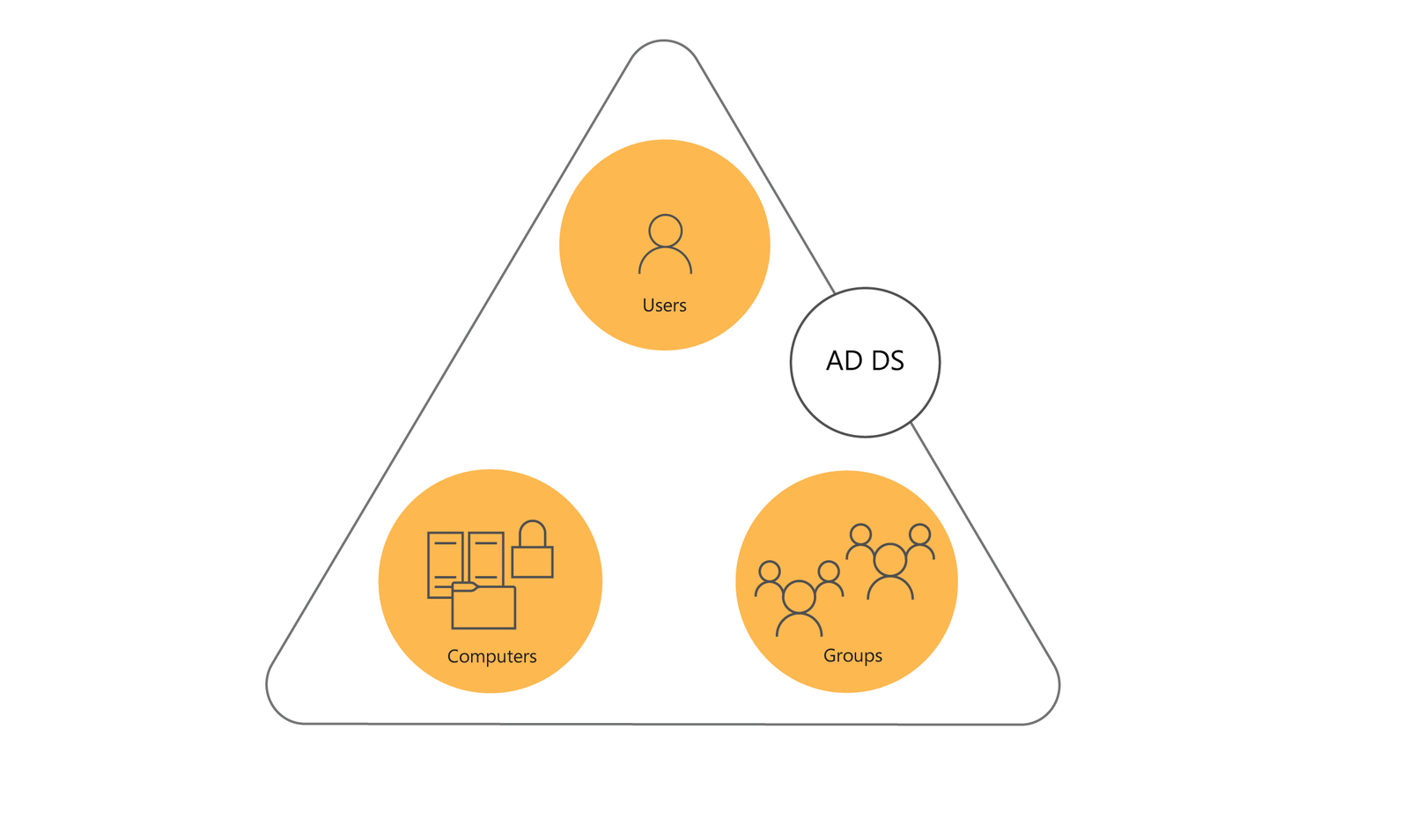
Users, Machines and Security Groups present in Active Directory:
Users:
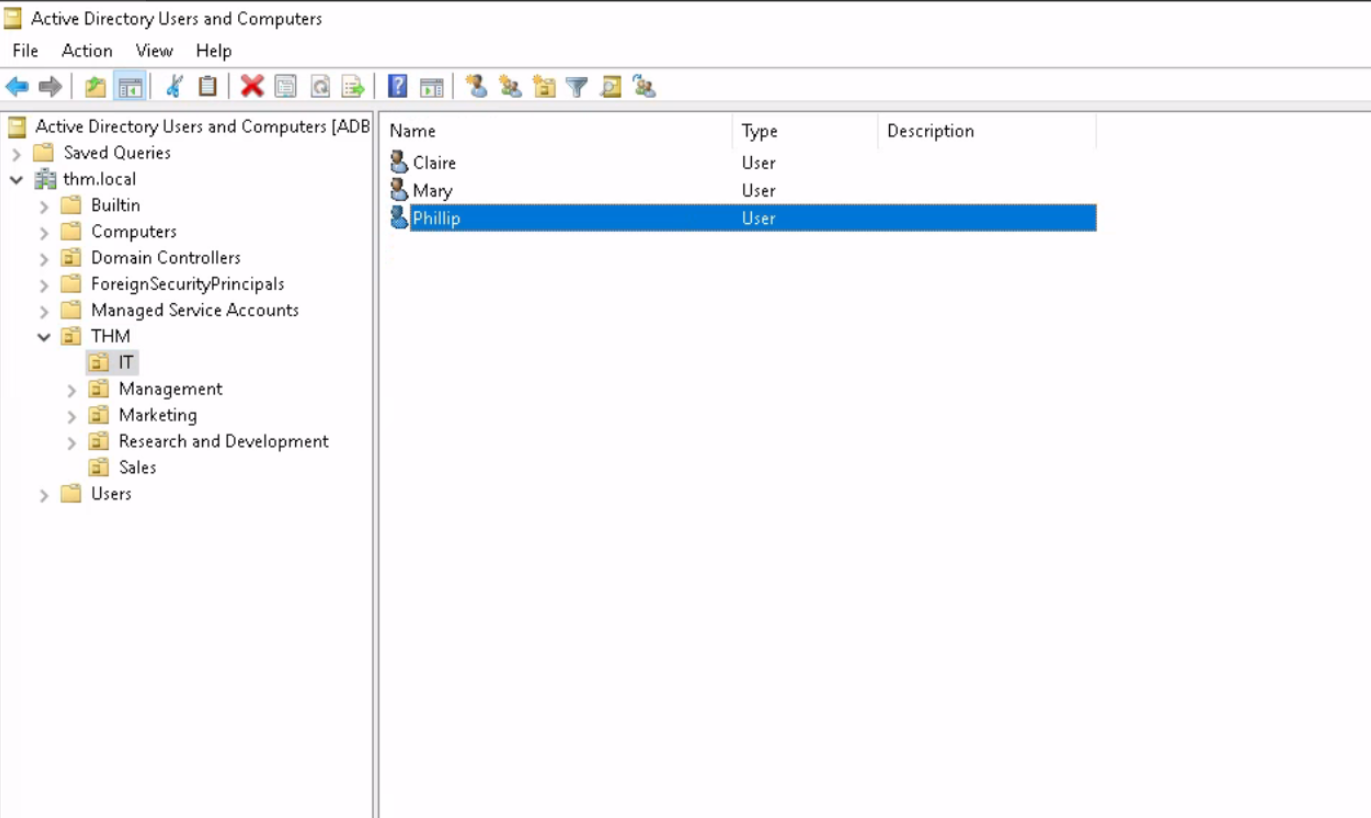
In Active Directory (AD), users represent individual accounts that can be assigned permissions to access resources. These accounts store important information about the users, such as their usernames, passwords, and personal details (e.g., full name, email address, and job title). User accounts can be managed individually or grouped together for easier administration. User accounts are essential for authenticating and authorizing access to network resources, applications, and data.
Machines:
Machines, also known as computer accounts, represent individual devices within the Active Directory environment. These accounts are used to manage and authenticate computers in the network. Machine accounts store information about the devices, such as their names, operating system versions, and security identifiers (SIDs). They are crucial for applying group policies, managing software updates, and ensuring secure communication between devices in the network.
