AI-Driven GRC TransformationIn today’s fast-paced business world, staying compliant while managing risks feels like walking a tightrope. I remember a time when our team would spend hours poring over regulatory updates and ensuring everything aligned perfectly with the rules. Despite their hard work, the sheer volume of information often left gaps that no human effort...
Introduction In today’s hyper-connected world, cybersecurity is no longer a luxury, it’s a necessity. As organizations move more of their operations online, they become prime targets for cyberattacks. Vulnerability management, the process of identifying, evaluating, and mitigating security weaknesses, is crucial to protecting sensitive data and maintaining business continuity. However, traditional methods of vulnerability management...
Malware is a pervasive threat that impacts individual, businesses, and governments equally in today’s digital environment. Malware can have a variety of potentially lethal effects, such as secretly stealing important data or locking down critical systems with ransomware. This blog seeks to define malware, examine its history, and emphasize the importance of malware analysis in...
Learn how DevSecOps ensures quicker, safer releases by seamlessly integrating security into the software lifecycle, from development to deployment. Security is now an essential component of software development and cannot be ignored in the quickly changing field. Organizations are being forced to reconsider how they incorporate security into their operations due to the increase in...
Introduction Malware analysis is playing a crucial role for safeguarding the digital landscape, guarding individuals, businesses, and governments alike. As ransomware locks down critical systems to spyware silently siphoning sensitive information, the impact of malware is both far-reaching and potentially devastating. This blog aims to demystify the concept of malware, delve into its evolution, and...
Footprinting Common Services: Footprinting is a crucial step in the reconnaissance phase of cybersecurity, involving the systematic collection of information about a target system. This process is divided into two primary methods: active and passive reconnaissance. Active reconnaissance involves directly interacting with the target system to gather information, typically through techniques like network scanning, ping...
Introduction Learn about insecure deserialization, a critical cybersecurity concern. In the digital age, data storage and transmission are fundamental aspects of software development. One key process that facilitates these tasks is Deserialization. While deserialization plays a crucial role in handling data, it also introduces significant security risks. This blog post delves into the concept of...
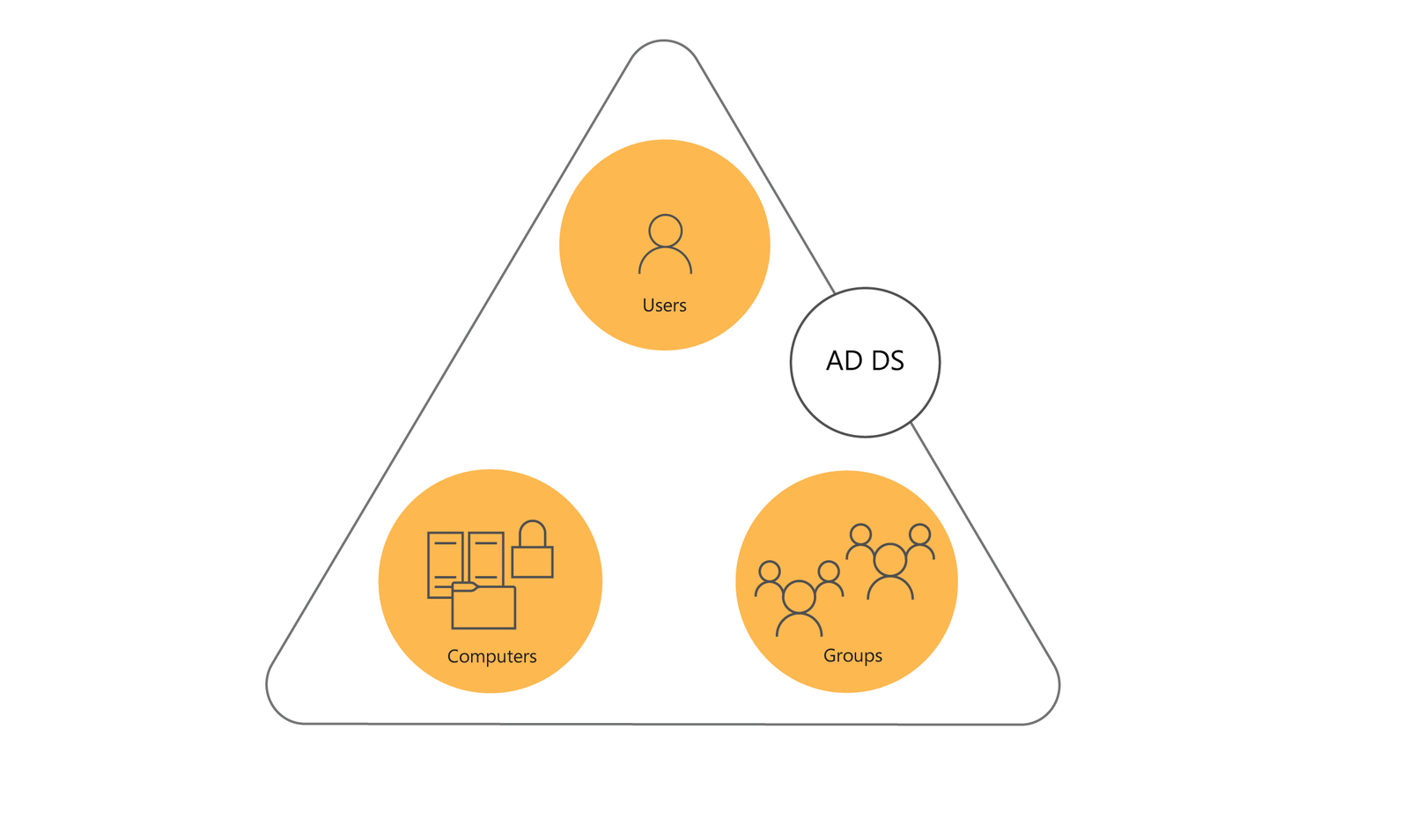
Active Directory A directory is a hierarchical structure that stores information about objects on the network. A directory service, such as Active Directory Domain Services (AD DS), provides the methods for storing directory data and making this data available to network users and administrators. For example, AD DS stores information about user accounts, such as...
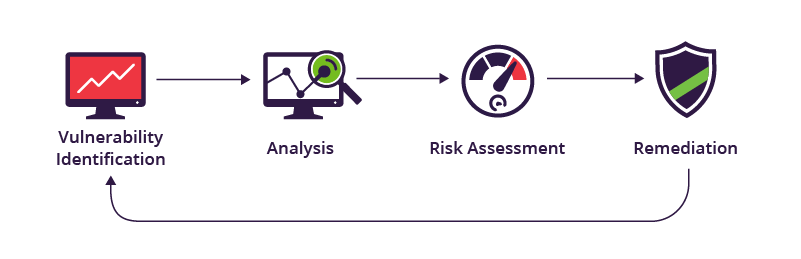
Vulnerability management automation refers to the use of automated tools and processes to identify, assess, prioritize, and remediate security vulnerabilities in IT systems. This approach aims to streamline and enhance the efficiency and effectiveness of vulnerability management programs, reducing the risk of cyber attacks and improving overall security posture. In this blog, we will be...
In this context, this article seeks to demystify two crucial procedures: operational audits and cyber risk quantification. Cybersecurity hazards are becoming serious dangers to businesses of all sizes in the age of digital transformation. Resilience and business continuity depend on an understanding of these risks and effective risk management. We’ll go into great detail about...