Windows Password Attacks Overview Windows password attacks focus on extracting and cracking stored credentials to gain unauthorized access to systems and networks. Attackers often target the Security Accounts Manager (SAM), LSASS process, and NTDS.dit files. These components store critical data like hashed passwords, cached credentials, and domain account information. By dumping and transferring these files...
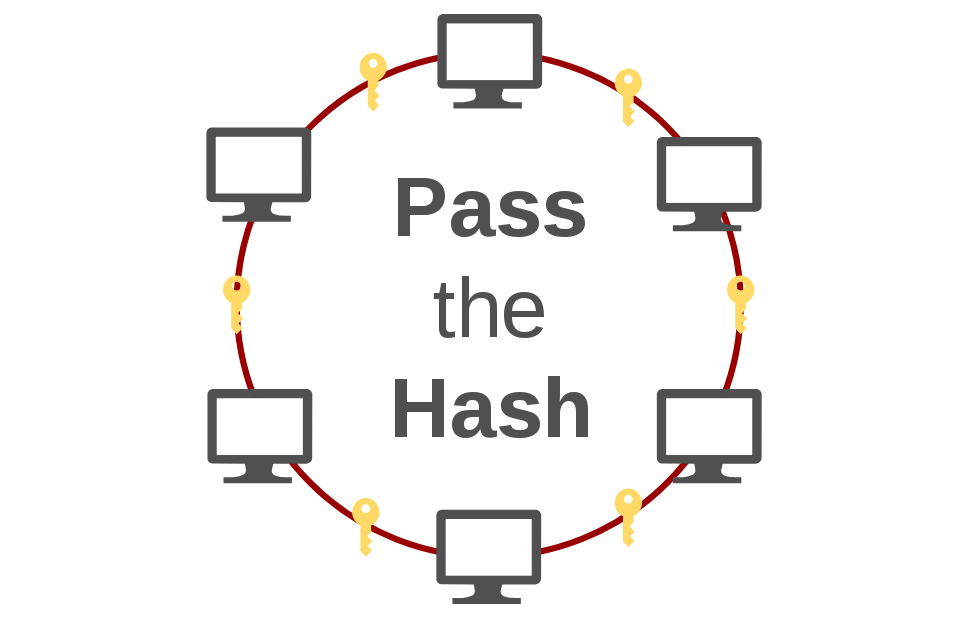
Lateral Movement in AD: Pass the Hash (PtH) One of the most important attacks in Active Directory is Pass the Hash. Pass the Hash (PtH) attack is a technique where an attacker uses a password hash instead of the plain text password for authentication. The attacker doesn’t need to decrypt the hash to obtain a...
Footprinting Common Services: Footprinting is a crucial step in the reconnaissance phase of cybersecurity, involving the systematic collection of information about a target system. This process is divided into two primary methods: active and passive reconnaissance. Active reconnaissance involves directly interacting with the target system to gather information, typically through techniques like network scanning, ping...
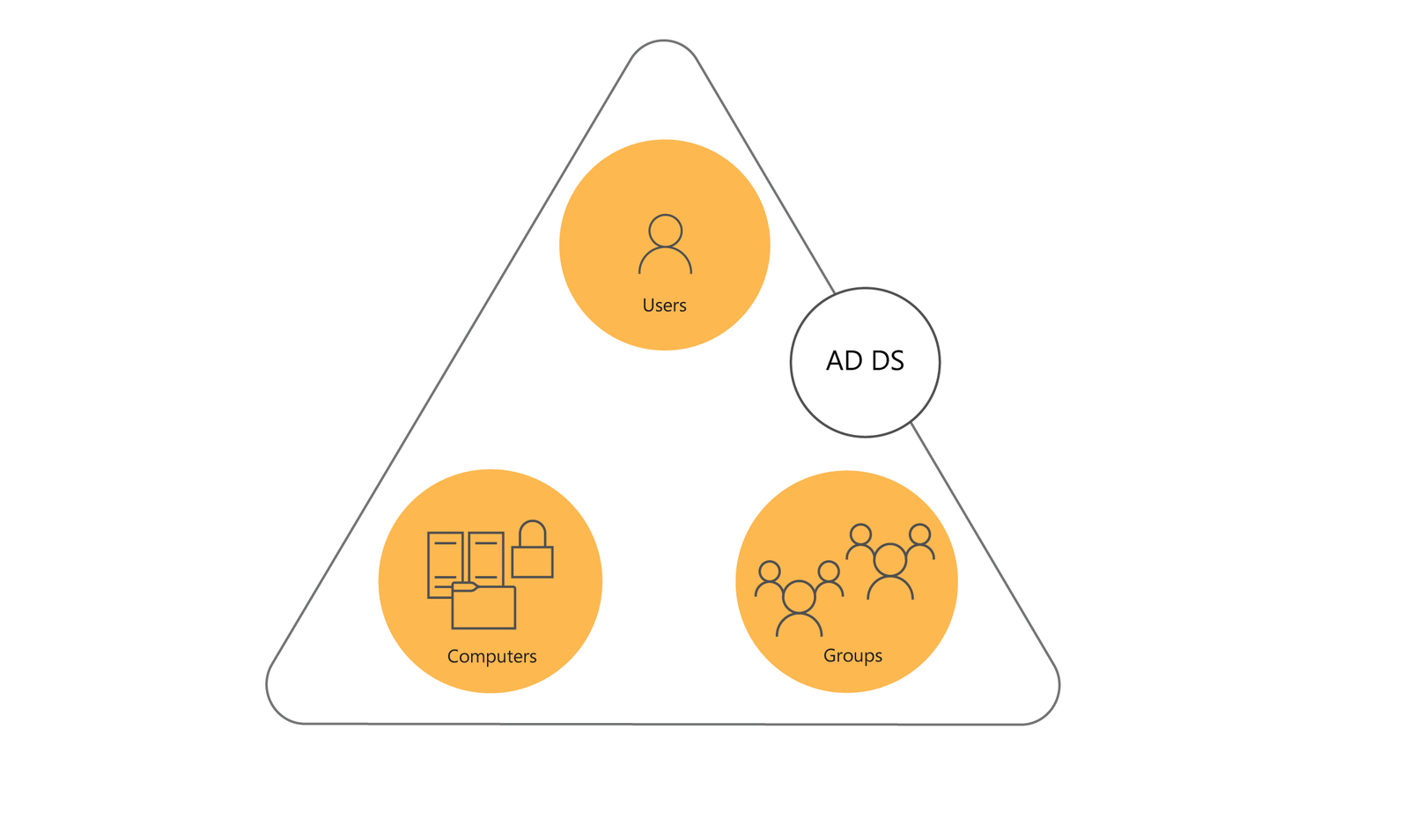
Active Directory A directory is a hierarchical structure that stores information about objects on the network. A directory service, such as Active Directory Domain Services (AD DS), provides the methods for storing directory data and making this data available to network users and administrators. For example, AD DS stores information about user accounts, such as...
Introduction: Since they provide a practical and effective means of permission and authentication, JSON Web Tokens (JWT) have emerged as a key component of contemporary web application security. JWTs are frequently used to authenticate users and secure web applications because they are a condensed and self-contained method of transferring claims between parties. Generally, the server...
