Footprinting Common Services:
Footprinting is a crucial step in the reconnaissance phase of cybersecurity, involving the systematic collection of information about a target system. This process is divided into two primary methods: active and passive reconnaissance. Active reconnaissance involves directly interacting with the target system to gather information, typically through techniques like network scanning, ping sweeps, and port scans. Tools like Nmap, Nessus, and OpenVAS are often used in active reconnaissance to identify open ports, services, and vulnerabilities. The main advantage of active reconnaissance is the depth and accuracy of the information collected, as it directly probes the target system to reveal detailed insights. However, it has the drawback of being easily detectable, potentially triggering security alerts and increasing the risk of exposure.
In contrast, passive reconnaissance does not involve direct interaction with the target system. Instead, it relies on third-party sources to gather information without alerting the target. Methods include searching public databases, querying WHOIS information, examining DNS records, and analyzing social media and online forums. Tools like Maltego and Shodan are useful for passive reconnaissance. The key benefit of passive reconnaissance is its stealthiness, as it minimizes the risk of detection since the target system is not directly engaged. This makes it a safer approach for gathering initial information. However, the limitation is that the data collected might not be as current or detailed as that obtained through active methods.
Both active and passive reconnaissance play vital roles in the enumeration process, which involves systematically gathering detailed information about a target’s network, systems, and services. Active methods provide comprehensive and accurate data but come with the risk of detection, while passive methods offer a stealthy way to gather information, albeit with potential gaps in the completeness and accuracy of the data. Combining both approaches can provide a balanced and effective reconnaissance strategy, leveraging the strengths of each method to gain a thorough understanding of the target environment.
In this blog, we are going to talk about the Active Recon methods for the common services that run on a web server.
1) FTP
File Transfer Protocol (FTP) is a standard network protocol used for the transfer of files between a client and a server over a computer network. Developed in the early 1970s, FTP allows users to upload, download, and manage files on a remote server. It operates on the application layer of the Internet protocol suite and is one of the oldest protocols still in use today.
FTP uses two main ports to establish connections and transfer data: port 21 for the command/control connection and port 20 for the data connection. The control connection is used to send commands from the client to the server and to receive responses, while the data connection is used to actually transfer the files. This dual-connection mechanism is one of the defining characteristics of FTP.
Here’s a basic overview of how FTP works:
* Connection Establishment: The FTP client initiates a connection to the FTP server on port 21. This creates the control connection, which remains open for the duration of the session. The client and server exchange commands and responses over this connection.
• User Authentication: Once the control connection is established, the client sends a username and password to the server for authentication. If the credentials are correct, the server grants access to the requested resources.
• Command Transmission: The client can send various commands over the control connection to navigate directories, list files, and initiate file transfers. Common commands include LIST (to list directory contents), RETR (to download a file), and STOR (to upload a file).
• Data Transfer: When a file transfer command is issued, a separate data connection is established, typically using port 20. The server opens a port and the client connects to it for the duration of the file transfer. Once the file transfer is complete, the data connection is closed, but the control connection remains open for additional commands and transfers.
• Session Termination: After completing the necessary file operations, the client sends a QUIT command to the server, closing the control connection and ending the session.
FTP can operate in two modes: active and passive. In active mode, the client opens a random port and waits for the server to connect back to the client’s specified port for data transfer. In passive mode, the server opens a random port and waits for the client to connect to it, which is useful for clients behind firewalls or NATs.
While FTP is effective for transferring files, it has notable security weaknesses. The protocol transmits data, including usernames and passwords, in plain text, making it vulnerable to interception and eavesdropping. To address this, secure versions like FTPS (FTP Secure) and SFTP (SSH File Transfer Protocol) have been developed, which encrypt the data transfer to enhance security.
Footprinting FTP:
a) We can use nmap scripts to fetch the ftp version and look at the misconfigurations it might have.
nmap <ip> -p21 –sC -sV
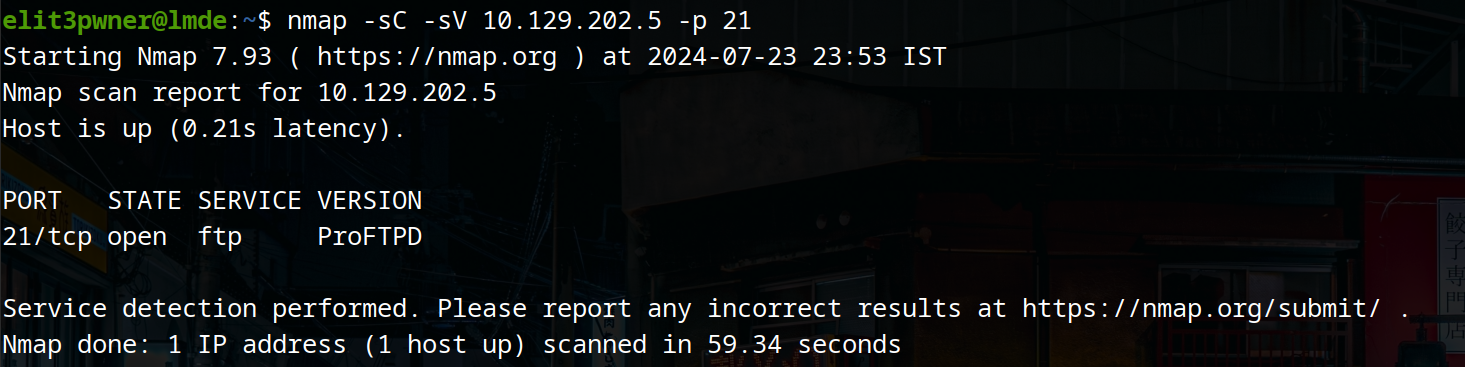
b) We can check for anonymous account logins. This misconfiguration is common and easy to look for.
