What is Multi-factor authentication (MFA)? Multi-factor authentication is an identity and access management security method that requires two forms of identification to access resources and data. MFA gives businesses the ability to monitor and help safeguard their most vulnerable information and networks. Importance of Multi-factor authentication MFA stands for multi-factor authentication. It is used as...
Hey there! Did you catch wind of the latest scoop? Mandatory Internal Compliance Monitoring Update for Financial Institutions. Circular RBI/2023-2024/117 of the Reserve Bank of India (RBI) is shaking things up, suggesting it’s time for a tech upgrade in compliance. Let’s break down what this means and how it can work wonders for your organization. According...
What is Single-Factor Authentication (SFA)? Single-factor authentication involves the use of a single piece of information to verify a user’s identity. Typically, this takes the form of a password. However, relying solely on passwords can be risky, as they can be easily compromised through techniques like phishing or brute-force attacks. For websites that adopt a...
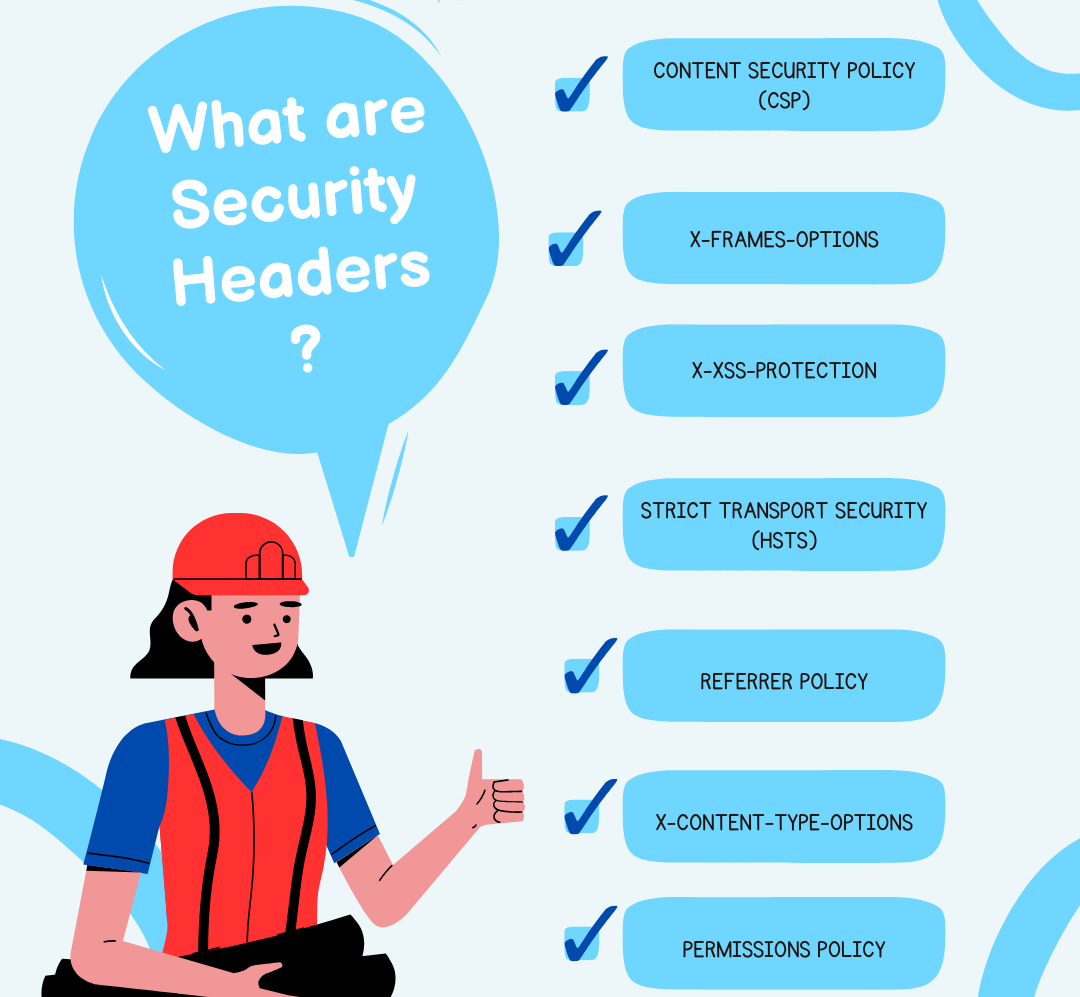
In the dynamic world of web security, where cyber threats are a major issue and evolving rapidly, the implementation of security headers plays a vital role in this web application world. Security Headers are HTTP response headers that provide an additional layer of protection against various types of attacks. Let’s delve into the essence of...
Introduction The OWASP (Open Web Application Security Project) Top 10 Mobile report identifies a critical concern: Insufficient Cryptography. This blog will delve into the nuances of insufficient cryptography, shed light on the associated risks, and provide insights into effective strategies for responding to this paramount security challenge. Understanding Insufficient Cryptography Cryptography’s Crucial Role: Cryptography is...
Introduction The OWASP (Open Web Application Security Project) Top 10 Mobile report underscores a prevalent threat: Insecure Data Storage. In the realm of mobile applications, the security of stored data is paramount. This blog will dissect the intricacies of insecure data storage, elucidate the risks it poses, and delineate effective strategies for response to this...
Introduction Security misconfiguration, as highlighted in the OWASP (Open Web Application Security Project) Top 10 Mobile, stands as a significant threat to the integrity and safety of mobile applications. In this exploration, we will unravel the complexities of security misconfiguration, decipher its implications, and chart a course for effective responses to this pervasive challenge. This...
Introduction The OWASP (Open Web Application Security Project) Top 10 Mobile report has highlighted a critical vulnerability: Insufficient Binary Protections. Mobile applications, being the digital backbone of our daily lives, store and process vast amounts of sensitive information. To understand this threat, let’s unravel what exactly insufficient binary protections entail. What is Insufficient Binary Protections?...
In the dynamic realm of mobile application security, the peril of insecure communication has surfaced as a critical concern. Ranked fifth in the OWASP Mobile Top 10 for 2023, insecure communication poses a significant risk to user data and overall app integrity. In this blog, we will delve into the nuances of insecure communication, explore...
Introduction In the 2023 edition of the OWASP Mobile Top 10, Insufficient Input/Output Validation secured the 4th position. This blog aims to shed light on the implications of this vulnerability, explore a real-world example, and discuss effective mitigation techniques to safeguard mobile applications. In the ever-evolving landscape of cybersecurity, mobile applications are becoming an integral...