Security Groups:
Security groups in Active Directory are collections of user and/or machine accounts that can be managed as a single unit. These groups are used to assign permissions and rights to multiple accounts simultaneously, simplifying the administration of security settings. There are two main types of security groups:
Domain Local Groups: Used to manage permissions within a single domain.
Global Groups: Used to manage permissions across multiple domains within a forest.
Security groups can be nested within other groups, allowing for flexible and scalable management of permissions and access control.
A typical Active Directory Structure looks like:
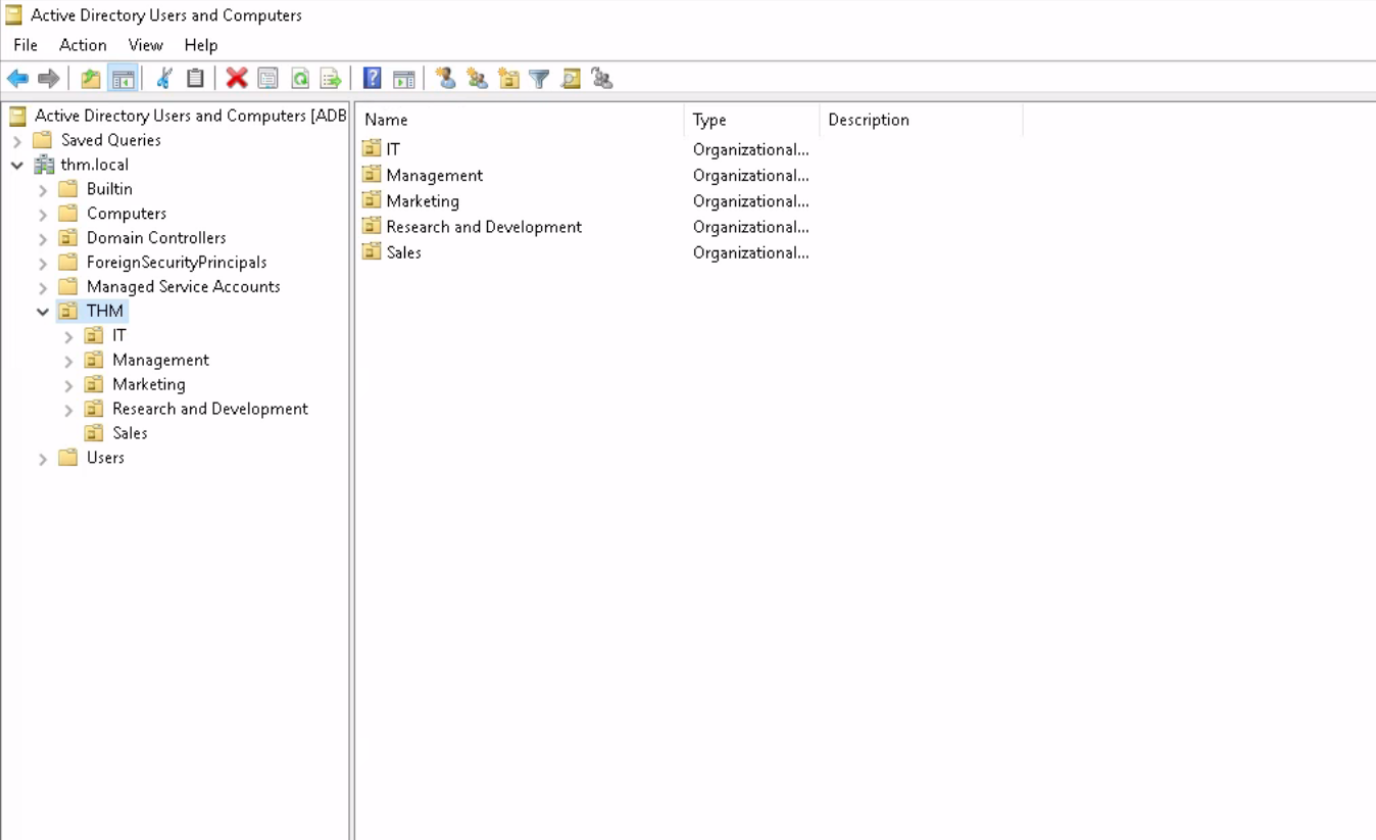
Organizational Units (OUs)
Organizational Units (OUs) are containers within Active Directory that help organize and manage objects such as users, groups, and computers. OUs provide a way to create a hierarchical structure that mirrors the organization’s structure, such as departments or geographical locations. They allow administrators to delegate specific administrative tasks and apply group policies at different levels of the hierarchy. OUs are essential for maintaining order, simplifying management, and enforcing security policies across the network.