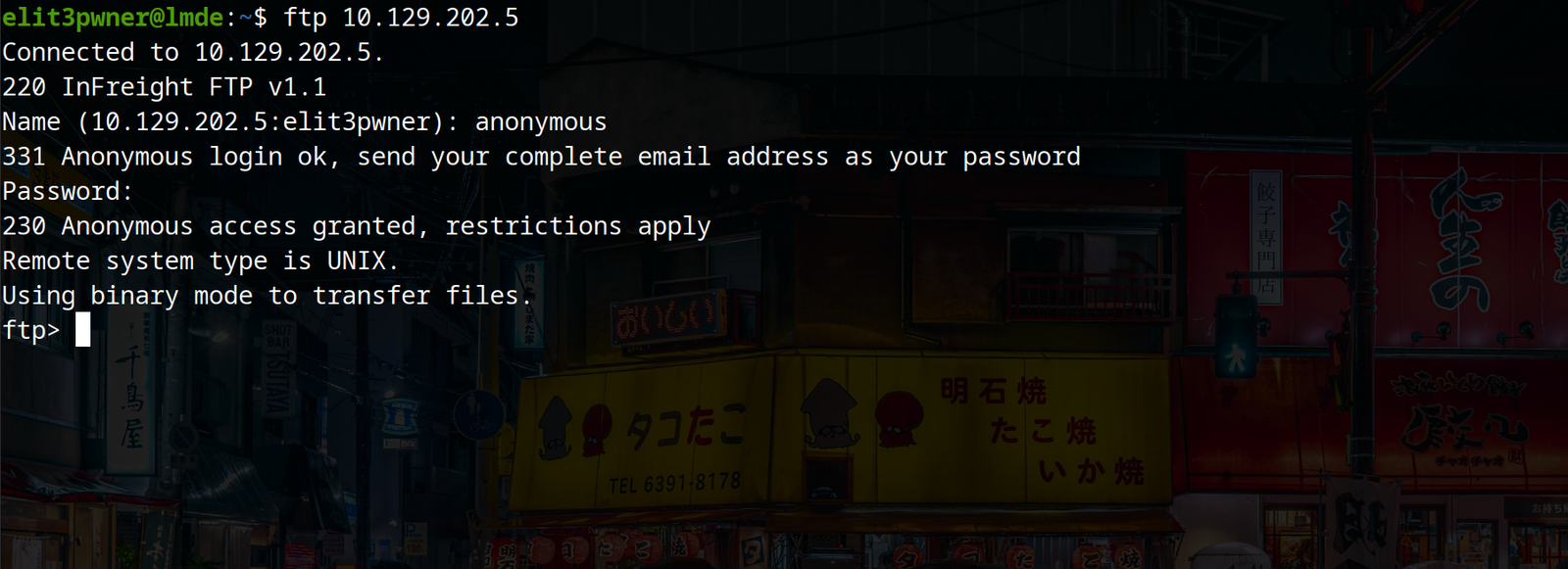
c) we can use commands like ls, cd, pwd to list, change directory and list the current directory. But, the best thing is, if you find an interesting file you can download it using get command. The syntax is:
get <filename>
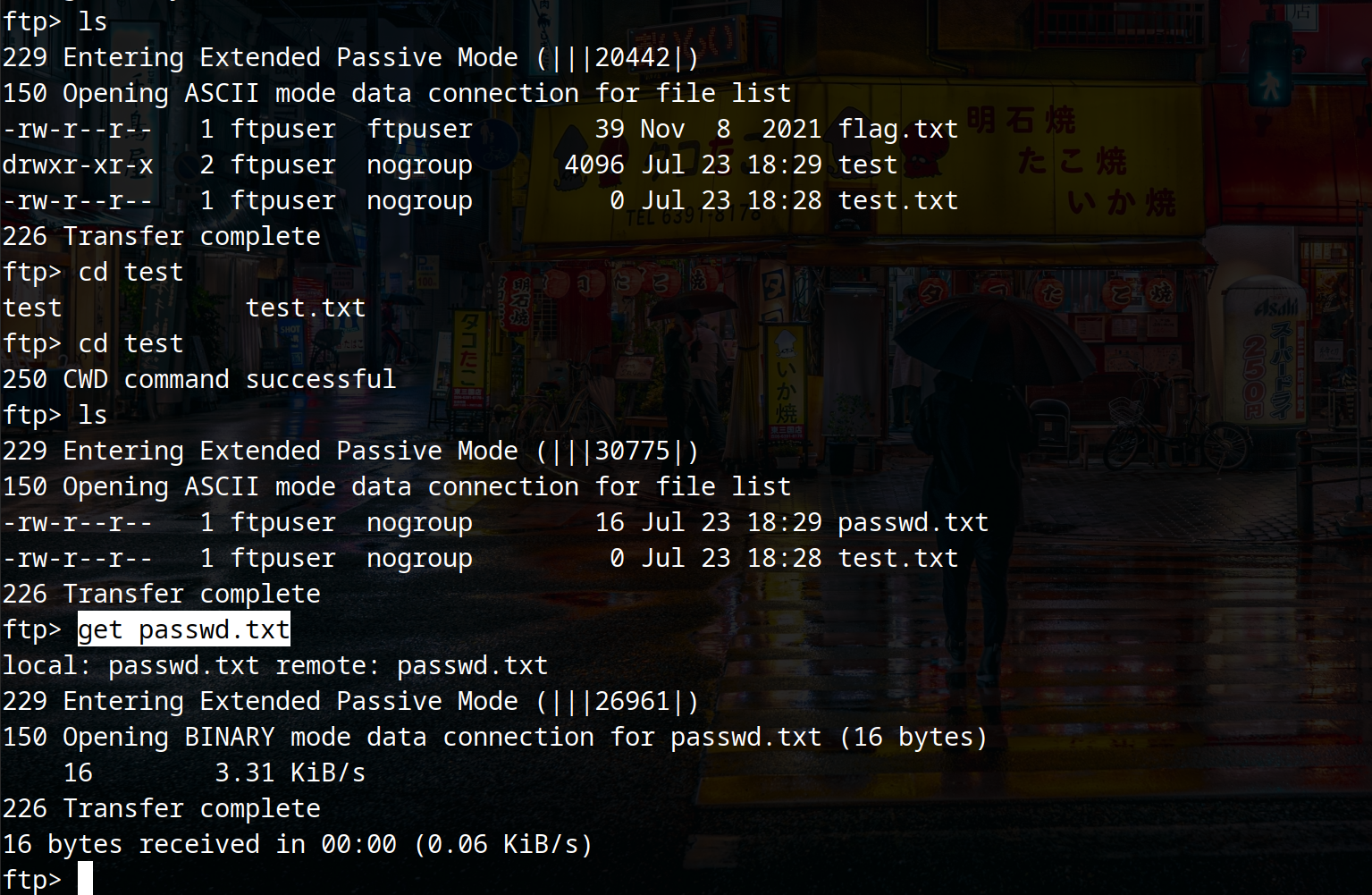
2) SMB
Server Message Block (SMB) is a network protocol primarily used for providing shared access to files, printers, and serial ports between nodes on a network. Developed by IBM in the mid-1980s and later enhanced by Microsoft, SMB operates on the application layer of the OSI model and enables communication between computers in a local network or over the Internet.
SMB typically uses port 445 for direct TCP/IP connections. Previously, it could also operate on port 139 via NetBIOS over TCP/IP, but modern implementations generally prefer the direct port 445 connection for improved performance and security.
Here’s a detailed explanation of how SMB works:
Session Establishment: An SMB client initiates a connection to the SMB server using port 445. During this handshake, the client and server negotiate the version of the SMB protocol to use (SMB 1.0, SMB 2.0, SMB 3.0, etc.). This negotiation step ensures compatibility and optimizes the protocol features based on the supported versions.
User Authentication: After establishing a session, the client must authenticate with the server. SMB supports various authentication mechanisms, including NTLM (NT LAN Manager) and Kerberos. Once authenticated, the client is granted access to shared resources based on the permissions configured on the server.
Resource Access: The client can now access shared resources such as files, directories, printers, and named pipes. SMB commands are used to perform various operations like opening files, reading and writing data, and creating or deleting directories. Each operation is handled as a discrete request-response transaction between the client and server.
File and Printer Sharing: One of the primary uses of SMB is file sharing. Clients can map network drives to shared folders, allowing seamless access to files as if they were located on the local machine. For printer sharing, SMB enables clients to send print jobs to printers shared on the network, facilitating centralized printer management.
Communication and Notifications: SMB also supports inter-process communication (IPC) mechanisms, allowing applications and services to exchange data. Additionally, SMB includes features for sending notifications about changes to shared resources, such as file modifications, which helps in synchronizing activities across multiple clients.
