Malware is a pervasive threat that impacts individual, businesses, and governments equally in today’s digital environment. Malware can have a variety of potentially lethal effects, such as secretly stealing important data or locking down critical systems with ransomware. This blog seeks to define malware, examine its history, and emphasize the importance of malware analysis in preventing these dangers. We will also examine how automation is transforming the industry by enabling faster and more precise detection and analysis of potentially harmful software.
-
Understanding CI/CD: The Backbone of Modern Software Delivery
Defining CI/CD:
A CI/CD pipeline is an automated workflow that moves code changes from development to production. It is made up of several stages that automatically build, test, and deploy code. By streamlining these processes, a CI/CD pipeline enables rapid, reliable software delivery.
- Continuous Integration (CI): Continuous Integration (CI) is a software development practice where developers frequently merge their code changes into a shared repository. Each integration triggers an automated build and testing process. The goal is to catch issues early and reduce the risk of integration problems let’s understand this in terms.
- Code Integration: Developers commit code to a shared version control repository (like Git) multiple times a day. CI tools (e.g., Jenkins, GitLab CI) automatically detect these changes and initiate a new build.
-
- Automated Build and Testing: Once code is integrated, the CI pipeline kicks off. The code is compiled, dependencies are resolved, and automated unit and integration tests are run. This ensures that newly added code doesn’t introduce bugs or break existing functionality.
- Feedback Loop: If a build or test fails, the team is immediately alerted. Developers can quickly fix issues before they grow into bigger problems.
CI helps maintain a stable codebase by catching issues early. Instead of waiting until the end of a project to integrate and test everything, CI ensures ongoing code quality. However, this speed can introduce security risks if vulnerabilities are not addressed during these early stages.
- Continuous Delivery/Deployment (CD): Continuous Delivery (CD) extends CI by automating the process of preparing code for release. Continuous Deployment takes it further by automatically deploying every code change that passes testing into production.
-
- Staging and Release Preparation: Once code passes the CI phase, it moves into the CD pipeline. Here, additional tests (like performance and security tests) are run. The code is then packaged and made ready for deployment.
- Deployment Process: In Continuous Delivery, the deployment is manual but fully prepared and automated up to the release point. Continuous Deployment automates this entirely, pushing every validated change into production.
The CI/CD pipeline accelerates software delivery but also introduces potential security risks. Automated processes, increased integration points, and rapid deployments create more opportunities for attackers to exploit. Security is critical for these reasons:
- Expanded Attack Surface: The frequency of code integrations and automated deployments broadens the attack surface, providing mor
- e entry points for potential threats.
- Vulnerability at Every Stage: From code commits to deployments, each phase is susceptible to attacks. For example, injecting malicious code during integration or exploiting insecure dependencies during deployment can have devastating consequences.
- Risks of Human Error and Misconfigurations: Even minor misconfigurations in build and deployment processes can lead to significant security vulnerabilities, such as granting excessive privileges or exposing sensitive data.
-
Common Security Risks in CI/CD Pipelines:
Each phase of the CI/CD pipeline introduces its own security challenges. Below is a summary of these phases, the associated risks, and recommended mitigation strategies:
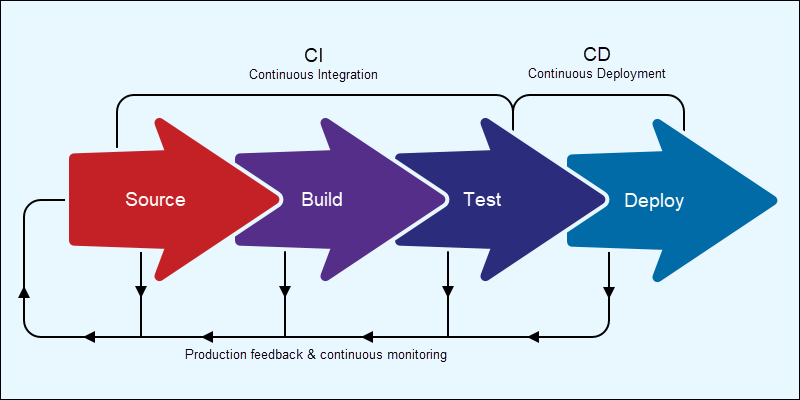
Phase 1: Source Code
- Threats:
- Malicious Code Insertion: An attacker may introduce a backdoor into the source code, such as a logic bomb that triggers harmful actions under specific conditions.