Organisational Units versus Security Groups:
Security groups and Organizational Units (OUs) serve different purposes in Active Directory, each playing a crucial role in managing and securing network resources. Security groups are primarily used to assign permissions and rights to multiple users or computers at once. They simplify access control management by grouping accounts with similar access needs, allowing administrators to grant permissions to resources such as files, folders, printers, and applications efficiently. These groups can span across domains within a forest, providing a flexible way to manage security across the entire network. Security groups can contain users, computers, and other groups, offering significant flexibility in how permissions are assigned and managed.
In contrast, Organizational Units (OUs) are designed to organize and manage Active Directory objects like users, groups, computers, and even other OUs. They provide a way to reflect the organizational structure within AD, facilitating the management and delegation of administrative tasks.
Unlike security groups, OUs do not grant permissions to resources directly. Instead, they are used to apply Group Policy Objects (GPOs) and delegate administrative control over specific subsets of AD objects. OUs are limited to a single domain and are used to create a hierarchical structure within that domain. This structure allows for detailed and logical organization, making it easier to apply specific policies and manage administrative tasks at different levels within the organization. OUs can be nested to reflect complex organizational hierarchies, enabling targeted policy application and delegation of management tasks.
Managing Users and Computers in Active Directory:
Managing users and computers in Active Directory involves creating, configuring, and maintaining accounts and devices to ensure secure and efficient network operations. For users, this includes setting up user accounts with appropriate permissions, passwords, and personal information, and organizing them into groups for streamlined access management. User accounts can be managed individually or through security groups to simplify permissions assignment.