SMB has evolved significantly over the years, with major improvements in performance, security, and functionality. SMB 2.0, introduced with Windows Vista, brought enhancements like reduced command overhead, improved scalability, and better support for large files. SMB 3.0, released with Windows 8 and Windows Server 2012, introduced features like end-to-end encryption, improved resiliency through multi-channel support, and performance optimizations for virtualized environments.
Despite its benefits, SMB has had its share of security challenges. Vulnerabilities in SMB, particularly in older versions like SMB 1.0, have been exploited in several high-profile cyberattacks, such as the WannaCry ransomware attack. Consequently, it is recommended to disable SMB 1.0 and use more secure versions (SMB 2.0 or later) with encryption and strong authentication methods to mitigate security risks.
In summary, SMB is a versatile and widely used protocol for sharing resources and enabling communication between devices on a network. Its continued evolution and enhancements ensure it remains a critical component of modern network infrastructure, providing robust support for file and printer sharing, among other capabilities.
Footprinting SMB
a) One of the most famous tools for testing SMB is “`smbclient“`. You can use smbclient to list the available shares using authentication and even anonymous shares.
Syntax: smbclient -N -L //<ip>/
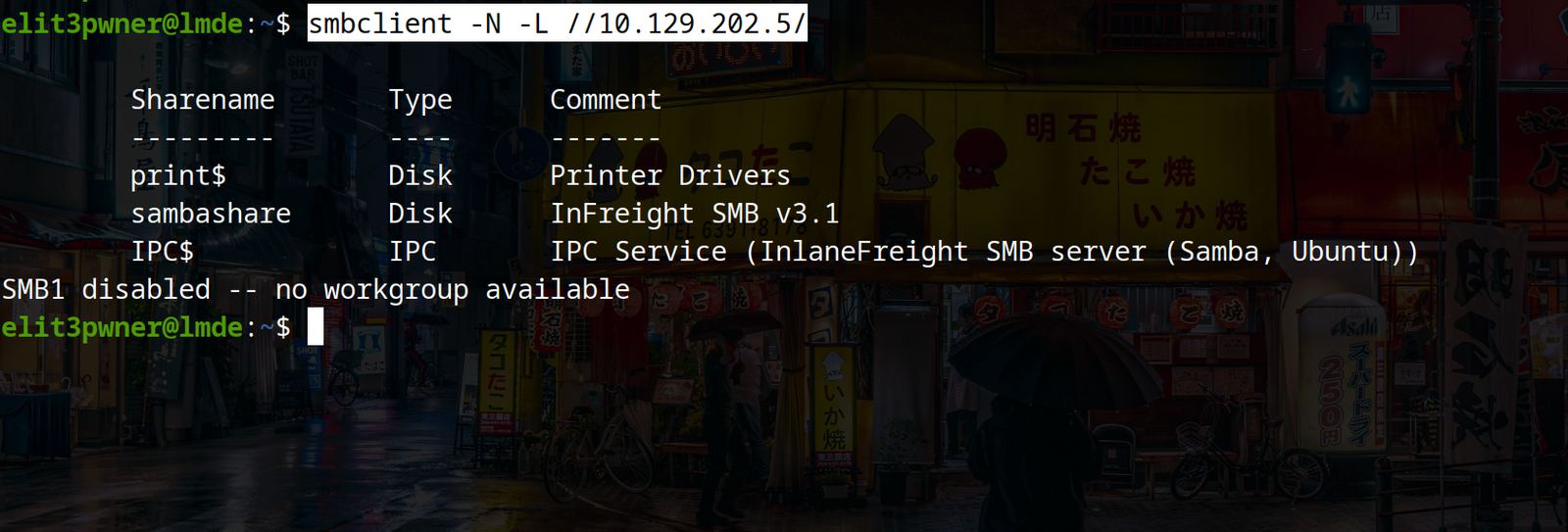
now, to interact with the available shares, use the following command:
smbclient -N //<ip>/<share>
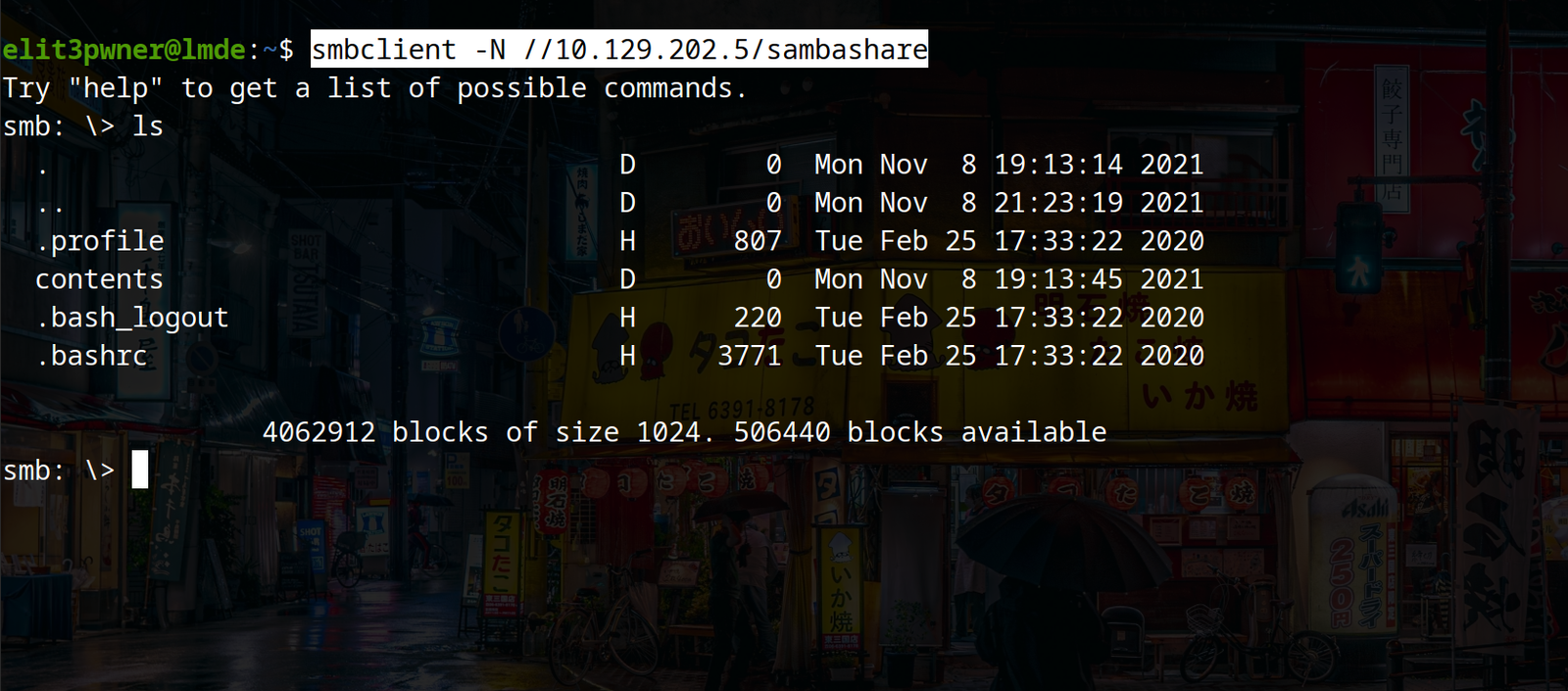
now, we can use commands like ls, cd to navigate and get command to download any file available on the share.
