Introduction: In today’s digital landscape, incident response (IR) has become a cornerstone of any effective cybersecurity strategy. With the frequency and sophistication of cyber threats steadily increasing, organizations must be prepared to respond swiftly and effectively when an attack occurs. Incident response refers to the structured approach an organization takes to prepare for, detect, contain,...
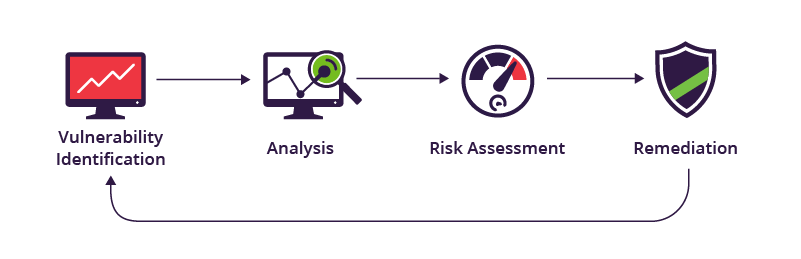
Introduction In today’s hyper-connected world, cybersecurity is no longer a luxury, it’s a necessity. As organizations move more of their operations online, they become prime targets for cyberattacks. Vulnerability management, the process of identifying, evaluating, and mitigating security weaknesses, is crucial to protecting sensitive data and maintaining business continuity. However, traditional methods of vulnerability management...
Introduction Vulnerability management is a critical aspect of cybersecurity that involves identifying, assessing, and mitigating vulnerabilities in an organization’s systems and software. It is essential for protecting sensitive data and ensuring the integrity of IT environments. This process not only helps organizations defend against potential cyber threats but also plays a vital role in maintaining...
Malware is a pervasive threat that impacts individual, businesses, and governments equally in today’s digital environment. Malware can have a variety of potentially lethal effects, such as secretly stealing important data or locking down critical systems with ransomware. This blog seeks to define malware, examine its history, and emphasize the importance of malware analysis in...
Learn how DevSecOps ensures quicker, safer releases by seamlessly integrating security into the software lifecycle, from development to deployment. Security is now an essential component of software development and cannot be ignored in the quickly changing field. Organizations are being forced to reconsider how they incorporate security into their operations due to the increase in...
Introduction Malware analysis is playing a crucial role for safeguarding the digital landscape, guarding individuals, businesses, and governments alike. As ransomware locks down critical systems to spyware silently siphoning sensitive information, the impact of malware is both far-reaching and potentially devastating. This blog aims to demystify the concept of malware, delve into its evolution, and...
Introduction Learn about insecure deserialization, a critical cybersecurity concern. In the digital age, data storage and transmission are fundamental aspects of software development. One key process that facilitates these tasks is Deserialization. While deserialization plays a crucial role in handling data, it also introduces significant security risks. This blog post delves into the concept of...
Vulnerability management automation refers to the use of automated tools and processes to identify, assess, prioritize, and remediate security vulnerabilities in IT systems. This approach aims to streamline and enhance the efficiency and effectiveness of vulnerability management programs, reducing the risk of cyber attacks and improving overall security posture. In this blog, we will be...
Introduction In today’s linked world, where software powers financial transactions, personal communication, and essential infrastructure, the significance of application security automation cannot be emphasized. Data breaches place businesses at significant risk, and cyber threats always change. As such, it is imperative to uphold strong security protocols. To solve the issues that enterprises encounter when managing...
Introduction: Since they provide a practical and effective means of permission and authentication, JSON Web Tokens (JWT) have emerged as a key component of contemporary web application security. JWTs are frequently used to authenticate users and secure web applications because they are a condensed and self-contained method of transferring claims between parties. Generally, the server...