For computers, management involves setting up computer accounts that represent individual devices in the network. These accounts store information about the devices and are crucial for applying group policies, managing software updates, and ensuring secure communication between devices. Computers can also be organized into groups or OUs to facilitate centralized management and policy application.
Organizational Units (OUs) play a vital role in structuring these accounts, reflecting the organizational hierarchy and simplifying the delegation of administrative tasks and the application of group policies. By leveraging security groups and OUs, administrators can efficiently manage user and computer accounts, ensuring proper access control, security, and compliance across the network.
users:
Computers:
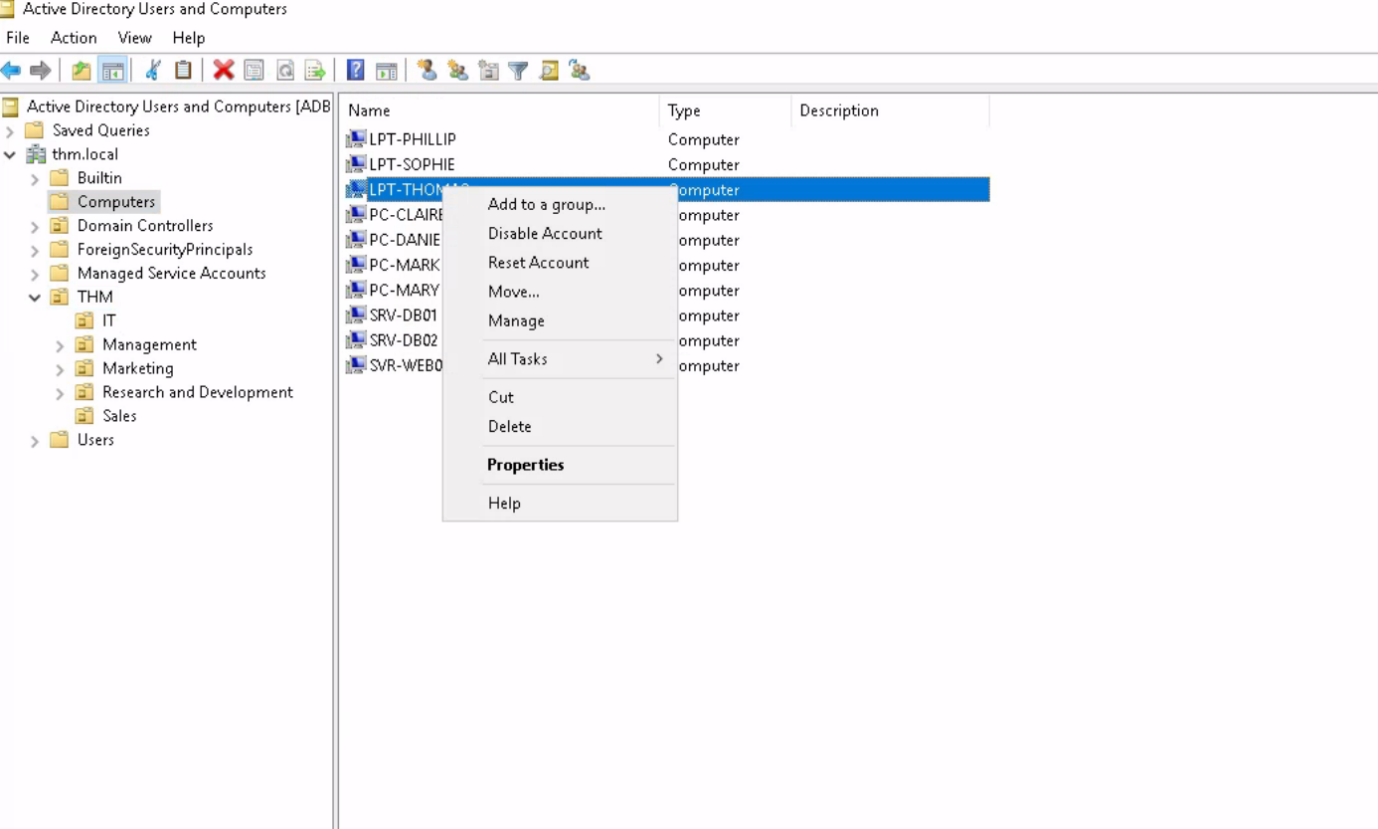
As you can see, AD allows us to manage Users and Computers. We can add users to any Group, Organizational Units we want, similarly we can disable, add new computers, reset accounts for computers available in Active Directory.
Group Policy Management:
Group Policy Objects (GPOs) in Active Directory are a powerful tool for centralized management and configuration of operating systems, applications, and user settings within an organization. GPOs allow administrators to define specific configurations and apply them consistently across multiple users and computers. This includes security settings, software installations, scripts, and desktop configurations.
GPOs are linked to Active Directory containers such as sites, domains, and Organizational Units (OUs). They are processed in a hierarchical order, ensuring that policies set at higher levels can be inherited by lower levels unless explicitly overridden. By using GPOs, administrators can enforce organizational policies, enhance security, and streamline the management of network resources, ensuring a standardized and compliant computing environment.