Syntax: get <filename>
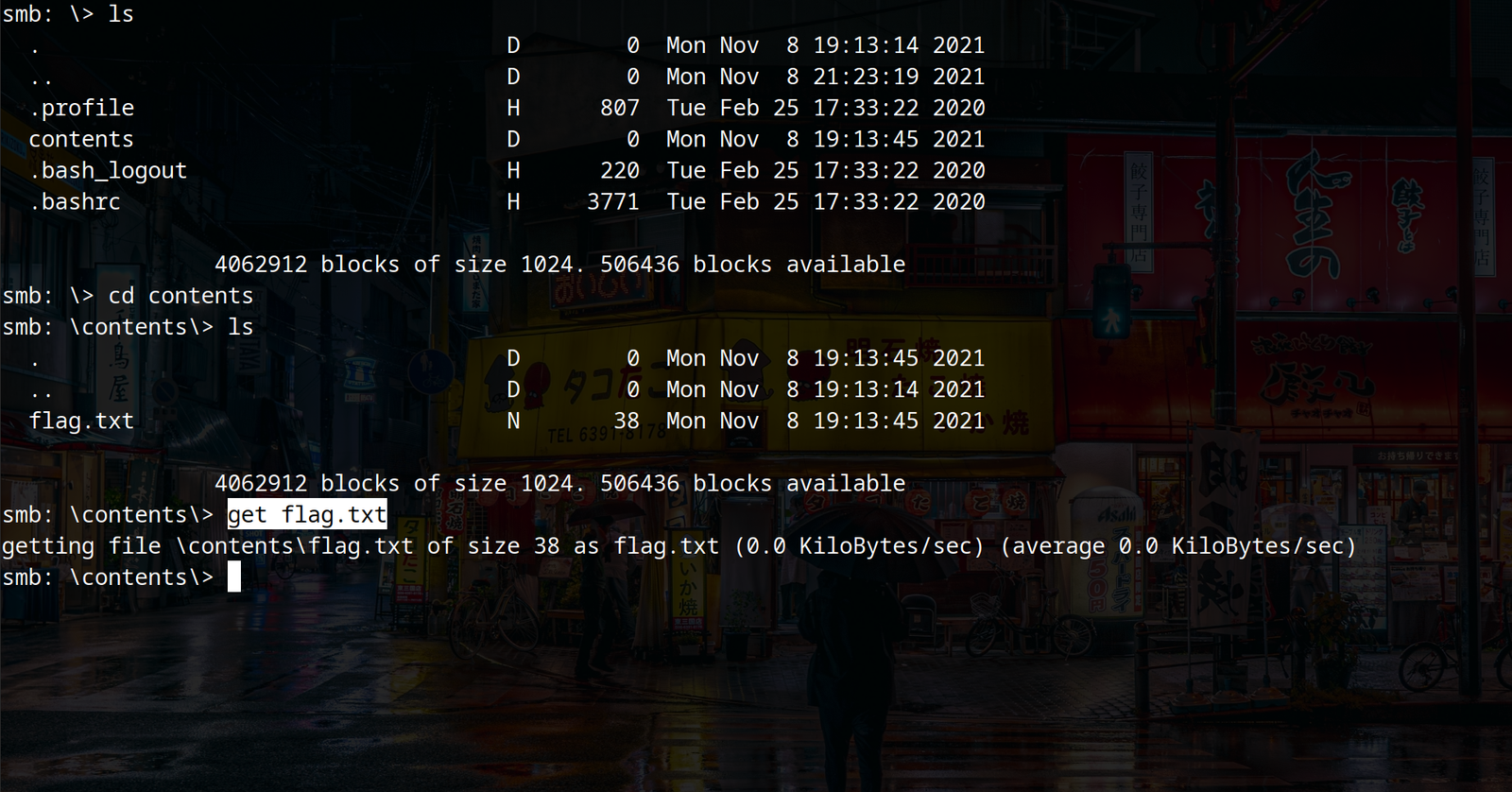
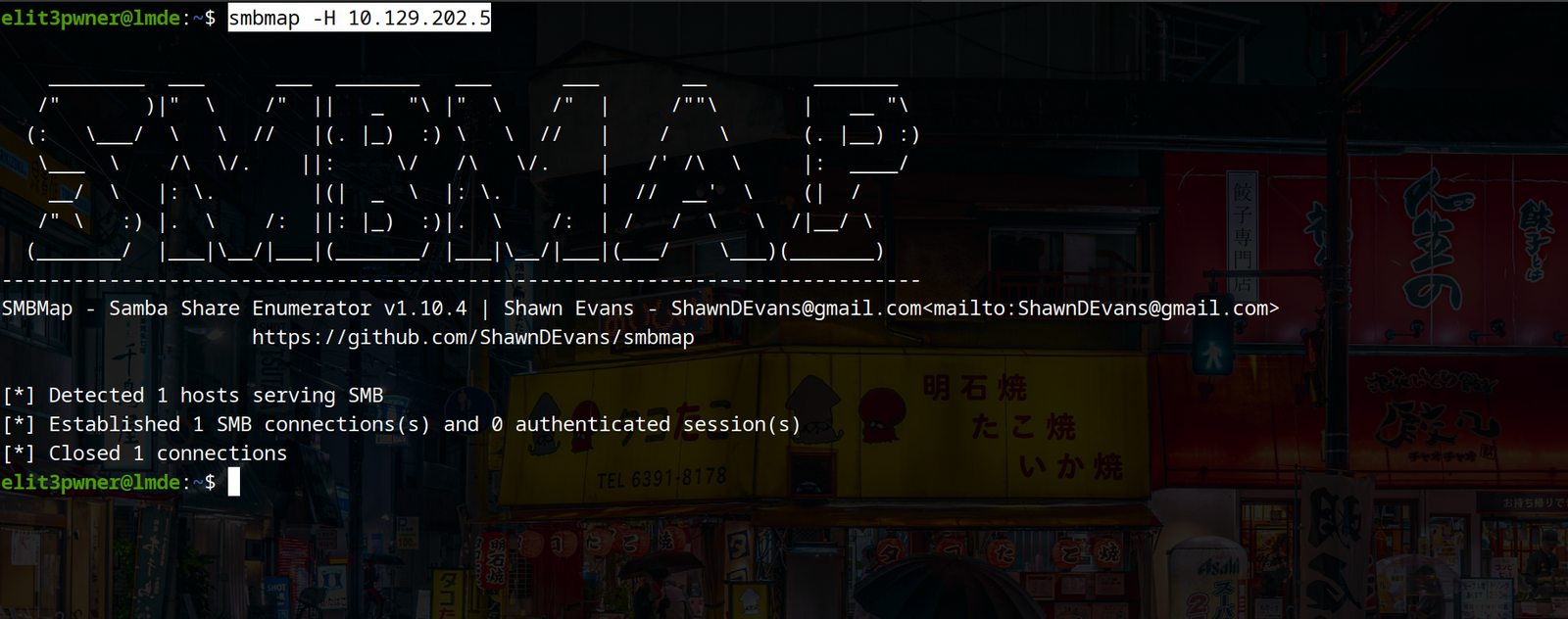
b) Another tool we can use is smbmap
syntax: smbmap -H <ip>
3) NFS
Network File System (NFS) is a distributed file system protocol developed by Sun Microsystems in the 1980s, allowing users to access files over a network as if they were on a local disk. NFS enables seamless file sharing and is particularly popular in Unix and Linux environments, though it is also supported on other platforms like Windows.