- Weak Authentication and Access Control: Poor access controls can allow unauthorized personnel to modify code, potentially injecting vulnerabilities.
- Mitigation: Implement Static Application Security Testing (SAST) tools like SonarQube or Checkmarx to detect security flaws early. Enforce strict access controls using multi-factor authentication (MFA) and role-based access control (RBAC) to limit codebase access.
Phase 2: Build
- Threats:
- Insecure Configurations: Misconfigured build tools could introduce security weaknesses, such as outdated libraries vulnerable to known exploits.
- Compromised Build Servers: If a build server is misconfigured or lacks patches, attackers can exploit it to tamper with the software.
- Mitigation: Use secure configuration practices and automated validation tools like Checkov or Terraform Sentinel. These tools help enforce consistent, secure configurations across all builds.
Phase 3: Test
- Threats:
- Inadequate Test Coverage: Insufficient testing can leave vulnerabilities undetected. For example, failing to test for SQL injection could expose the application to serious threats.
- Insecure Testing Environments: Non-isolated or improperly configured test environments can expose sensitive data or introduce security weaknesses.
- Mitigation: Ensure comprehensive test coverage with tools like OWASP ZAP or BurpSuite and use securely isolated testing environments. Integrating automated security tests into the pipeline can detect flaws early and prevent insecure code from advancing to production.
Phase 4: Deploy
- Threats:
- Misconfigurations: Improper deployment settings, like leaving databases publicly accessible, can lead to data leaks or unauthorized access.
- Tampering with Automated Deployment Processes: Attackers could exploit vulnerabilities to inject malicious code during deployment.
- Mitigation: Implement secure deployment practices by enforcing RBAC and conducting automated configuration checks. Tools like Jenkins, GitLab CI, or CircleCI can be configured to verify deployment processes and prevent unauthorized access.
-
Securing the CI/CD Pipeline
Role-Based Access Control (RBAC): Establishing clear access controls limits who can make changes to the CI/CD pipeline. Adhering to the principle of least privilege reduces the risk of unauthorized access. Role definitions should be continuously reviewed and updated to align with organizational needs.
Integrating Security Testing into the CI/CD Workflow: Security checks must be embedded at every stage of the CI/CD pipeline to ensure that vulnerabilities are detected and addressed promptly. Automation tools like Jenkins, GitLab CI, and CircleCI enable security testing to run in tandem with build processes without slowing down development.
Best Practices in Securing CI/CD Pipelines:
- Shifting Security Left: Embedding security at the earliest stages of the pipeline (i.e., during code commits and builds) reduces the cost and complexity of fixing vulnerabilities later in the process.
- Continuous Monitoring and Alerts: Use advanced monitoring tools like Splunk or the ELK Stack (Elasticsearch, Logstash, Kibana) to detect anomalies and suspicious activity in real time.
- Automated Compliance Checks: Tools like Chef InSpec can be integrated to validate that code adheres to compliance standards like GDPR or HIPAA before reaching production.
-
Conclusion:
Securing the CI/CD pipeline is integral to the success of DevSecOps practices. By employing a strategic combination of tools, best practices, and continuous monitoring, organizations can unlock the potential of their CI/CD pipelines without sacrificing security. A resilient and protected CI/CD framework not only enhances software quality but also builds customer trust and provides a strong defence against increasingly sophisticated cyber threats.
In today’s fast-evolving software development landscape, the responsibility for security cannot rest solely on the shoulders of dedicated security teams; it’s a shared responsibility that must permeate every discipline within the organization. By implementing the strategies and tools outlined above businesses can build secure, agile, and compliant pipelines that foster innovation while maintaining stringent security measures.




