What is Single-Factor Authentication (SFA)?
Single-factor authentication involves the use of a single piece of information to verify a user’s identity. Typically, this takes the form of a password. However, relying solely on passwords can be risky, as they can be easily compromised through techniques like phishing or brute-force attacks.
For websites that adopt a password-based login process, users either register for an account themselves or they are assigned an account by an administrator. This account is associated with a unique username and a secret password, which the user enters in a login form to authenticate themselves.
In this scenario, the mere fact that they know the secret password is taken as sufficient proof of the user’s identity. Consequently, the security of the website would be compromised if an attacker is able to either obtain or guess the login credentials of another user.
Attack Surface
Username enumeration
Username enumeration involves an attacker detecting website behavior changes to identify valid usernames. It commonly happens on login pages (via incorrect password attempts) or registration forms (checking for taken usernames). This streamlines brute-force efforts by quickly narrowing down valid usernames.
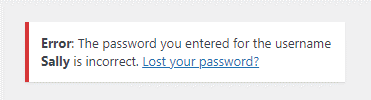
In this case, the username is correct, but the password isn’t.
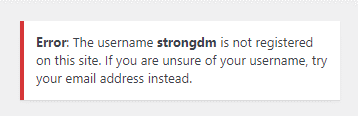
Here, the username is invalid.
The problem with username enumeration is that attackers can tell what usernames are valid. Then, they can try to hack valid user accounts using brute-force techniques without wasting their time and money testing a multitude of invalid account names.
When brute-forcing a login page, watch for variations in:
Status Codes: Check for different HTTP status codes upon guessing. A distinct code suggests a correct username, though websites ideally maintain consistency. For Example: Each request received a response with a 200 status code except for one, which got a 302 response. This suggests that the login attempt was successful.
Error Messages: Differences in error messages may reveal if the username is correct, especially if there are variations for incorrect password versus both incorrect username and password.
Response Times: Deviations in response times can indicate a correct username, as additional steps (like password verification) may affect processing times. Attackers may exploit this by using excessively long passwords to accentuate delays.
Logic Flaw in Rate Limiting
In some systems, repeated failed login attempts trigger an IP block to prevent brute force attacks. However, if the system resets the counter when the legitimate user logs in successfully, attackers can exploit this by inserting their own successful logins into the attack. This tactic, known as “login token” or “successful login evasion,” can render the defense ineffective.
To address this, administrators should consider measures like implementing account lockout durations, monitoring for suspicious activity, enabling multi-factor authentication, using IP whitelisting, and applying rate limiting on login attempts.
To bypass this IP-based rate limiting, attackers can use multiple security headers like X-Forwarded-For and many more.
Logic Flaw in Account Locking
While locking user accounts after repeated failed login attempts offers a level of protection against targeted brute-force attacks on specific accounts, it lacks effectiveness in thwarting brute-force attempts aimed at gaining access to random accounts.
To overcome this protection:
- Create a list of potential usernames, either through methods like username enumeration or by identifying common usernames.
- Select a very limited number of passwords, ensuring that the chosen passwords do not exceed the permitted login attempts (e.g. if the limit is 3 attempts, stick to a maximum of 3 passwords).
- Employ tools such as Burp Intruder to systematically test each selected password with every candidate username. This approach enables the attacker to carry out brute-force attacks on multiple accounts without triggering account locks. Success occurs if any user among the candidates uses one of the chosen passwords, leading to the compromise of the account.
Staying Logged In
A “Remember me” or “Keep me logged in” checkbox beneath a login form makes it super easy to stay logged in after closing a session. It generates a cookie that lets you skip the process of logging in.

However, this can lead to a cookie-based authentication vulnerability if an attacker can predict a cookie or deduce its generation pattern. They can use malicious techniques like brute-force attacks to predict cookies, and cross-site scripting (XSS) to hack user accounts by allowing a malicious server to make use of a legitimate cookie.
If a cookie is poorly designed or protected, attackers may be able to obtain passwords or other sensitive (and legally protected) data such as user addresses or account information from a stored cookie.
Credential Stuffing
Credential stuffing is a cyber-attack where automated tools input stolen username-password pairs, often from data breaches, into various online services. This exploits users who reuse credentials, leading to unauthorized account access, single-factor authentication failures, and security risks. Countermeasures include multi-factor authentication, account lockout policies, and monitoring for unusual login activities.
Unsecure Password Change and Recovery
Sometimes, users forget or just want to change their passwords and click the “Forgot password” or “Lost your password” links.
When resetting a password for your account, you click on forgot password and get a password reset link in your inbox which looks like: http://website.com/reset-password?token=a0ba0d1cb3b63d13822572fcff1a241895d893f659164d4cc550b421ebdd48a8
When the user visits this URL, the system should check whether this token exists on the back-end and, if so, which user’s password it is supposed to reset. Sometimes, there is a hidden parameter that verifies the user based on username to change his/her password. Attacker can change the parameter and use victim’s username and change his password.
To state it simply, we can use our token to change victim’s password by simply manipulating the hidden parameter to victim’s username.
How to Prevent Single-Factor Authentication Vulnerabilities?
While single-factor authentication vulnerabilities are easy to identify, they greatly impact cybersecurity. But, you can prevent them from happening.
Here are eight best practices to prevent single-factor authentication-based vulnerabilities and keep critical information safe.
- Implement a reliable brute-force protection system: Put in place a dependable brute-force defense mechanism. Application firewalls, rate limits, IP-based monitoring, account lockouts, and CAPTCHAs are some ways to stop brute-force attacks.
- Enforce a secure password policy: Implement a secure password policy. To do this, develop a password checker that provides users with a real-time password strength assessment.
- Consider disabling username enumeration: Consider turning off username enumeration. An attacker is forced to brute-force both the set of likely usernames and the set of possible passwords, as opposed to focusing only on the ones they are certain are valid, when you generate the same error for a login failure regardless of the username’s validity.
- Modify cookie headers: Making changes to cookie headers shields them against nefarious attempts. When setting cookie headers, using the HttpOnly and SameSite tags shields them from XSS and CSRF attacks, respectively.
- Implement proper multi-factor authentication: Password-based systems are less secure when using multi-factor authentication. To successfully use this type of authentication, you will need strong code and secure verification code creation.
Conclusion
To sum up, there are several serious vulnerabilities associated with Single-Factor Authentication (SFA), such as credential stuffing, rate limitation and account locking logic errors, username enumeration, cookie-based authentication threats, and insecure password change/recovery processes.
Robust methods including putting in place a trustworthy brute-force protection system, enforcing safe password practices, implementing HTTP tight transport security, blocking username enumeration, altering cookie headers, and putting multi-factor authentication in place are essential for thwarting these threats. Frequent code audits are necessary to find problems with authentication bypass and logical errors, which strengthen cybersecurity and protect sensitive data.