NFS uses multiple ports for communication. The primary port used by NFS is port 2049 for the NFS daemon, but it also relies on other services like the Portmapper (port 111), and potentially other dynamically assigned ports for related services such as mountd and nlockmgr.
Here’s an overview of how NFS works:
Client-Server Architecture: NFS operates on a client-server model where the NFS server shares its file systems and the NFS client mounts these shared file systems. Once mounted, the client can access the files as if they were part of its own local directory structure.
Mounting File Systems: The process begins with the client sending a mount request to the NFS server. This request is initially handled by the Portmapper service, which directs it to the appropriate service handling the mount requests (usually mountd). The server then verifies the client’s access rights and allows the client to mount the requested file system.
Remote Procedure Calls (RPC): NFS relies on the Remote Procedure Call (RPC) protocol for communication. RPC enables the client to execute commands on the server as if they were local procedure calls. The client’s NFS requests are translated into RPC calls that the server executes, returning the results to the client.
File Operations: Once the file system is mounted, the client can perform various file operations such as reading, writing, creating, and deleting files. These operations are executed over the network, with the client issuing RPC calls to the server for each operation. The server processes these requests and returns the appropriate responses.
Stateless Protocol: NFS is designed as a stateless protocol, meaning each client request contains all the necessary information for the server to process it independently. This design simplifies server implementation and improves robustness since the server does not need to maintain any session state between requests.
Versions and Enhancements: NFS has undergone several versions, each bringing improvements in performance, security, and functionality. NFSv3, introduced in 1995, added support for 64-bit file sizes and better error handling. NFSv4, released in 2000, brought significant enhancements, including stateful operations, support for strong authentication, integrated file locking, and improved performance over wide area networks (WANs).
Security: NFS security has evolved to support various authentication mechanisms. NFSv3 relies on UNIX-based authentication (UIDs and GIDs), which can be insecure over untrusted networks. NFSv4, however, introduced support for stronger security measures, including Kerberos authentication and integrated access control lists (ACLs), providing better security and access control.
Performance and Scalability: NFS is designed to be highly performant and scalable, capable of supporting large-scale environments with many clients and high I/O demands. Features like asynchronous writes, read-ahead caching, and delegations (in NFSv4) help optimize performance and reduce latency.
In summary, NFS is a powerful and flexible protocol for network-based file sharing, providing seamless access to remote file systems. Its stateless design, reliance on RPC, and continued evolution through multiple versions make it a robust choice for distributed computing environments, particularly in Unix and Linux systems. With improvements in security and performance, NFS remains a widely used and reliable solution for network file sharing.
Footprinting NFS
Now, the best part about NFS is, we can mount the available file system on our own device and browse the features just like a normal directory on our own system.
a) To show available NFS shares:
showmount -e <ip>
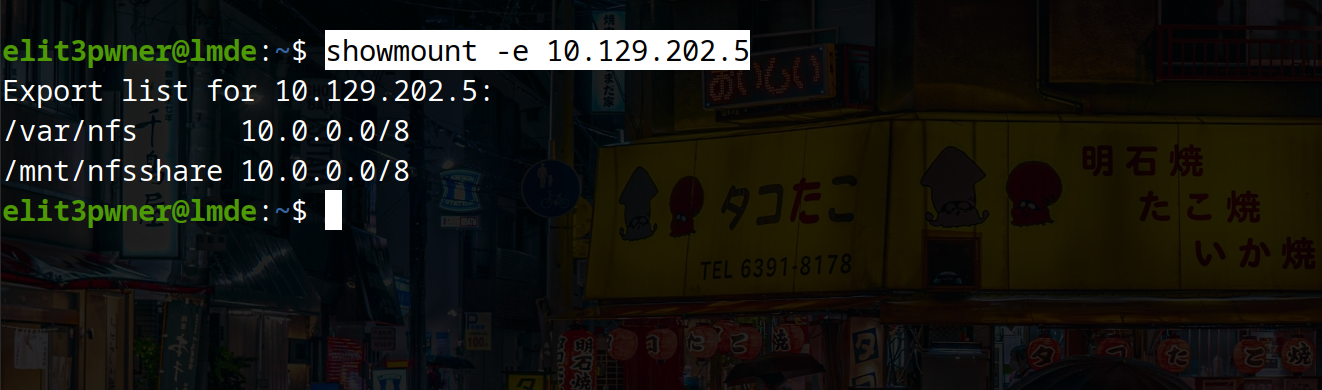
b) now, use following commands to mount the available shares:
mkdir test-dir → This will serve as the directory on which the shares will be mounted on.
sudo mount -t nfs <ip>:/ ./test-dir/ -o nolock → This is the command to mount the shares.
cd test-dir → we can now move into the directory and browse it normally.
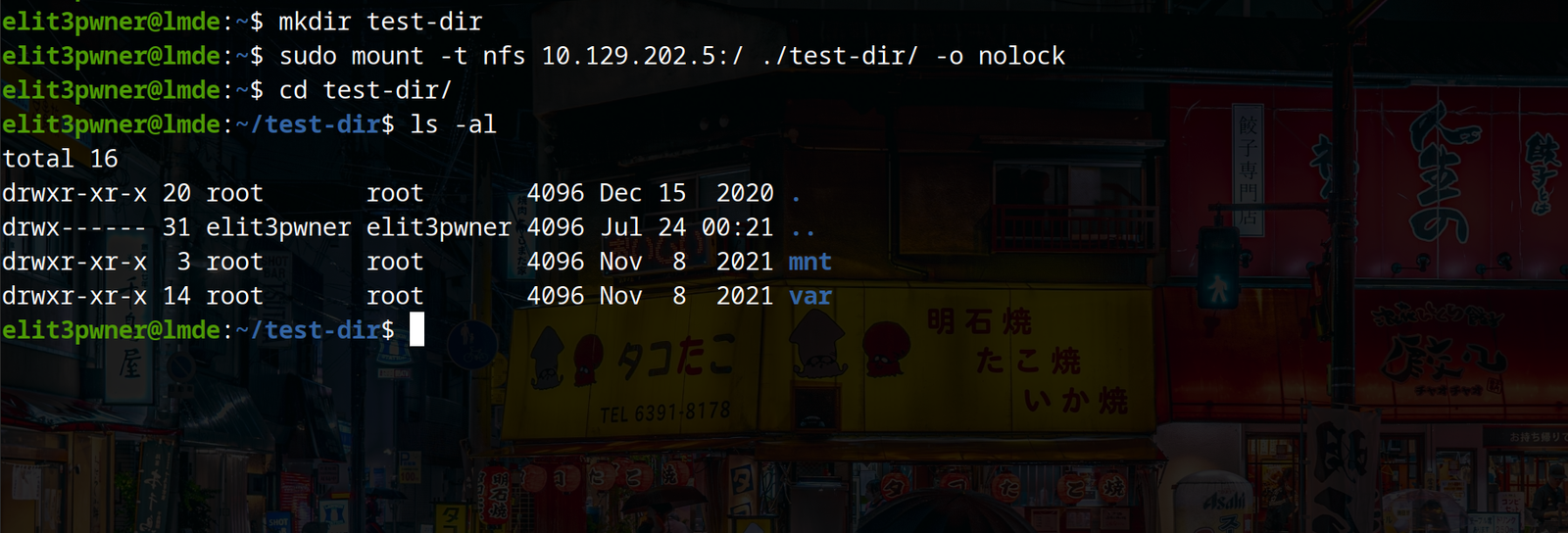
c) To unmount the share that we mounted, use the following command:
sudo umount ./test-dir
4) IMAP/POP3
Internet Message Access Protocol (IMAP) and Post Office Protocol version 3 (POP3) are two widely used protocols for retrieving email from a mail server. Both protocols allow users to access their emails, but they do so in different ways, each with its own set of features and advantages.
