The advent of technology has brought about new ways for cybercriminals to exploit the vulnerabilities that exist in our networks and systems. That is why, according to OWASP, “the world needs a robust set of guidelines to help organizations mitigate these risks.”
Introduction
The Open Web Application Security Project (OWASP) is a worldwide not-for-profit organization dedicated to improving the security of software. Our mission is to make software security visible so that individuals and organizations can make informed decisions about true software security risks.
The latest OWASP Top 10 is not a comprehensive list of all possible attacks, but rather a prioritized list of attack vectors that present the greatest risk to web applications today. Understanding and mitigating these risks is critical to securing your web application.
Top 10 Vulnerabilities in 2021
- A01:2021-Broken-Access control
- A02:2021-Cryptographic Failures
- A03:2021-Injection
- A04:2021-Insecure Design
- A05:2021-Security Misconfiguration
- A06:2021-Vulnerable and Outdated Components
- A07:2021-Identification and Authentication Failures
- A08:2021-Software and Data Integrity Failures
- A09:2021-Security Logging and Monitoring Failures
- A10:2021-Server-Side Request Forgery
What is the OWASP Top Ten Project?
OWASP’s Top Ten attacks are categorized according to their frequency on the web. It has been compiled by the Open Web Application Security Project, an international organization dedicated to improving software security. The OWASP Top Ten is released every three years, and the most recent version was published in 2017.
The OWASP Top Ten is designed to be a reminder for developers and system administrators of the importance of security. It also provides a common language that can be used to discuss web application security risks. The OWASP Top Ten is not a silver bullet, but it is a good starting point for organizations to identify and prioritize the risks that they face.
Benefits of the project
The OWASP Top Ten benefits include the following:
Enhanced awareness:
The OWASP Top Ten can help to raise awareness of web security issues within an organization.
Reduced risk of attack:
Organizations can reduce their risk of attack by understanding the most common attacks.
Greater peace of mind:
Knowing that your organization is taking steps to protect itself against common attacks can give you greater peace of mind.
Improved security posture:
Implementing the recommendations of the OWASP Top Ten can help organizations to improve their overall security posture.
OWASP top ten vulnerabilities for 2021: A brief overview
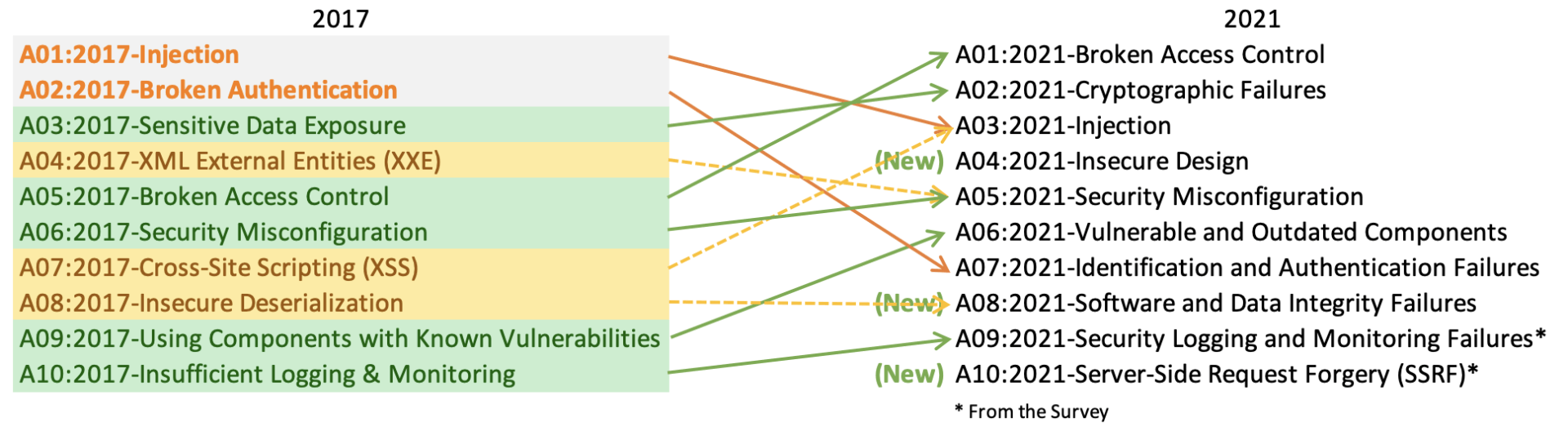
In the OWASP Top Ten, the most common web attacks are classified. It has been updated for 2021, with changes to the categories and entries.
A01: 2021 – Broken Access Control
The OWASP 2021 list has ranked broken access control as the number 1 problem, moving up from the number 5 spot.
A02:2021 – Cryptographic Failures
Formerly known as A03:2017 – Sensitive Data exposure, this vulnerability has also gained a place in 2021’s list. The renewed name majorly focuses on the failures related to cryptography, leading to sensitive data being exposed.
A03:2021 – Injection
Previously on the top list, this vulnerability slides down to the third position and cross-site scripting has been made part of this vulnerability. Applications vulnerable to this vulnerability are impacted by the invalid data injected by an attacker into the application in order to perform unauthorized actions.
A04:2021 – Insecure Design
A new category of vulnerability was introduced in the 2021 list that focuses on risks related to design flaws. We need more threat modeling, safe design patterns and principles, and reference architectures if we truly want to “go left” as an industry. A flawed design cannot be repaired by a flawless implementation since necessary security safeguards were never established to defend against specific threats.
A05:2021 – Security Misconfiguration
We moved up from 6th place last year. It’s no surprise that this category is on the rise as we move towards highly configurable software. Categories before A4: 2017-XML External Entities (XXE) are now part of this risk category.
A06:2021 – Vulnerable and Outdated Components
This category rises from ninth in 2017 and is a well-known concern that we struggle to evaluate and quantify risk. This vulnerability was formerly titled using components with Known Vulnerabilities and is ranked second in the Top 10 community survey of OWASP.
A07:2021-Identification and Authentication Failures
Formerly called Broken Authentication, this has slipped from the second position and now includes CWE related to identification errors. There seems to be a positive impact from the increased availability of standardized frameworks.
A08:2021-Software and Data Integrity Failures
It’s a new category for 2021 that focuses on making assumptions about software updates, vital data, and CI/CD pipelines without confirming their integrity. A8:2017-Insecure Deserialization has been added to this category.
A09:2021-Security Logging and Monitoring Failures
Previously known as A10:2017-Insufficient Logging & Monitoring. This category has been expanded to include more types of errors, that are harder to test, and are not well represented in CVE/CVSS data. However, failures in this category can directly impact visibility, incident alerts, and forensics.
A10:2021-Server-Side Request Forgery
A new category this year, Server Side Request Forgery (SSRF) can occur when a web application requests a remote resource without validating a user-provided URL. The increasing complexity of cloud services and architectures has increased the severity and frequency of SSRF attacks.
OWASP top 10 2021 – Conclusion
Most categories of OWASP Top 10 can be covered by adopting a wholesome web application security strategy. Scanning is not enough, and it is recommended to include penetration testing and monitoring of the security procedures.
It is recommended to businesses that they reach out to MSSPs for detailed security protection and monitoring. This way you can be sure that you have someone who will keep a watchful eye on everything that cannot be found automatically and cover everything that can be found automatically.