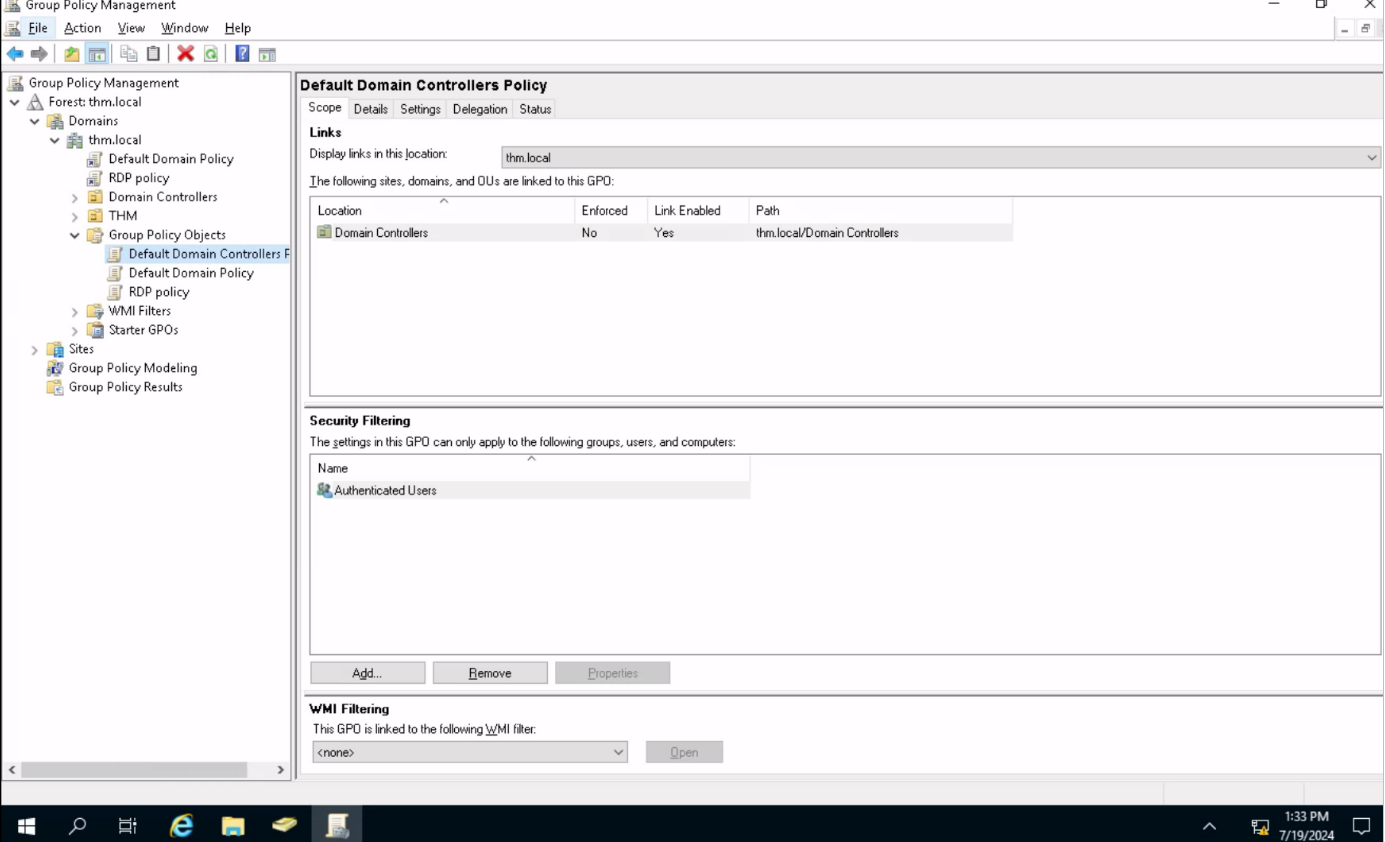
As you can see, we have different policies available in AD. We can configure, add new policies, remove existing policies and attach them to any object available in Active Directory.
Active Directory Trees and Forests:
Active Directory Trees and Forests are fundamental components of the Active Directory (AD) architecture that help organize and manage network resources across multiple domains.