IMAP (Internet Message Access Protocol)
IMAP, currently at version 4 (IMAP4), is a protocol that allows users to access and manage their email directly on the mail server. It uses port 143 for non-encrypted connections and port 993 for SSL/TLS encrypted connections. Here’s how IMAP works and its key features:
Server-Based Storage: IMAP stores emails on the server, allowing users to view and manage their messages without downloading them to their local device. This means emails can be accessed from multiple devices, as the server always has the latest copy.
Synchronization: IMAP synchronizes emails across all devices connected to the mail account. Actions such as reading, deleting, or moving emails are updated in real-time on the server and reflected on all devices.
Folder Support: IMAP allows users to create, delete, and rename folders on the server. This organizational feature helps in managing emails efficiently and keeps the same structure across all devices.
Partial Download: IMAP can download only the headers of emails initially, allowing users to preview messages and decide whether to download the entire content. This can save bandwidth and time, especially with large emails.
Multiple Clients: Since emails are stored on the server, multiple clients can access the same email account simultaneously. This is useful for shared or collaborative email accounts.
Search Capabilities: IMAP allows searching through emails on the server, making it easier to find specific messages without downloading all emails.
POP3 (Post Office Protocol version 3)
POP3 is an older protocol for retrieving email from a mail server. It uses port 110 for non-encrypted connections and port 995 for SSL/TLS encrypted connections. Here’s how POP3 works and its key features:
Local Storage: POP3 downloads emails from the server to the local device and, by default, deletes them from the server. This means emails are primarily stored on the device, and access from multiple devices can be cumbersome as each device would need to download its own copy of the emails.
Single Device Focus: POP3 is designed for accessing email from a single device. Once emails are downloaded, they are stored locally and typically not available on other devices.
Simple Protocol: POP3 is straightforward and easy to implement. It works well for users who prefer to manage their emails offline or need to free up server space by downloading and deleting emails from the server.
Limited Synchronization: Unlike IMAP, POP3 does not synchronize email actions across devices. If an email is read or deleted on one device, this change is not reflected on other devices.
Offline Access: Since emails are downloaded and stored locally, they can be accessed without an internet connection. This is beneficial for users who need to access their emails while offline.
Choosing Between IMAP and POP3
The choice between IMAP and POP3 depends on the user’s needs and email management preferences:
IMAP is ideal for users who access their email from multiple devices or locations, as it provides real-time synchronization and keeps all emails on the server. It is also better for users who require advanced email management features, such as folder organization and server-side search.