What is it? Business logic vulnerabilities are flaws in the design and implementation of an application that allow an attacker to elicit unintended behavior. This potentially enables attackers to manipulate legitimate functionality to achieve a malicious goal. These flaws are generally the result of failing to anticipate unusual application states that may occur and, consequently,...
When it comes to site security, file upload functionality can be very dangerous if not used and maintained correctly. This essay will examine several kinds of file upload vulnerabilities, examine actual attack scenarios, and go over practical mitigation techniques. What vulnerabilities exist in file uploads? Vulnerabilities related to file uploads occur when a web server...
The vulnerability management lifecycle serves as a robust framework, guiding organizations through the identification, analysis, and mitigation of potential security risks. Additionally, understanding where vulnerability analysis fits into the disaster management cycle is crucial for a comprehensive approach to cybersecurity. In the ever-evolving landscape of cybersecurity, organizations face a constant barrage of potential threats. Effectively...
A significant concern among the numerous risks that web applications face is session vulnerabilities. This blog will look at the definition, implications, and proactive measures of session fixation in order to effectively defend against such attacks. Session fixation is a significant security vulnerability that attackers utilise to access user sessions. By tricking a user into...
What is it? SQL injection is a type of security exploit where an attacker injects malicious SQL code into a vulnerable application’s database query, in order to gain unauthorized access to sensitive information or perform malicious actions. In simpler terms, it’s a technique that hackers use to manipulate a database by inserting malicious SQL statements...