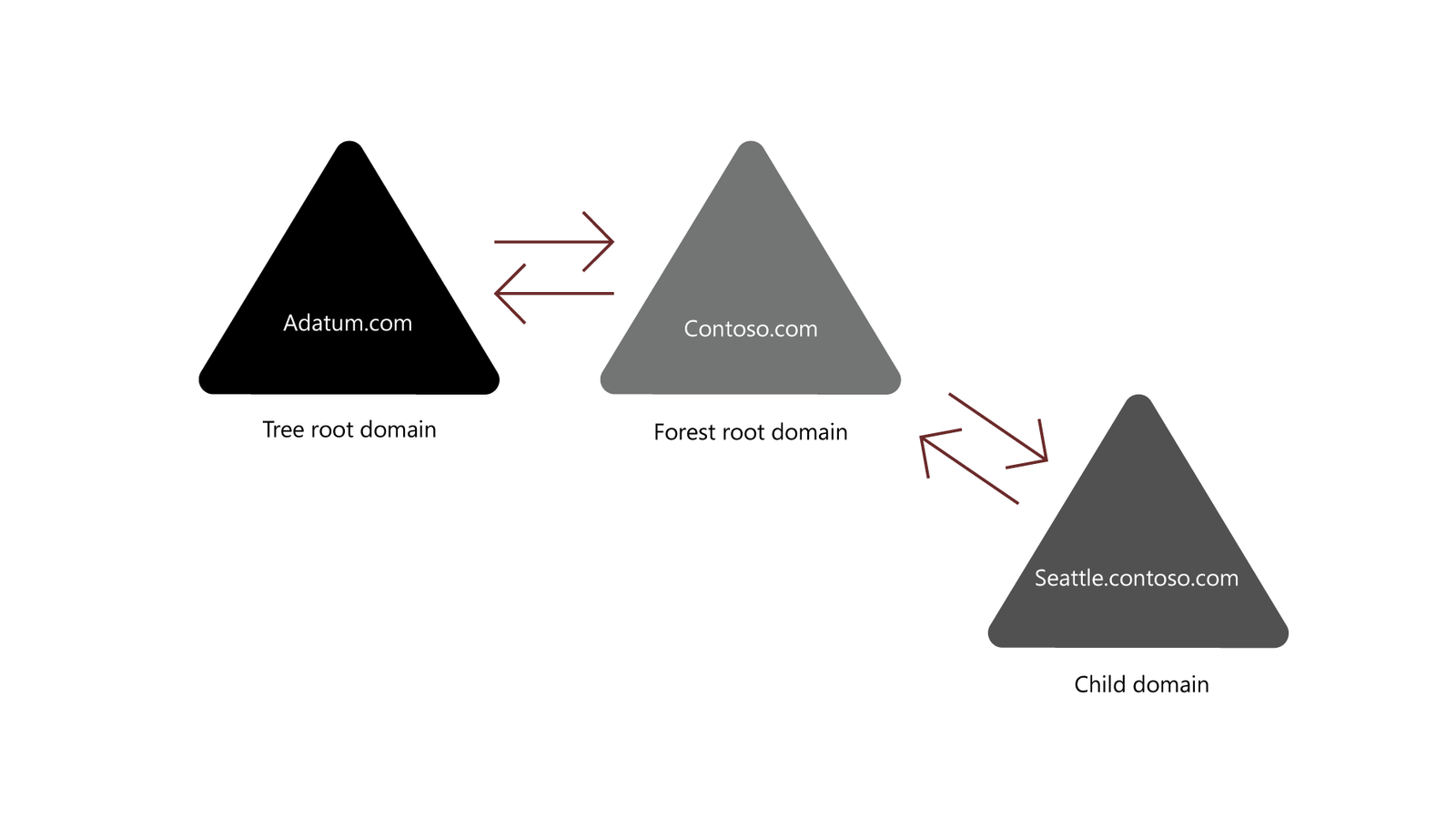
Trees: An Active Directory Tree is a collection of one or more domains that share a contiguous namespace. In simpler terms, a tree is a hierarchical structure where domains are linked together in a parent-child relationship, reflecting a domain hierarchy. The parent domain serves as the root of the tree, and child domains are created beneath it. Domains within a tree share a common schema, configuration, and Global Catalog, allowing for seamless integration and resource sharing. For instance, in a tree with the root domain company.com, a child domain might be sales.company.com, creating a hierarchical structure that simplifies management and access control.
Forests: An Active Directory Forest is a collection of one or more Active Directory trees that share a common schema and global catalog but operate with separate namespaces. Forests represent the top level of the AD hierarchy and are used to group multiple trees together, allowing for the management of complex and large-scale environments. Trees within a forest can be related or unrelated in terms of their domain names, but they all share a common schema and configuration. Forests enable organizations to manage different domain trees while maintaining a unified directory structure, ensuring that resources and information can be shared across trees within the same forest.
Together, trees and forests provide a scalable and flexible structure for managing domains, enabling organizations to handle complex networks and diverse requirements while ensuring consistency and interoperability across different parts of the network.
Overall, Active Directory provides a comprehensive framework for maintaining a secure, organized, and efficient network environment, supporting the dynamic needs of modern enterprises and enabling them to effectively manage their IT infrastructure.
Learn more about managing Active Directory objects: link
Our LinkedIn: https://www.linkedin.com/company/aspiainfotech/mycompany/