POP3 is suitable for users who prefer to store their emails locally and primarily use a single device to access their email. It can also be beneficial for users with limited server storage, as emails are downloaded and removed from the server.
In summary, IMAP and POP3 are both essential protocols for email retrieval, each catering to different user needs. IMAP offers flexibility, synchronization, and server-based management, while POP3 provides simplicity and local storage for users who prefer offline access. Understanding the differences between these protocols helps users choose the best option for their email access requirements.
Footprinting IMAP/POP3
a) we can use the following nmap command to gather information about IMAP/POP3:
sudo nmap <ip> -sV -p110,143,993,995 -sC
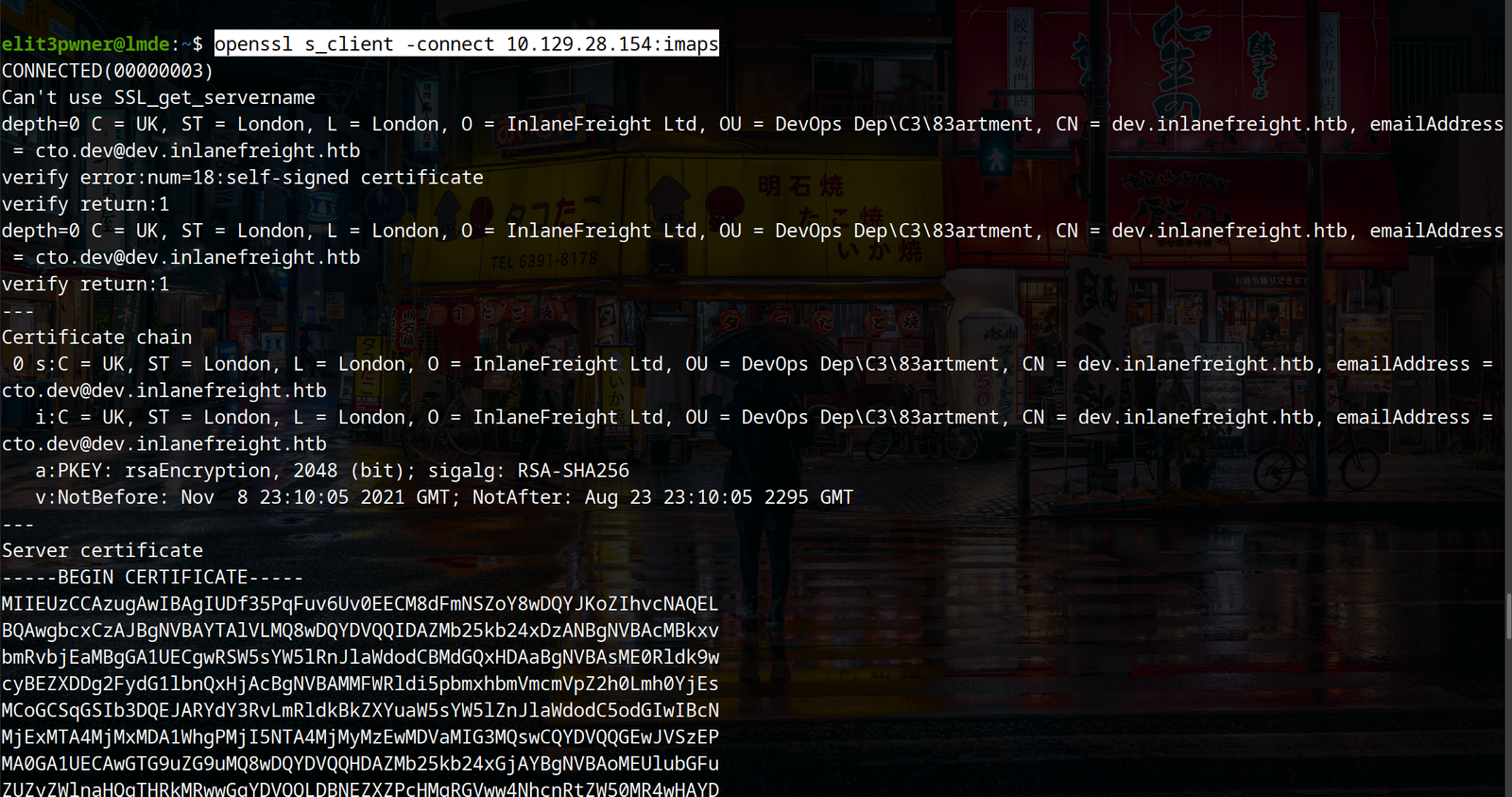
b) we can connect to IMAP and POP3 using the “`openssl“`. Follow the following commands to connect to each respective service:
Connecting to IMAP:
openssl s_client -connect <ip>:imaps
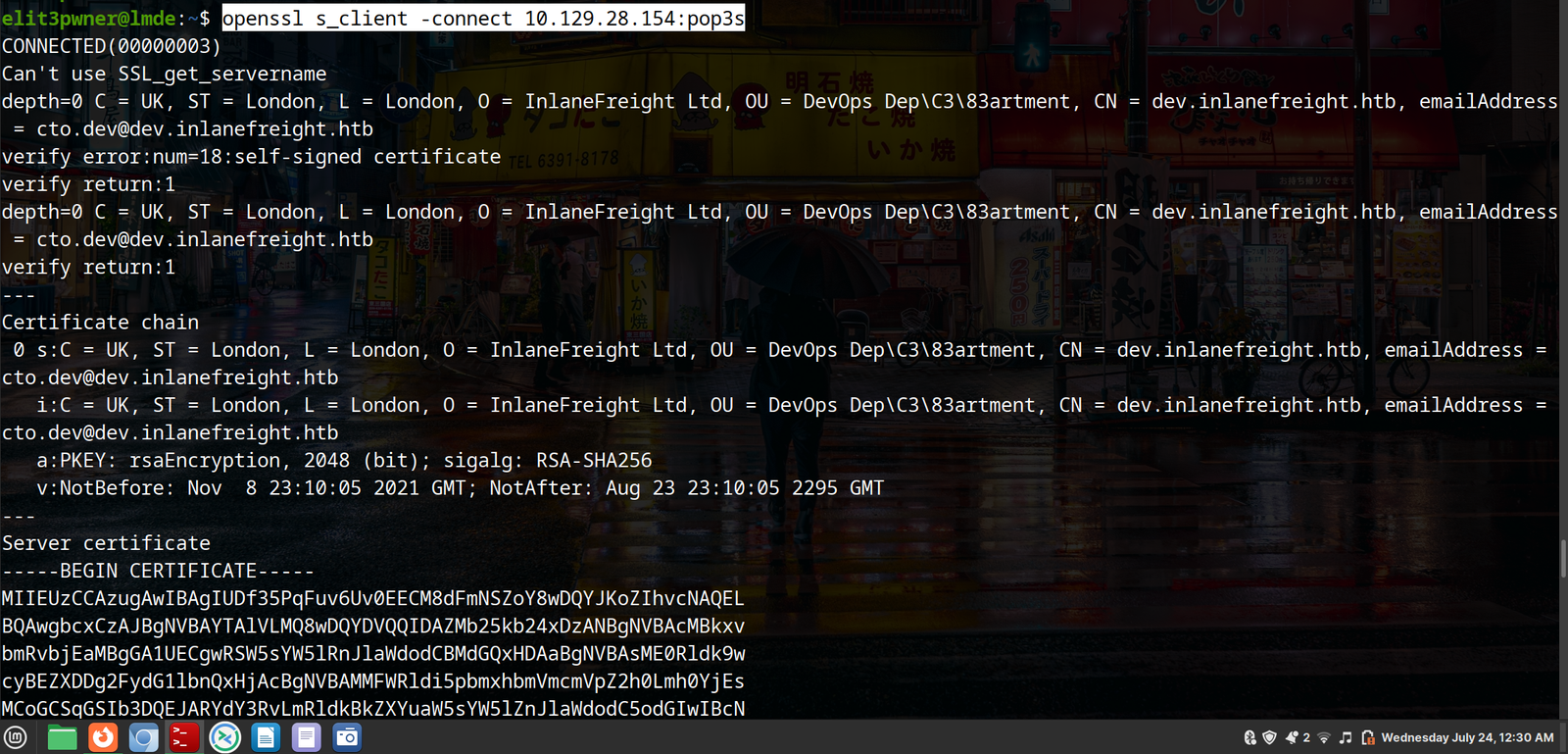
Connecting to POP3:
openssl s_client -connect <ip>:pop3s
c) After you have valid credentials to authenticate to IMAP/POP3 service, you can use commands to navigate the service, read, create, delete, rename emails.
IMAP Commands
IMAP Commands
|
Command
|
Description
|
|
1 LOGIN username password
|
User’s login.
|
|
1 LIST “” *
|
Lists all directories.
|
|
1 CREATE “INBOX”
|
Creates a mailbox with a specified name.
|
|
1 DELETE “INBOX”
|
Deletes a mailbox.
|
|
1 RENAME “ToRead” “Important”
|
Renames a mailbox.
|
|
1 LSUB “” *
|
Returns a subset of names from the set of names that the User has declared as being active or subscribed.
|
|
1 SELECT INBOX
|
Selects a mailbox so that messages in the mailbox can be accessed.
|
|
1 UNSELECT INBOX
|
Exits the selected mailbox.
|
|
1 FETCH <ID> all
|
Retrieves data associated with a message in the mailbox.
|
|
1 CLOSE
|
Removes all messages with the Deleted flag set.
|
|
1 LOGOUT
|
Closes the connection with the IMAP server.
|
Use the link to know about more imap commands: https://www.atmail.com/blog/imap-commands/
POP3 Commands
|
Command
|
Description
|
|
USER username
|
Identifies the user.
|
|
PASS password
|
Authentication of the user using its password.
|
|
STAT
|
Requests the number of saved emails from the server.
|
|
LIST
|
Requests from the server the number and size of all emails.
|
|
RETR id
|
Requests the server to deliver the requested email by ID.
|
|
DELE id
|
Requests the server to delete the requested email by ID.
|
|
CAPA
|
Requests the server to display the server capabilities.
|
|
RSET
|
Requests the server to reset the transmitted information.
|
|
QUIT
|
Closes the connection with the POP3 server.
|
|
TOP [message index] [num lines to return]
|
Returns the headers and top X lines of a message by message index (from LIST). Can be used to display the 1st few lines of a message. Headers are always returned.
|
Use the link to know more about POP3 commands: https://kb.datamotion.com/?ht_kb=how-to-utilize-pop3-protocol-to-access-datamotion-securemail-and-direct-accounts
5) SNMP
Simple Network Management Protocol (SNMP) is a widely used protocol for managing devices on IP networks. Developed in the late 1980s, SNMP allows network administrators to monitor, manage, and configure network devices, including routers, switches, servers, workstations, printers, and more. It operates primarily on the application layer of the OSI model.
SNMP typically uses UDP port 161 for sending requests from the manager to the managed devices (agents) and UDP port 162 for receiving notifications (traps) from agents. Here’s a detailed overview of how SNMP works and its key components:
How SNMP Works
Architecture: SNMP follows a client-server architecture, where the server is known as the SNMP manager and the clients are known as SNMP agents. The SNMP manager is a central system that monitors and controls the network, while SNMP agents are software components on network devices that report information to the manager.
Communication: The SNMP manager and agents communicate using a standardized set of messages. The manager sends requests to the agents to retrieve or modify information, and agents respond with the requested data. Additionally, agents can send unsolicited notifications, called traps or informs, to the manager to report significant events or changes in status.
Management Information Base (MIB): Each SNMP-managed device contains a Management Information Base (MIB), which is a hierarchical database of objects representing various aspects of the device. These objects are defined by object identifiers (OIDs) and can include information such as device configuration, performance metrics, and error statuses. The MIB is standardized, ensuring consistent management across different devices and manufacturers.
Operations: SNMP supports several key operations:
GetRequest: The manager requests the value of specific variables from an agent.
SetRequest: The manager sets the value of specific variables on an agent.
GetNextRequest: The manager retrieves the next variable in the MIB hierarchy.
GetBulkRequest: The manager retrieves large blocks of data from an agent.
Response: The agent responds to the manager’s requests with the requested data.
Trap: The agent sends an unsolicited alert to the manager about a significant event.
InformRequest: Similar to traps, but the manager sends an acknowledgment back to the agent.
SNMP Versions
SNMP has evolved through several versions, each offering different features and security improvements:
SNMPv1: The original version, introduced in 1988, provided basic management capabilities but had limited security features, relying on community strings (simple passwords) for authentication.
SNMPv2c: Introduced in the early 1990s, this version improved performance and introduced new operations like GetBulkRequest. However, it still relied on community strings for security.
SNMPv3: The most secure and widely used version, SNMPv3, introduced robust security features, including authentication, encryption, and access control. It supports message integrity, ensuring that messages are not tampered with in transit, and privacy, ensuring that messages are encrypted.
Advantages of SNMP
Scalability: SNMP is highly scalable, capable of managing networks of all sizes, from small local networks to large enterprise environments.
Flexibility: The protocol is flexible and can be used to monitor a wide range of devices and parameters, making it suitable for diverse network environments.
Standardization: SNMP is an open standard, ensuring interoperability between devices from different manufacturers and providing a consistent approach to network management.
Real-Time Monitoring: With SNMP, administrators can monitor network performance and status in real-time, quickly identifying and addressing issues as they arise.
Automation: SNMP supports automation of routine network management tasks, reducing the need for manual intervention and increasing efficiency.
Use Cases of SNMP
Network Monitoring: SNMP is widely used to monitor network performance, including bandwidth usage, error rates, and device statuses.
Fault Management: SNMP traps allow administrators to receive alerts about network faults, enabling rapid response to issues.
Configuration Management: SNMP enables remote configuration of network devices, simplifying management and deployment.
Performance Analysis: SNMP data can be used to analyze network performance trends and optimize network resources.
In summary, SNMP is a powerful and versatile protocol for network management, providing essential capabilities for monitoring, configuring, and controlling network devices. Its scalability, flexibility, and real-time monitoring capabilities make it an indispensable tool for network administrators.
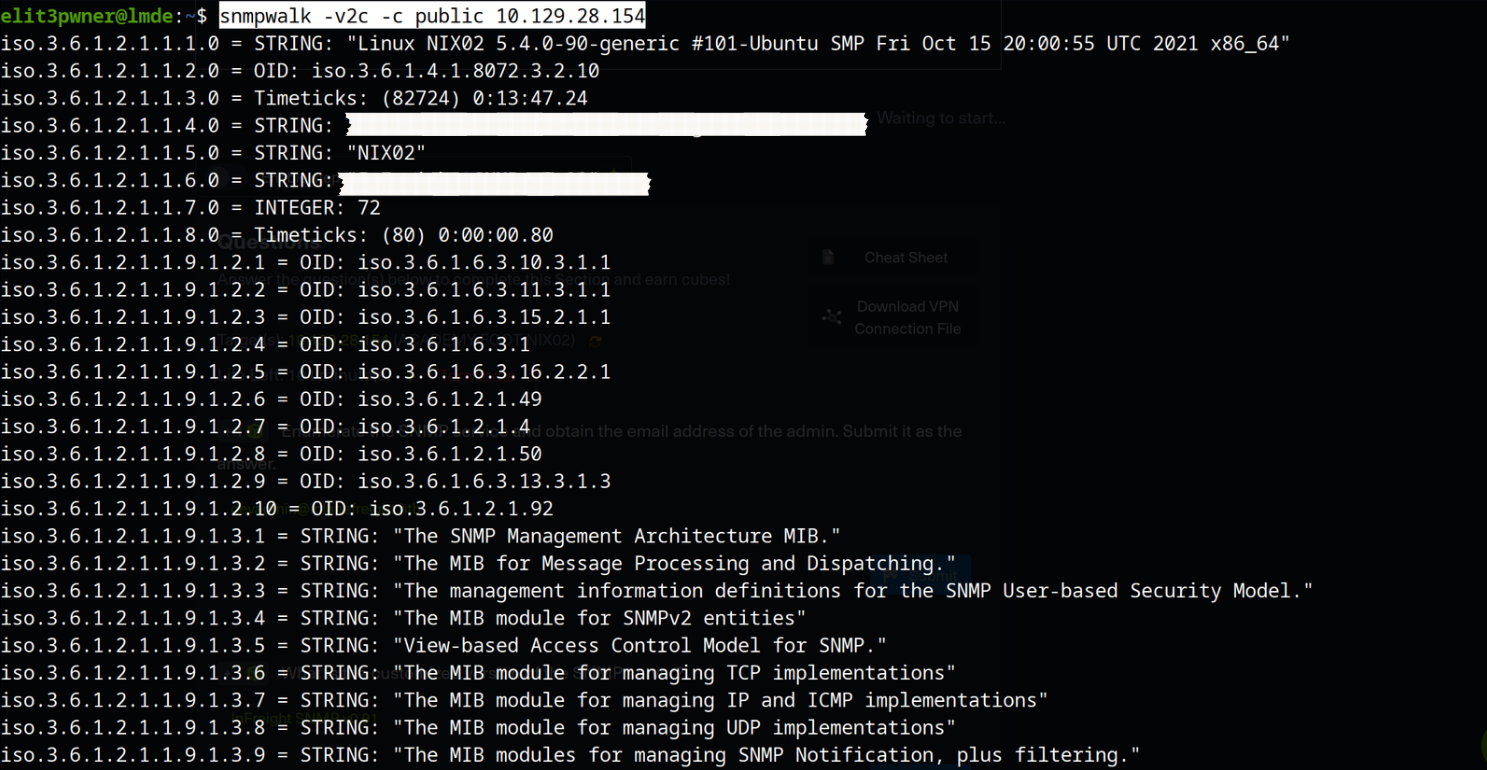
Footprinting SNMP: The most common and famous tool for footprinting SNMP is snmpwalk.
a) We can use snmpwalk to footprint the service. snmpwalk is used to enumerate information about the community string we found.
snmpwalk -v2c -c <string> <ip>
Our LinkedIn: https://www.linkedin.com/company/aspiainfotech/mycompany/





